Facial biometrics system built for real-world identity
From verifying physical presence to enabling document-free onboarding, Shufti's biometric face Verification deliver fast, accurate, and adaptive verification.
Liveness detection
Deepfake detection
Photo-ID matching
Facial age estimation
Passwordless authentication
No doc onboarding
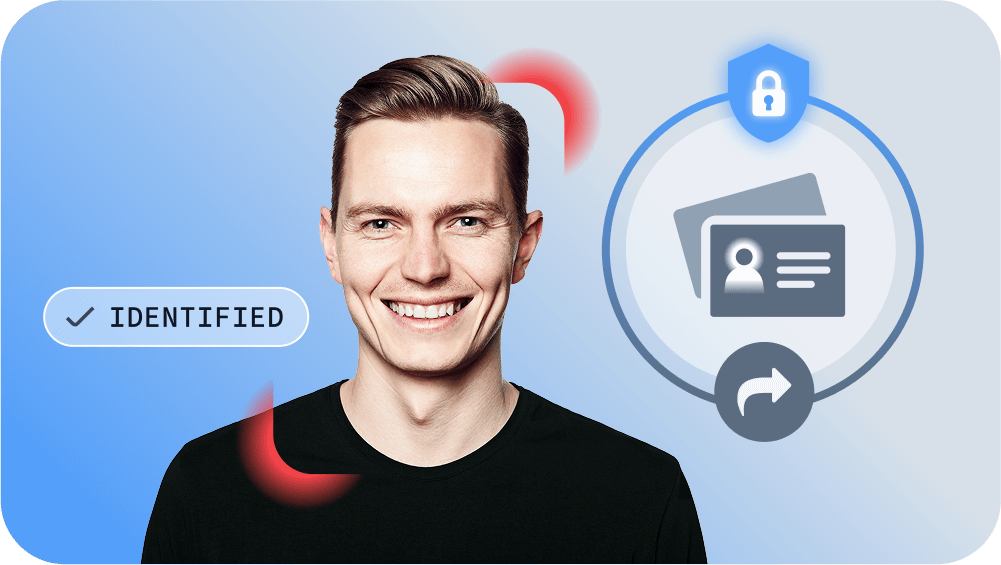
Instantly identify pre-verified users with facial recognition, while their associated documents are shared via secure backend transfer.

Detect real presence without any user interaction, no replay attacks, no liveness failures.

Detects deepfakes by analyzing 100+ unique facial vectors, catching what the human eye, and fraudsters, try to conceal.

Confirm identity by verifying facial consistency between the ID and the person on camera.

Estimate a user’s age from their face to support age-gated access and compliance.

Log in or perform high-trust actions with a quick and seamless face scan.

Instantly identify pre-verified users with facial recognition technology, while their associated documents are shared via secure backend transfer.
Uncompromising User Experience
Boosted user accessibility and comfort
Implement a password-free login via simple selfies for quick, secure access. Shufti’s face verification solution streamlines user experience, effectively deters fraud, and accelerates operational efficiency.

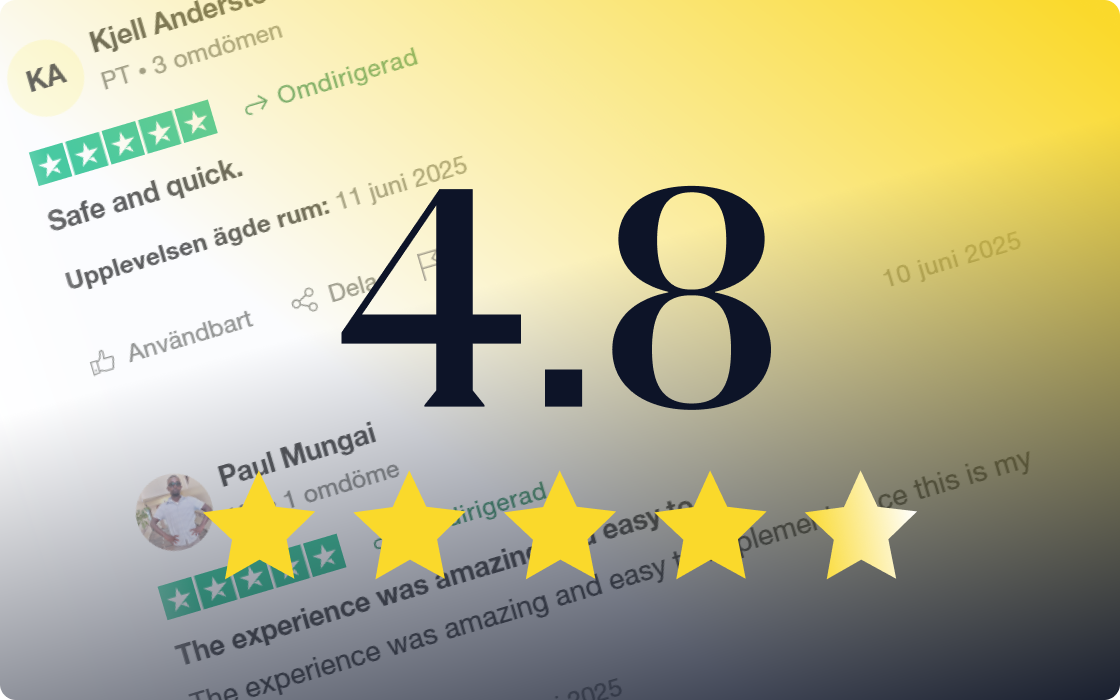
Users who know the difference
Proof of our exceptional user experience is in the numbers. Check out our industry leading 4.8 Trustpilot score.
See Trustpilot reviewsHassle-free image capture for global humans
Users can wear a hat, scarf, or glasses, in bad lighting or with old technology, and Shufti will still offer a seamless experience.
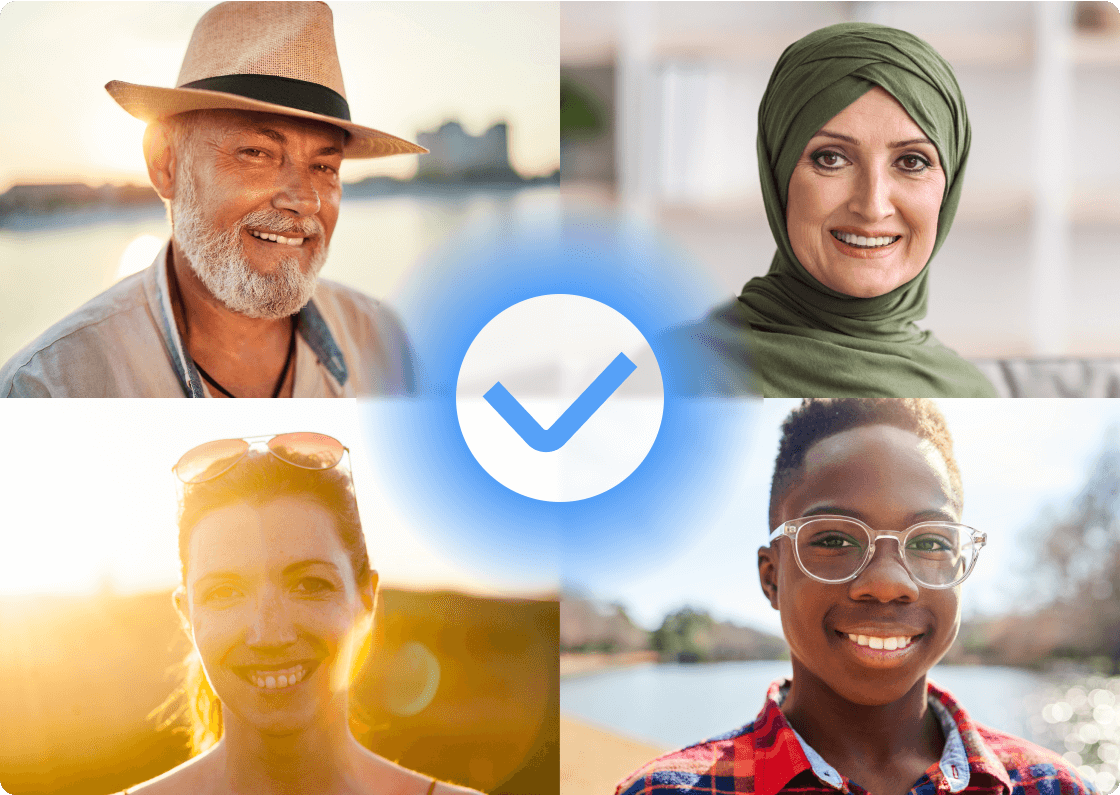
Zero effort liveness detection
- No extra steps needed from users
- Detects manipulation attempts in the background
- Ensures strong security without disruption
- Provides a smooth, frictionless experience
- Improves pass rates for faster access
*For high security applications, we also offer an active liveness capability
Zero effort
liveness
<1% FRR & FAR
Compatibility
with accessories
Bias
mitigation
= An exceptional user experience
The power of Shufti’s Face Verification Software
Shufti’s multi-layered forensic analysis ensures real-time face ID verification, deepfake detection and fraud prevention, safeguarding every verification attempt with cutting-edge security measures.
Video replay attacK
Identifies pre-recorded video submissions attempting to mimic live users.
Screen replay attacks
Prevents screen-recorded videos from being used as live user submissions.
3D depth and shape analysis
Confirms facial depth and contours to prevent flat image attacks.
3D mask impersonations
Detects hyper-realistic 3D masks used to replicate real facial features.
eye movement simulations
Detects artificial blinking or static eyes in spoof attempts.
Light reflection analysis
Identifies inconsistent lighting or reflections, a sign of spoofing.
Facial feature obfuscation
Flags fraudsters altering their appearance with makeup, tattoos, or digital overlays.
Shadow detection
Confirms natural shadow behavior, preventing 2D photo attacks.
AI-generated deepfakes
Flags AI-created faces designed to imitate real users.
Pupil dilation monitoring
Analyzes pupil response to light to confirm real human presence.
Lip movement verification
Analyzes lip sync and movement to confirm live interactions.
Digital injection attacks
Detects fake face streams injected into the verification process.
Skin texture analysis
Differentiates between real skin and synthetic materials like silicone masks.
High-definition photo spoofs
Detects high-quality printed or digital photos used for impersonation.
Shufti Innovation Room
Innovation that defines the future of facial liveness detection
Shufti has reengineered facial biometrics to go beyond recognition and into prevention, prediction, and precision. Our innovations aren’t just upgrades; they’re industry benchmarks.
<
>

iBeta Level 2 Passive Liveness certification
We are among the few global providers to achieve iBeta Level 2 certification for passive liveness detection, a mark of excellence in biometric security.
This means:
- No user prompts required for a completely frictionless experience
- Detect pre-recorded videos, screen replays, and photo attacks

Advanced defense against face swaps and deepfakes
Most AI models fail to detect face swaps where two different faces share partial similarity, leading to false matches. Shufti’s engine is built to solve this exact problem.
Now you can detect:
- Look-alike faces and artificially aligned swaps
- Micro-level facial inconsistencies

Fair for every face
Eliminating bias isn’t a feature — it’s a responsibility. Shufti’s face liveness verification ensures equitable performance across every user group, regardless of race, gender, or age.
Key bias mitigation efforts include:
- Optimized for all skin tones, facial shapes, and lighting conditions
- Avoid bias with regular audits to monitor false acceptance and rejection rates across demographics
Attack types we prevent:
Printed
Image
Replay
Mask
Makeup and
Disguise
Lookalike /
Impersonation
AI-Generated and
Synthetic Media
Display-Based
Injection
Environmental
Manipulation
Hardware-Level
Coercion-Based
Meeting critical compliance challenges with Shufti’s facial verification software
Related Solutions
Fast ID
Eliminate time-consuming document scanning, accelerate customer onboarding, and enhance authentication by using existing verified data.
 Explore
Explore
eIDV
Verify customers remotely and paperlessly using e-IDs checked against government databases for quick, accurate results.
 Explore
Explore
Know your customer
Simplify customer onboarding with efficient identity verification, reducing compliance burdens and boosting security across your operations.
 Explore
Explore
Our platform has you covered

Global Coverage
Break through growth limits thanks to comprehensive reach and accessibility.
Customizable
orchestration
Adapt verification workflows to fit seamlessly with your business operations.

All in One SDK
Integrate effortlessly with our versatile toolkit, compatible with various platforms and devices.
Explore the Shufti Global KYC Platform
Unlock your business potential with a verification platform built for worldwide scalability and reliability.
View Platformlearn more
Facial Biometric Verification and Authentication
Learn how Shufti uses liveness detection and deepfake detection to onboard global users seamlessly, while safeguarding privacy of users.
Download the whitepaper

Frequently Asked Questions
What is the difference between liveness detection and facial verification?
Liveness detection checks if a face presented is real and live (not a photo, mask, or video). Facial verification then compares that live face to a stored image or ID to confirm identity.
Can deepfake detection systems stop fraud in online onboarding?
Yes. Deepfake detection helps identify AI-generated or manipulated faces that could bypass basic checks, reducing fraud risk in digital onboarding.
How does face recognition work in the dark?
Shufti uses infrared imaging or low-light sensors, enabling facial features to be captured and verified even in poor lighting conditions. This is why Shufti is known for handling the most difficult and diverse edge cases in facial biometric verification.
Can facial verification be integrated into mobile apps or existing systems?
Yes. Shufti's modern verification APIs and SDKs can be embedded directly into mobile apps, websites, or existing compliance systems without disrupting workflows.
What technologies are used in face verification (AI, 3D mapping, neural networks)?
Shufti combines AI, deep neural networks, 3D mapping of facial geometry, and texture analysis to accurately verify faces and detect spoofing attempts. Additionally, it conducts deepfake detection to stop and prevent injection attacks.
Is face data stored, and how is user privacy protected?
Data storage depends on deployment, cloud or on-premises. However, Shufti supports privacy-first models where biometric data can be processed transiently or encrypted under GDPR and local laws.
How fast is the face verification process?
With Shufti, the process typically takes a few seconds, balancing accuracy with user convenience to keep onboarding friction low while ensuring compliance.
Take the next steps to better security.
Contact us
Get in touch with our experts. We'll help you find the perfect solution for your compliance and security needs.
Contact us
 Explore Now
Explore Now












