Why 2 Factor Authentication is vital for Online Identity Risk Management?

Online identity risk management is becoming harder and harder on cyberspace. It is a headache for not only individual users but corporations are equally worried about the potential fallout from online identity theft and digital fraud. It is estimated that in the year 2017, only in the USA 16.7 million people became victims of identity frauds. The financial cost of such a systemized attack on online user identities is estimated to be USD 16.8 billion.
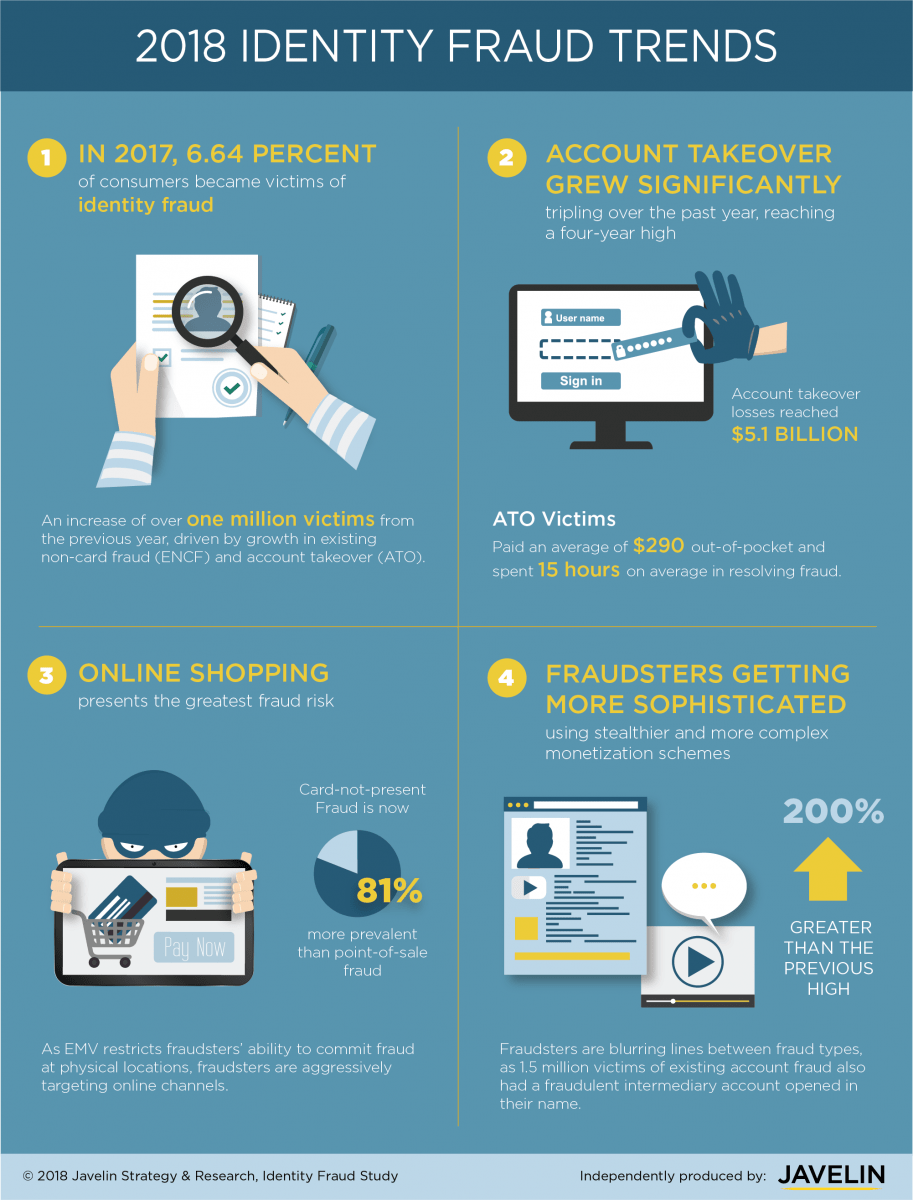
Infographic Credits: Javelin Strategy
Given the careless practices adopted by the majority of individuals when it comes to passwords and security on internet platforms, the above-displayed stats are not much of a surprise. 2 Factor Authentication is a tried and tested method for online identity theft protection and digital fraud prevention. Not only individual users but the employees of large businesses are responsible as well for continuous identity theft and unauthorized access to crucial customer information. Although many companies have adopted data security practices involving 2-factor authentication as a mandatory method of accessing sensitive information, there are still many who have not realized the importance of 2 FA as identity risk management solution. They still relay over outdated methods of user verification and login services protected by customized passwords. But we have a bad news for such businesses and executives who are not willing to utilize identity verification services
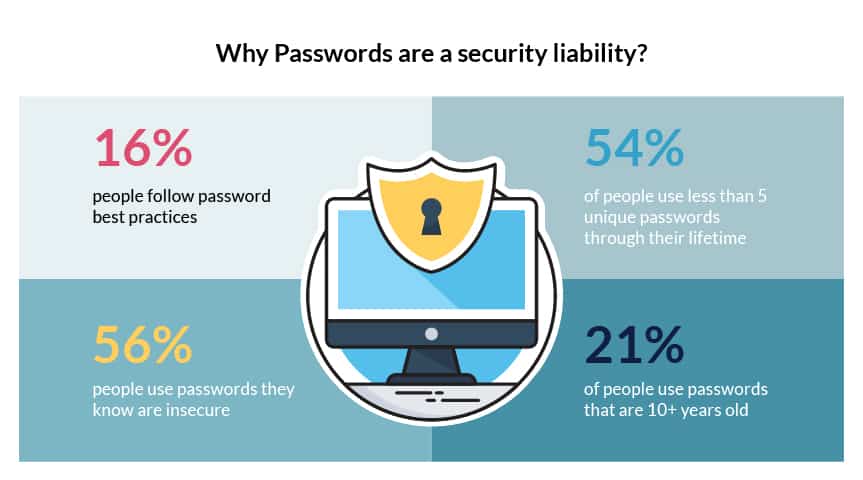
Passwords are no Longer Secure
Ordinary passwords are no longer regarded as the sole defense shield standing between a data hacker and a centralized resource. All the major companies have turned towards 2 step verification to mitigate online identity theft risks whether it is Facebook, Google or Pinterest. Businesses and corporations, on the other hand, have adopted stricter versions of two-factor authentication and made their employees follow those rules. There are many KYC verification and ID verification solutions that are offering 2 Factor authentication to its customers as an added layer of security, but most of them fail at recognizing the urgency required in the process. Shufti has developed its two factor authentication solution that is not only secure but robust as well. Full-scale identity verification can be achieved by Shufti customers using its advanced KYC check via phone verification.
Social media websites and online payment systems are mostly blamed as a major force behind heightened risk to online identities of users, with 2 Factor Authentication being presented as a viable solution against frequent identity theft complaints. Frequent data breaches and dark web-based black markets for personal information have surely established a toxic yet highly stable system of supply and demand. Shufti ensures that personal information of users, including their phone numbers that were collected for performing 2-factor authentication, are fully secure.
Automation is Key
A KYC Verification solution offering to support any digital service or web-based process has to be fully automated. Otherwise, it will have grave consequences for the user experience and customer onboarding process. Same is the rule for a two factor authentication solution that claims to streamline identity risk management for an online business or various digital channels used by a customer to avail its offered services. No customer is going to wait for more than a few seconds in order to confirm their identity using 2 step verification.
Shufti has developed all of its services on a singular principle of “ease of use” without compromising on the quality of the service. So, this KYC check of 2 FA can also be performed by Shufti in real-time. A customized code is forwarded on an end-user phone number as soon as a verification request is received from Shufti customer. Now, as soon as the verification code is entered into the desired field and sent to Shufti’s AI-based verification system, the real-time verification result is not only forwarded to end-user but also updated into Shufti Back office as proof of verification for the convenience of Shufti customers.
Customized 2 Step Verification
Shufti has always developed its identity verification services and KYC solutions with an aim to provide complete peace of mind to its customers. That is why 2 factor authentication from Shufti works in two ways:
Authentication with Phone Number – In this kind of 2 step verification, Shufti customers already has the phone number of the verifying user. Shufti directly sends the customized code to the end-user and after receiving the correct code in the assigned field, verifies the identity of the user.
Authentication without Phone Number – This form of identity verification is helpful in case Shufti has to verify the identity of a user who has not yet provided their phone number to Shufti customers. Shufti collects phone number of the end-user on behalf of its customer and then forwards a customized code on the provided number. After verification code is received by Shufti from end-user, Shufti updates the verification status in its Back Office providing essential personal information to its customers regarding end-user.

Use Case of 2 Factor Authentication
2 step verification solution can come in handy for various business and companies. It is not only suitable for mitigating online identity risk for in-house usage but it can be easily extended to end-customers. Whether it is a registration process or a authenticating access to a centralized database, Shufti offers infinite use cases to its customers. Two factor authentication solution from Shufti can be purchased as a separate service as well as part of a comprehensive KYC verification check including facial verification, document verification, and address verification. ID verification can also be coupled with 2-factor authentication to quickly authenticate the identity of an incoming user or potential customer.
E-commerce Industry – As a survey tells us that majority of identity theft leads to excessive shopping sprees, e-commerce websites can safeguard themselves from cashback requests by integrating a KYC software such as Shufti with an additional feature of 2 Factor authentication. A user will be required to perform 2 step verification not only at the time of registration but the same phone number can also be used to authenticate checkouts exceeding a set limit. Because of real-time verification results, the entire 2 step verification process is completed without causing any nuisance for end-users.
Banking Transactions – Banks can utilize 2 FA to their benefit by binding customers to perform 2 step verification whenever they are performing certain banking operations. Transactions beyond a set limit and using online banking services must be subjected to two factor authentication and Shufti will make sure that your banking customers don’t have to wait at all in authentication their identities using two factor authentcation solution from Shufit Pro.
Digital Service Providers – Any kind of digital service provider, whether a steaming service or an educational course offering website, can easily use 2-factor authentication to ensure that only the authorized persons are using their services. True identity of a user can easily be ensured by using ID verification in tandum with 2 step verification.
Social Media Websites – Two factor authentication or phone verification from Shufti can also help social media websites to provide a secure service to their customers. Any doubt regarding the identity of a user can easily be checked with Shufti’s best identity theft protection. An ID can be locked down until a user verifies their identity via 2 step authentication.
Centralized Resources – Now this use case is concerned with mostly corporate and business entities that have multiple employees working in different locations. Think of a news organization or multi-national company offering IT services to its customers. Two factor authentication services can ensure that only authorized personnel can access centralized resources of the company. Some of the companies, even use perpatual 2 step verification that works as notification system whenever there is an attempt of unauthorized access to sensitive or confidential digital resources.
2 Factor Authentication for KYC Verification
Although a comprehensive list of use cases has been provided in above list, but in general 2 step verification is used to not only collect crucial information regarding an incoming user but, if used correctly 2 Factor authentication solution can be the only verification service required for a company. It is safe to say that startup companies or businesses that are not in the position to spend a lot on identity verification solutions or find it too expensive to pay for ID verification, can use two factor authentication services of Shufti.
This not only provides a credible piece of information to the service provider about their customer but also creates a channel of instant communication between the end-user and Shufti customer. As for KYC verification, 2 step verification also serves an ideal purpose of performing online identity verification for mobile applications. With availability for both iOS and Android platforms, Shufti can be the ideal and cost-effective solution for mobile apps and service portals designed specifically mobile and smartphone devices.
Shufti is available in 225+ countries and all of its verification services are available in all of these countries as well, including 2-factor authentication solution. So even if your end-user is based in the most remote area of the world, there is more than 99% chance that Shufti can verify their phone number, through its real-time 2 FA service. This feature of global availability even helps international companies that are serving customers and users across multiple regions and continents. A unified verification procedure can be integrated instead of settling for multiple 2 FA solutions for individual regions or countries.
2 FA or ID Verification?
ID verification is a preferred method of performing KYC verification by digital and online businesses. Shufti offers ID verification services with identity cards, driving licenses and passports being the supported document formats. Universal language coverage of Shufti helps it to identify text and verify personal information in more than 150 official languages. Although both verification services are offered by Shufti in real-time, but as compared to ID verification, 2 step verification is better for companies that are not interested in performing comprehensive KYC check for their customers. In most of the cases, authorities require companies and businesses to collect verified phone numbers of their customers as part of their KYC regulations. Shufti can assist its customers in fulfilling this regulatory obligation.
ID verification when combined with two factor authentication, can serve as ultimate protection against online scams, digital frauds, and identity theft cases. You must set up a demo of Shufti trial version to check the superior service standards of Shufti for both ID verification as well 2-factor verification.
Conclusion
Shufti is an AI-based identity verification SaaS product offering multiple KYC and AML Compliance solutions to its customers. Two factor authentication is another smart verification procedure from Shufti to enable its customers in adopting comprehensive online identity risk management. It not only secures its customers from digital risks but from unwanted regulatory scrutiny as well because it is compliant to all major data security guidelines. GDPR compliance is one of those as it secures our customers from huge fines that are bound to be paid by any company that doesn’t collect user information in a secure manner, saves it properly and uses it for specific reasons.
Utilize 2-factor authentication from Shufti if you also want to verify the identity of your future customers in no-time. Shufti can even collect verified phone numbers of your customers on your behalf, which can then be used as a marketing channel for your new products, upcoming events or any public announcement. Competitive pricing is offered by Shufti, for which only prices are different but the quality of service is similar. No monthly minimum verification volume is required to be purchased from Shufti, as we offer “Pay As You Go” pricing feature to our customers.
Recommended For You:

 Explore Now
Explore Now