How identity verification can help prevent Medical Identity Theft?

Digitization is reshaping the future of healthcare. With the healthcare industry, having more resources at their disposal, medical treatment is becoming more accessible to patients irrespective of the location. But this exponential growth has also given way to technical crises and predicaments one of which is Medical Identity Theft. Medical Identity Theft is becoming increasingly popular in this age of digitization. Identity thieves are targeting medical records without any hesitation and the number of cases continues to grow each day, affecting the healthcare sector on a much larger scale. Problems as such insist on innovative digital identity verification solutions. Speaking of which, in this day and age, many online systems are vulnerable to and defenseless against massive data breaches.
Let’s look into what Medical Identity Theft actually looks like, the damages it can cause if go unnoticed, and how to prevent it.
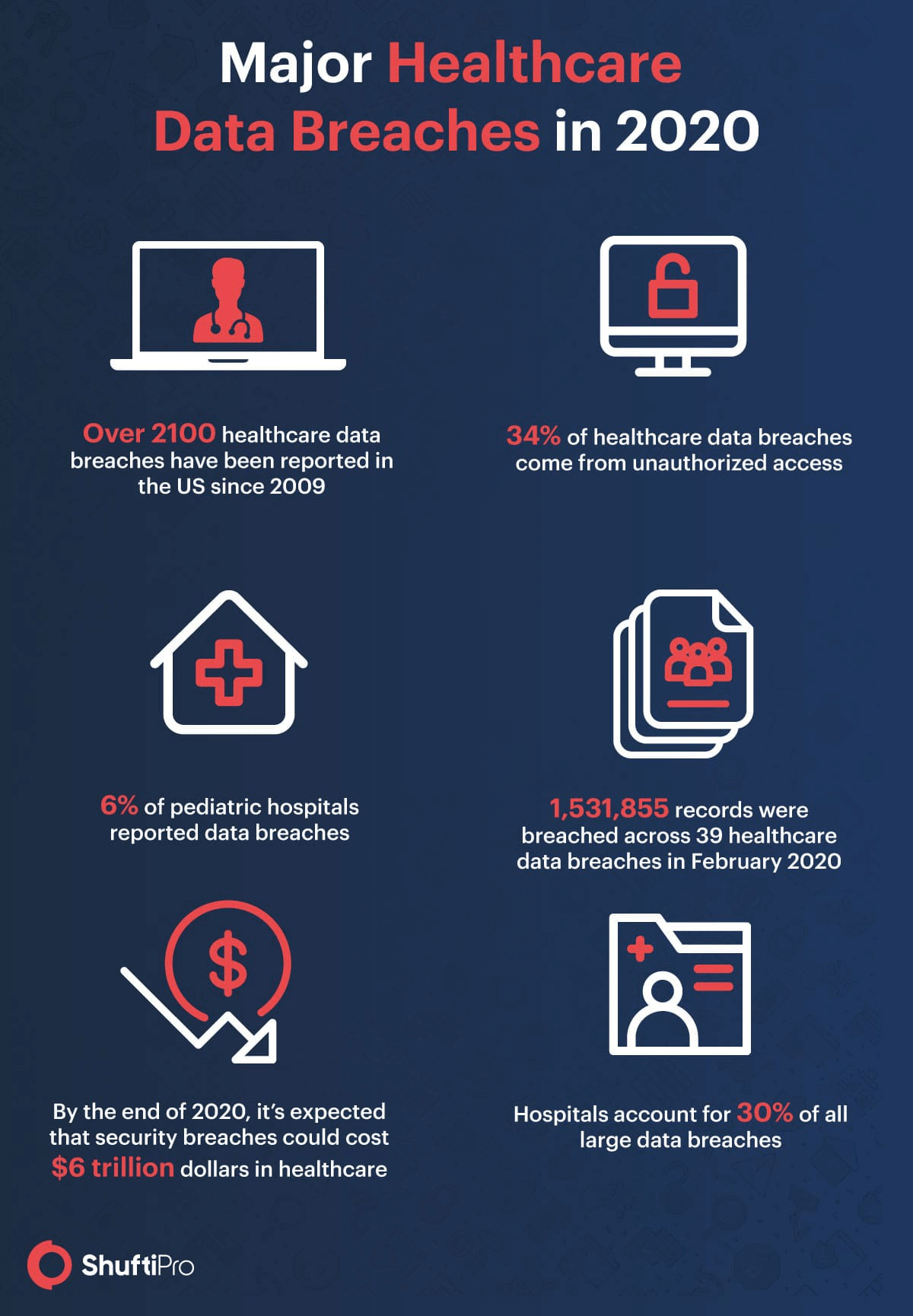
These breaches are not limited to the corporate world but the health care sector has been greatly impacted as well.
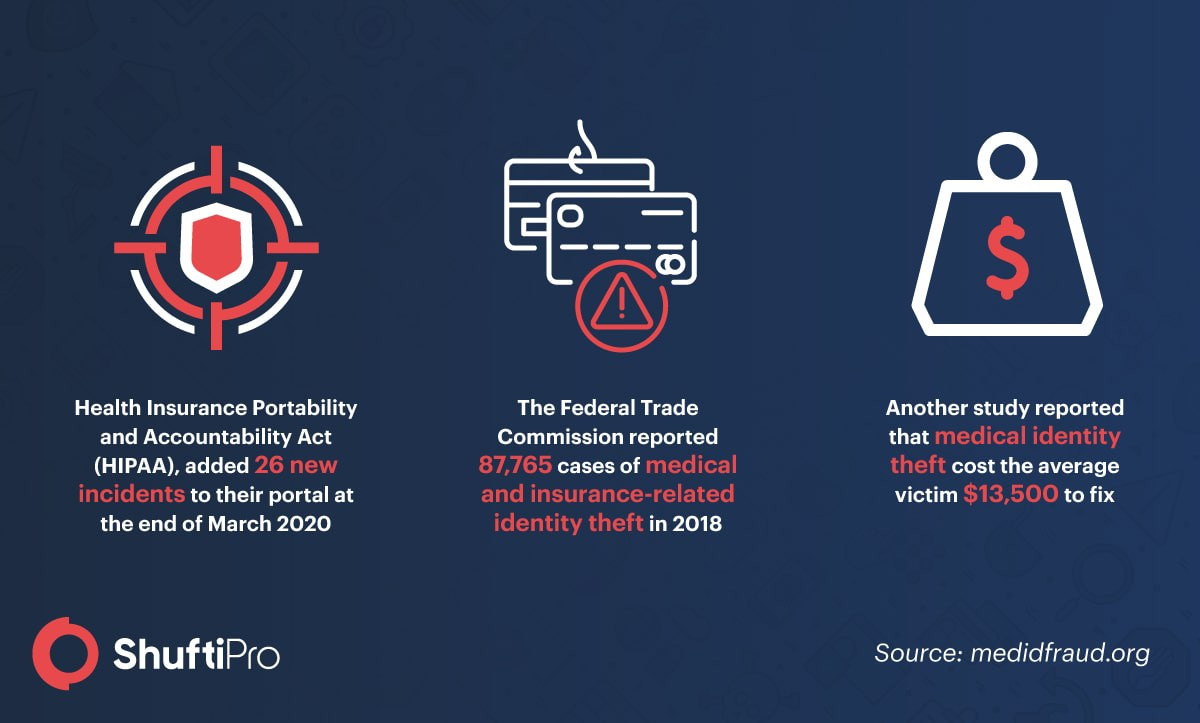
Medical identity theft has always been there, which is pretty evident from the numbers given above, and can have more detrimental effects than the usual identity theft. Here fraudsters use the healthcare information of patients to get expensive medical services, and the aftermath is in the form of millions that can take eons to fix and settle.
To get more information about compliance and Identity verification, get in touch with us.
What is Medical Identity Theft?
Medical identity theft is considered a healthcare fraud that transpires when someone steals medical and personal information of patients to get medical treatments or prescriptions. Not only this, but they can also use that information to make false claims to insurance providers to obtain medical reimbursements or fictitious medical services from government healthcare programs.
Medical identity theft may not be in the spotlight but it is a growing threat that can have some serious consequences on hospitals, insurance firms, victims and not to mention the considerable financial losses. All it needs for the crime to take place is the patient’s personally identifiable information and/ or personal health information such as your social security number, mailing address, name, medical record, prescription history, and other pieces of information that identify you as a specific individual.

What are some of the types of Medical Identity Theft?
Healthcare is expensive around the globe especially in the US but it affects everyone equally as it strains the budget of individuals and taxpayers all the same. Healthcare costs continue to rise and account for almost 90% of the spending in the US alone. However, everyone has access to health insurance to cover the costs.
Undergoing free medical care: Keeping in view the expensive medical services, now just imagine the damage online medical frauds can do to the community. Using a patient’s health insurance number, fraudsters can get free treatment from practitioners at a number of hospitals either undergoing major surgery or getting a prescription they don’t even qualify for or just making claims for the medical care they might not even need just for the sake of receiving reimbursements by fabricating medical records.
Healthcare industry and black market: Fraudsters can pose as patients and use insurance to get expensive medical equipment, only to sell the equipment on the black market. On the other hand, PHI is worth a great deal of money on the black market because it can be used to procure pharmaceuticals, pull off insurance frauds, or obtain government healthcare programs like Medicaid and Medicare.
No access to health coverage: Patients can lose their health coverage due to these imposters. They can exhaust their health benefits (which were initially in place for the patients). As a result, it can put the patient’s health in jeopardy when they actually need medical attention in case of emergencies.
The world’s privacy forum published the first-ever major report about the crime of medical identity theft in 2006 and its implications on patients as well as hospitals.
Insider threats: Surprisingly sometimes the perpetrators work within the healthcare sector. They are well aware of the insurance billing system enough to charge your bill for inflated claims to treatments you never received.
Prescription drugs: Here thieves can use patient’s health insurance to obtain restricted or otherwise prescribed medications in order to feed into their addiction or for treatment. According to a Consumer Reports article, in 2006 a woman was allegedly arrested for buying 1,700 opioid painkiller pills on prescription. Someone stole her purse and her wallet according to the story. The charges were dissolved after she filed a report, still, it took her almost 7 years to clear her name.
Government Healthcare: False use of identity to get government health benefits which they otherwise don’t deserve.
How Medical Identity theft can affect patients and businesses?
The repercussions of Medical identity theft to consumers and businesses are acute.
An estimated 1.4M Americans were victims of medical identity theft in 2009 which is the only 5% of reported incidents, according to experian.
Whether its plain identity theft or medical identity theft specifically, it takes time to resolve. Oftentimes it can not be identified which makes it extremely dangerous. Other times victims don’t even realize that they were the victims of such a menace until after it’s too late. Which in return can leave negative footprints on not only patients but the healthcare industry as a whole.
Negative Outcomes on Patients: 40% of customers say that they have no idea that their information is compromised until after they receive a medical bill for services they didn’t get or when they hear from a debt collector about a medical debt they were unaware of. Sometimes the victims have to pay for the damages out of their own pockets to make up for the losses.
Negative Outcomes on Businesses: The impact of such a breach is as detrimental to businesses as it is to consumers. According to Ponemon Institute research, the average cost for a company to address a medical data breach is $211 per record. On top of that, the companies that fail to comply with the HITECH Act may have to pay $1.5M in fines.
Damages go beyond just financial losses and fines. It also ruins the industry relationships including trust and is damaging to the overall business reputation.
How Identity Verification can help prevent Medical Identity Theft?
Medical identity theft is preventable. Therefore, some studies and practical implementations have shown how identity verification can solve this problem. To prevent healthcare data breaches and medical identity thefts, hospitals need to have adequate and digitized identity verification solutions in place that provide a comprehensive patient screening process, known as ‘Know your Patient or KYP’. This will reduce the risk of medical identity theft that is negatively impacting the revenue cycle of hospitals, patient privacy, customer experience and onboarding.
To prevent medical identity thefts by authenticating patients, healthcare institutions can use a biometric identification system. Opting for an online identity verification system during the early stages of patient onboarding has some really convincing advantages.
Healthcare fraud prevention: Online identity verification can seamlessly help with medical identity theft and healthcare fraud prevention as it uses ID document verification to identify and verify a patient. More so, a complete ID verification solution not only relies on document verification using OCR to fight insurance frauds but a mixture of facial recognition features through liveness detection, and consent verification to ensure that the patient is who he says he is and not impersonated by mere imposters. Moreover, as telehealth continues to develop gradually, ID verification and biometric authentication can effortlessly verify the identity of patients while providing services online. These processes are not only crucial for quick and safe patient onboarding but also improves consumer satisfaction.
Healthcare Compliance: Fortunately, there are many healthcare regulations that basically lay the standards of data protection such as KYP/ AML compliance. HITECH and HIPAA compliance sets forth the policies and procedures to address online security in the healthcare industry. Failure to comply with these regulations may incur penalties on the industry. Patient screening through AML regulations can help healthcare institutions to run background checks on new patients against AML watchlists to ensure that the patients do qualify for the said treatment. Which can save them from future medical identity theft incidents and data breaches.
Swift user onboarding: In most cases, online identity verification is performed during patient onboarding, meaning when they create their online accounts on the hospital portal. This instantly captures its data in real-time for online verification in seconds to be able to efficiently deliver patient care. Verification of government-issued ID document, or health insurance cards upon onboarding facilitates smoother processing of payments and/or insurance claims.
Protecting a patient’s data: Online identity verification effectively protects the patient’s medical records by eliminating the risk of medical identity theft. Using strict security protocols such as anti-virus and malware alone isn’t enough. The healthcare sector needs a proper ID verification solution in place to ensure that the patient isn’t posing as an imposter. Hospitals can achieve this through enhanced KYC.
Conclusion
Patient identification solutions can protect the healthcare sector from online frauds, possible data breaches, medical identity theft, and non-compliance penalties. Verifying age can provide prescription-only pharmaceuticals, document verification can prevent false insurance claims, facial recognition can catch identity theft and biometric authentication can help prevent unauthorized medical account access. The innovations in ID verification solutions are outstanding. This paradigm shift from manual paper-based solutions to automated online verification solutions continues to solve many problems for businesses around the globe.
Shufti pro offers AI based cost-effective identity verification services to the healthcare sector for patient verification.
Find more relevant resources:
How identity verification can help prevent Medical Identity Theft?
Get 7 days free trial today, to prevent medical identity theft.











