Difference between KYC and AML

The growing Fintech industry leads to an increased demand for KYC and AML compliance requirements. Financial institutions face high-risk frauds through the customers and financial transactions. KYC and AML compliance programs build a systematic review of the secure financial system. Customer verification procedures, Know Your Customer and Anti-money Laundering screen customers against possible fraud risks.
The need for KYC and AML compliance has become mandatory to comply with the global and local regulations. The ones who fail to do so, are subjected to harsh regulatory penalties. To avoid fines, businesses should identify the underlying company standards and the need for KYC and AML compliance in the business framework. Before this, there should be clear understanding of how KYC and AML are different from each other.
What is meant by Know Your Customer (KYC)?
KYC refers to a need for understanding clientele, monitor financial transactions, and figure out the potential risks associated with customers towards business relationships.
Know Your Customer is defined as a process that verifies the identity of customers. Customers are required to provide personal information which includes name, address, contact information, id card, etc. This information is verified before they become part of a business or company. The term KYC is commonly referred for financial institutions. This is because the finance industry is prone to high-risk frauds that vary from money laundering and terrorist financing to identity theft and data breaches.
The scope of KYC enlarges and takes in all the Fintech companies that provide financial services to customers. Online businesses that are under threat of a large number of financial frauds also lie into this cluster. KYC compliance has become mandatory whose non-compliance can result in businesses in the hefty monetary and reputational loss.
KYC Incorporates CDD AND EDD
Know Your Customer demonstrates customer verification which ultimately refers to the processes of Customer Due Diligence (CDD). Financial institutions verify the information of clients to make sure that they are building a secure relationship with them. Financial middlemen are supposed to undergo a CDD process to authenticate customer traffic and ensure their incorruptibility. In CDD, ascertain the identity of customers and verify the name and address. After authenticating, identify the risks before making an entity part of the system.
Enhanced Due Diligence (EDD) on the other hand, gathers additional information from customers. EDD came into force with the declaration of the USA Patriot Act. The difference between CDD and EDD should be clear to map the business standards and needs accordingly. Periodic due diligence processes on the customer are highly beneficial to deter the risks that could be generated by an entity later.
EDD regulations are more efficient because of the extra information and proof it gathers from the customer. Detailed documentation is done for the whole EDD process and regulators are provided with the gathered information. EDD information includes;
- Geographical factors
- Property and assets information
- Transactions types
- Occupation information
- Banking information
What is meant by Anti-money Laundering (AML)?
Anti-money laundering is a term that is used in Financial Institutions (FIs). It describes legal controls according to which FIs and other regulatory entities are supposed to take in place actions to detect and prevent money laundering activities.
AML procedures detect suspicious transactions happening in the financial system. Entities are investigated and thorough documentation takes place that reveals malevolent entity beforehand. Criminal activity is accelerated when laundered money is used. By breaking that cash flow, a large number of criminal operations can be terminated. For this, a company must first verify the identity but do not stick to it. Continuous transaction monitoring should be done to identify the risky entity before some ruinous situation takes place.
Global and local regulators are all set up to evaluate the AML standards of businesses. Regulations are declared to which states are supposed to comply strictly. Otherwise, it could lead to heavy regulatory punishments. AML regulations intend to eliminate the incidences of money laundering and terrorist financing. Businesses across the world are evaluated with respect to in-house AML techniques and procedures. This is done to make sure that no individual is facilitated to launder money through some industry or business (knowingly or unknowingly). An overall assessment takes place by global regulators that evaluate the AML norms of countries and present amendments accordingly.
AML Procedures
The AML framework keeps on updating with the pace of fraudulent activities. Rules and regulations change with time. Following are the steps that help businesses comply with the AML regulations and standards:
Step#1 Stay updated with the changing AML rules and regulations
On a continuous basis, keep on reviewing the company norms and improve them accordingly.
Step#2 Know Your Customer
KYC is a part of AML compliance. It is necessary to know who you are facilitating with your services and how in return your customer will be.
Step#3 Identify the external and internal risks
It is necessary for companies to identify the high-risks associated with the business. Identify the vendors, third parties and customers.
Elaboration: Difference between KYC and AML
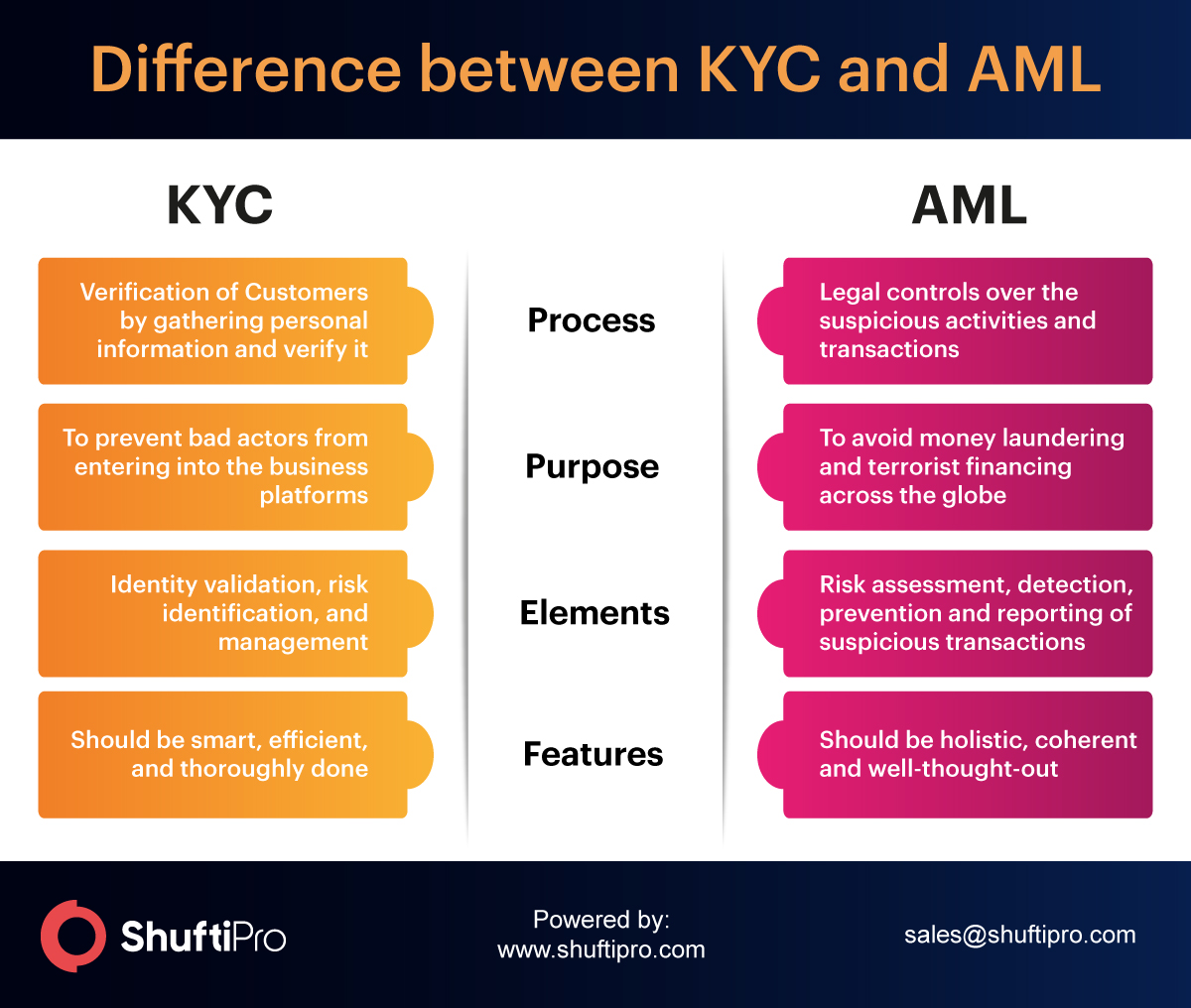
AML procedures contribute to avoiding money laundering and terrorist financing activities. KYC, on the other hand, is the process of gathering customer verification on the basis of gathered information. It is necessary to consider both simultaneously. A business that complies with both KYC and AML regimes is considered well-reputed and trustworthy. The reason is that the chances of fraud are reduced when a company takes in place stringent actions and steps for fraud prevention.











