Data Breaches in 2019 – A Year in Review

Stepping into 2020, the year 2019 has been on the rollercoaster in terms of security breaches. Data breaches continue to make headlines all across the globe. And with every passing year, there has been a significant increase in the numbers. No matter what the size of an organization is, no business is too small or large to fall victim to a data breach.
Every industry whether healthcare, financial or e-commerce, is equally immune to threats and attacks. The increased security breaches make it evident that attackers are able to circumvent the defensive measures put in place. Entering into the fourth industrial revolution, data is the new currency. Regardless of the type of organizational data, it is always useful for the attackers.
Factors Fueling Data Breaches
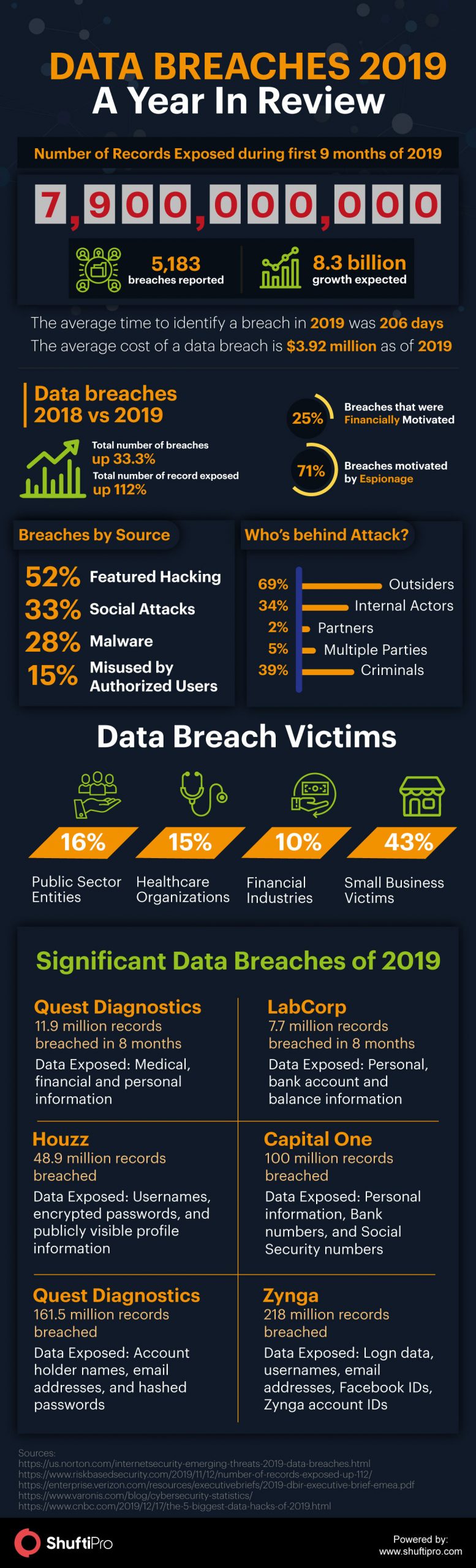
To say the year 2019 has been a year of data breaches won’t be an understatement. During the first nine months of 2019, around 7.9 billion records have been compromised according to Risk-based Security Reseach and are expected to be 8.5 billion in the whole year. As per statistics, these numbers are up 112% as compared to mid-year 2018.
The data exposed included the personally identified information (PII), email addresses, passwords, bank account information, social security numbers, etc. This increased ratio of data breaches is raising serious concerns for businesses. It is important to know what’s causing the rise in data breaches. Here are the core three drivers
1. Excess Information to Steal
When a robber was asked why he robbed a bank, the reply was “because that’s where the money is.” The same is the situation with increased data breaches; since there’s more information to steal. Living in the digital era, businesses actively rely on cloud technology and data banks to conduct business operations and store valuable information.
The stored information not only includes business data but also the consumers’ information. This data holds a crucial value in the digital world, not in just terms of personalized marketing. In fact, the consumers’ data is sold on the dark web for criminal and fraudulent gains. To access this data, hackers and cybercriminals are extensively working hence resulting in data breaches.
2. Technology Facilitates Hacking
While the advancement of technology is shaping the business industry, it is also being misused by the bad boys out there. Technological innovations have made it easier for hackers to use specialized hacking tools to target businesses and individuals. Through automated attacks, for instance, brute force attacks, keylogging, dictionary attacks, etc., hackers are getting successful in breaking into the businesses and gathering the valuable data stored.
The exploited data often leaves the victims vulnerable to identity theft, account takeovers and other digital frauds. Moreover, the business’ reputation is ruined and they fall under strict regulations hence held liable for compliance violations.
3. The Crime of Opportunity
Hacking and data breaches often considered as the crime of opportunity because of people being careless about security. Upon investigation of the breaches, multiple reports highlight the slack handling of data and inefficient security practices as the core reasons for data breaches.
While the attacks on renowned and large cooperations are disclosed and receive media coverage, the small organizations are often ignored. It makes the smaller businesses to be under greater risks because even they contain more valuable data yet have poor security measure than large firms.
Tips to Prevent Data Breaches
Considering the above mentioned first two drivers, there is nothing much business could do. Abandoning the technology to go back in time is not possible right? But what you can do is just take some precautionary measures, follow security practices and consider technology solutions to reduce the vulnerability and threat to attackers. Some of them are:
Update your Software
Non-updated software can prove to be fatal for an organization because it opens up backdoors for hackers to exploit the system. Make sure all of your software are always up to date and protected. Sometimes, the new updates contain the latest patches to protect possible threats and address the previous loopholes. Hence, it’s important to install updates timely. The failure to do so can make your operating system vulnerable to data breaches and other malicious viruses.
Practice Advanced Authentication Methods
Passwords have always been the primary line of defense against hacking. But the technological advancements have made passwords an inefficient authentication method. Through phishing and brute force attacks, breaking a password is no more of a difficult task. Businesses need to pay attention to their authentication checks. Most of the time, data breaches are influenced by a company insider.
Integrating the advanced authentication checks such as AI-powered face verification and ID verification can protect unauthorized access to the companies data.
Educate your Employees
According to IBM, the average time to recognize a data breach in 2019 was 206 days. The reason is the lack of awareness among the company employees. Businesses need to educate their employees about online threats and how to protect themselves in the digital world. Moreover, it is the duty of organizations to ensure that their employees clearly understand the practices hackers use to trick the employees and target companies, so that they can recognize signs of a data breach at initial stages.
Set Security Policies
The well-designed company policies are essential for the success of any business. While we are talking about data breaches, the company’s security policies must be put in place that must be made mandatory for every employee to follow. For instance, since many employees use personal mobile phones at their work station, the security guidelines for the usage of devices can be set.











