Biometrics identity verification system – a masterstroke in verification market

The biometrics identity verification system determines the resemblance of an individual by comparing the live-captured unique characteristics of a person against a biometric template stored in a database. The reference model of biometrics information is stored against which the system authenticates the information captured in real-time asking, “Are you indeed, who you say you are?”
With the advent of digitization and computerized databases, biometric verification has a high industrial adoption rate worldwide that ensures security through prompt personal identification. Identity verification is a requirement in the regulatory landscape. The digital world is under the threat of an array of cyberattacks and fraud that most of the time take place as a result of uncontrolled access over user accounts. The online user data and privacy protection rights highlighted in the EU’s General Data Protection Regulation (GDPR) demands the protection of digital data of customers from the cyberattacks. The personal and financial data of customers often get compromised by data breaches and account takeover frauds and further used for a variety of malevolent purposes.
Biometrics identity verification system
What is the Biometric identity verification system?
An identity verification system that allows individuals to be identified based on unique recognizable data such as biological traits that are specific to them. The unique identifiers include fingerprints, face, hand geometry, retina/iris, earlobe geometry, voice acoustics, DNA, etc.
However, by ensuring authorized access over digital user accounts and activities risks of cyberattacks can be mitigated to a considerable degree. Thus, the biometrics identity verification (IDV) system is an advanced approach towards online user authentication. From the national ID programs to digital banking platforms and healthcare to e-learning, biometrics IDV systems are adopted at a high rate.
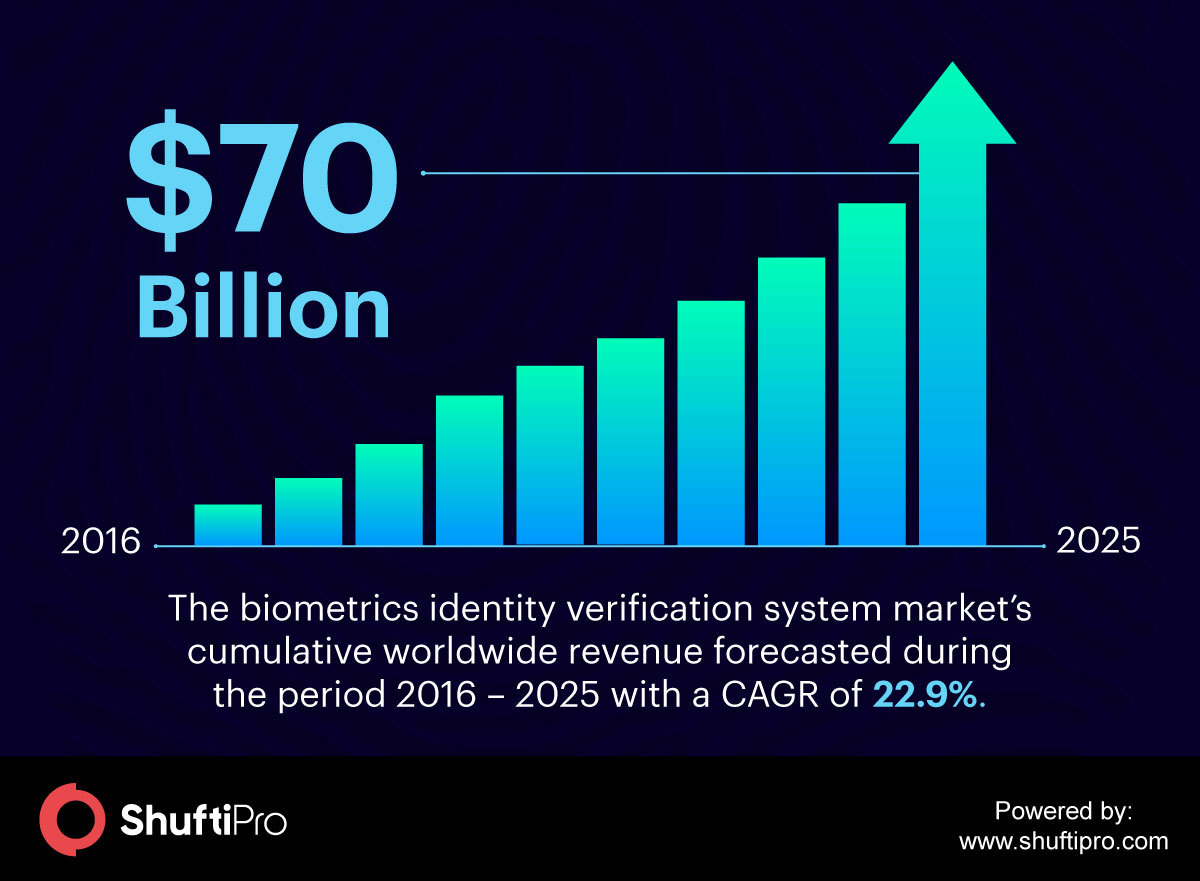
The Rise of Biometrics Distincts Traditional IDV Systems
The traditional online user authentication methods are getting distinct by the introduction of advanced biometric IDV systems. To balance security with customer experience, enterprises are rethinking the authentication measures for the secure digital environment. The survey conducted by Spiceworks shows that biometric authentication technology is used by 62% of organizations and an additional 24% will be using it within the next two years.
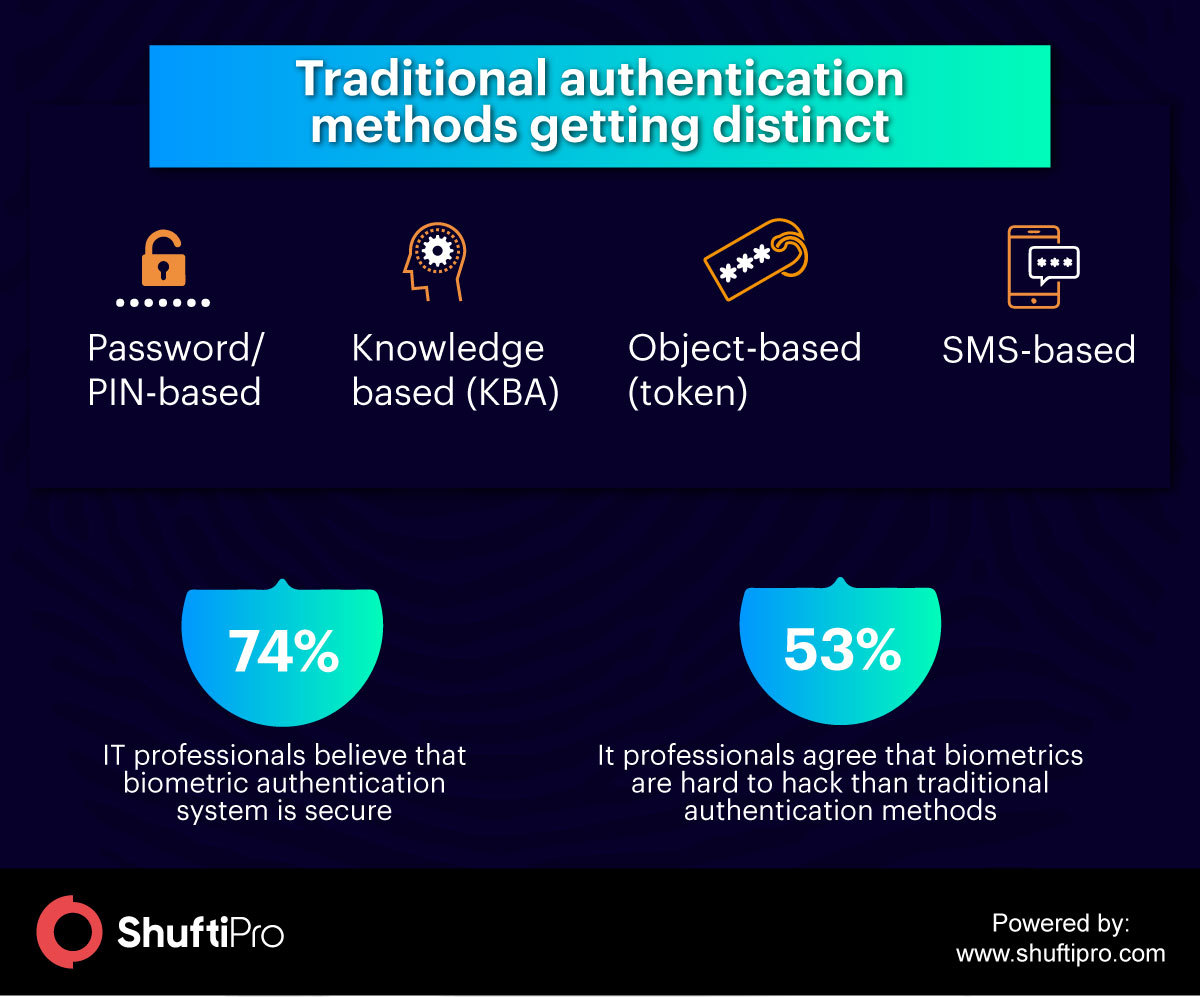
The traditional authentication methods have fallen from grace due to their security vulnerabilities that fraudsters exploit to perform malicious activities. Consequently, the IT industry is exploring secure and robust authentication systems that help decrease the risk of fraud keeping intact the customer experience. Biometrics identity verification systems are praised on multiple communication mediums. Along with the 46% of biometric authentication used on smartphones, 25% of organizations are using it on laptops, 22% on tablets and 17% on the time clock systems for employee identification.
Read more: how biometric technology is reshaping identity verification.
Emerging contactless biometrics amid COVID-19
The need for contactless biometrics has emerged amid the coronavirus outbreak. As per the World Health Organization (WHO), social distancing should be ensured at public crowded places to stop the spread of the virus. Under such circumstances, evaluating fingerprint scanners installed on airports and other public squares show that they carry various bacteria and viruses. However, there is a need for contactless biometrics so that the physical contact with the device for identification purposes can be eliminated.
Facial recognition systems help industries execute ‘social distancing chant’ by verifying the customers through face biometrics that do not need any physical contact with the device. Coronavirus outbreak has influenced many digital businesses as well, who are now deploying facial recognition systems to secure their online platforms from unauthorized access. A substantial increase is recorded in the online transactions during the coronavirus lockdown, which calls for strong user authentication methods as, during the time, fraudsters are prepared with their advanced approaches towards cyberattacks.
Biometric use cases
Door lock control
More than 11% of organizations are using biometrics identity verification systems for server rooms/data centers, 9% are using them to unlock doors in the offices.
Biometric sign-in:
8% of businesses use biometric sign-in systems into applications. The system authenticates the users that are performing high-value transactions, online purchases, bill payments, etc. Financial institutions are using biometric verification systems online for customer identification to ensure digital banking by an authorized individual.
Public security:
For criminals identification, facial biometrics-based security cameras are installed on streets and public squares. The biometrics system identifies the face of individuals passing by and detects the wanted criminal’s entity.
Travel Security:
Biometrics IDV systems are installed on airports and cruise ship stations for passenger quick identification at the checkpoints. The process is seamless and eliminates the overhead of a time-consuming boarding process with biometrics.
Authorized Healthcare Services:
Online patient identification with biometric authentication provides controlled access over patients’ accounts. The health benefits can be given to the eligible patients, hence, the fraud rate can be reduced in digital health services.
E-learning platforms:
The e-learning institutes and services providers can ensure that the registered students are availing services and appearing in the quizzes. The biometrics system will authenticate the end-users before and in between the quiz.
To sum up, biometric identity verification systems are expanding because they provide enhanced security and customer experience to digital businesses. Comparing them to traditional authentication methods, biometrics IDV systems are hard to hack which is the reason that the biometrics adoption rate in enterprises is high.

 Explore Now
Explore Now













