CCPA Compliance Checklist – Is your business ready?

With the world moving towards digitization, organizations have a customer base from all around the globe. More consumers mean more data to handle and higher threat of data breach. Protecting consumer’s personal data is one of the biggest challenges for businesses. Taking into account the increasing trend of data breaches and unauthorized access to user data for target marketing is driving the attention of regulatory authorities.
Previously, General Data Protection Regulation (GDPR) came into effect in May 2018 to ensure that how websites and organizations are allowed to collect, handle and process personal data of consumers, it can be anything from names, addresses, browser history to financial data and many more.
California Consumer Privacy Act (CCPA)
GDPR compliance has paved the way for new consumer privacy initiatives known as California Consumers Privacy Act (CCPA) which came into effect on January 1, 2020. While GDPR is more of a “privacy by default” and “valid consent from consumers” legal framework for the entire EU, CCPA is about “creating transparency” and giving rights to its consumers in California’s huge data economy.
According to AB 375 of CCPA, every California consumer is given a right to see all the personal information that a company or organization has saved on them. Moreover, it allows consumers to demand a full list of all third parties with whom data is shared. In case if the companies violate the privacy guidelines, consumers have the right to sue them, irrespective of a data breach.
What is personal information as per CCPA?
“Information that identifies, relates to, describes, is capable of being associated with, or could reasonably be linked, directly or indirectly, with a particular consumer or household.”
This definition is clearly broader and complex than GDPR as it lists a wide range of standard examples. For instance, social security number (SSN), purchase histories, browser histories, drivers’ license numbers, and other “unique personal identifiers” like geolocation & device identifiers and online tracking technologies. However, it excludes the publicly available information such as tax data from the central registry or government records.
What does CCPA means for business?
The CCPA already effective from January 1, 2020, has a significant impact on the corporate privacy policies across technology, media and entertainment, and telecommunications (TMT) industries. Many brands across the United States largely avoided GDPR. Despite, the emerging privacy concerns among consumers and global regulations are core drivers around data privacy mobilization across TMT industries.
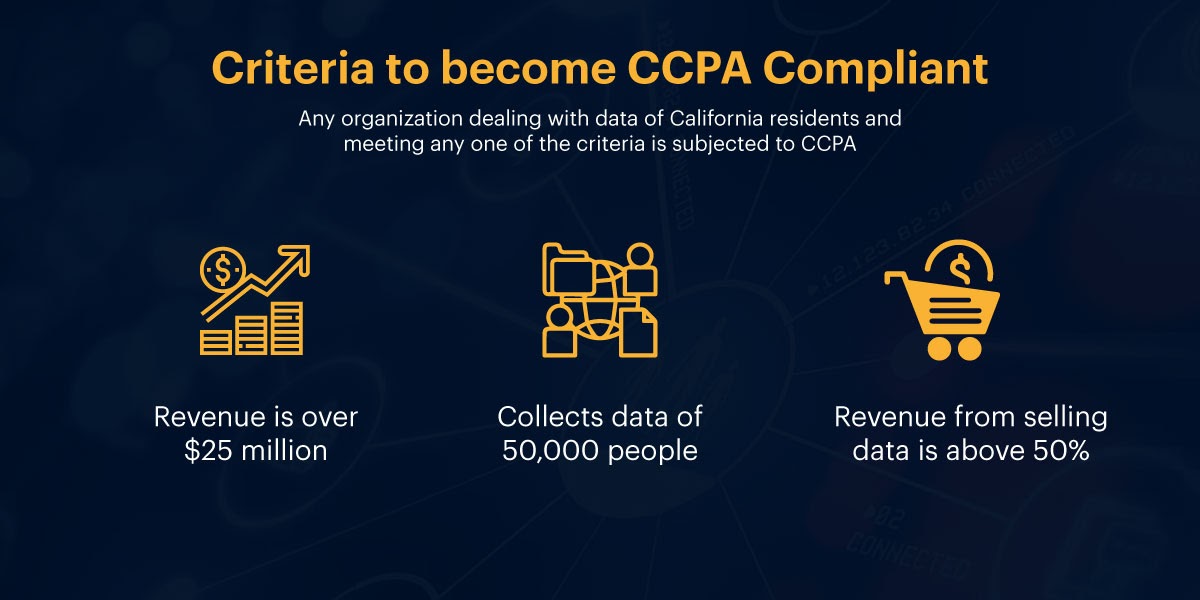
The CCPA compliance is obligatory for all the businesses and companies dealing with California residents and possessing at least $25 million in annual revenue. Additionally, the businesses that cater to personal data of at least 50,000 people, regardless of their size, also fall under obliged entities. To be obliged by CCPA, companies don’t have to have a physical existence in California, in fact, they don’t even have to be in the United States.
CCPA is considered one of the strictest privacy laws in the United States. It forearms California residents to monitor and control how businesses process their personal data. It means now the organizations have to pay homage to the requests from consumers to access, delete and even opt-out of sharing or selling their personal information. Taking into account such CCPA-specific requirements, organizations and businesses need to update their privacy programs and stop selling data on consumer’s requests.
Last year in April, an amendment was made in the law that exempts “insurance institutions, agents, and support organizations” since they are already subjected to another similar regulation under California’s Insurance Information and Privacy Protection Act (IIPPA). Moreover, it also excludes medical or health information collected by a person or entity governed by California’s Confidentiality of Medical Information Act or Health Insurance Portability and Accountability Act of 1996 (HIPAA).
Risks associated with third-party services
CCPA compliance holds a very significant challenge for businesses because of the involvement of third-party policies. Being the obliged entities, working with third parties is crucial for organizations. They are held responsible for whatever those third parties do with their data.
Under CCPA, the organizations that collect or process the personal data of consumers are liable to keep the data private and protected under any circumstances any number of third parties such as service providers or external vendors performing marketing, verification, or billing, etc., potentially gathers the organization’s data.
Businesses need to consider a comprehensive audit to determine which third-parties are collecting, processing or storing consumer’s data on their behalf. Upon identifying, the organizations need to make amendments in policies and contracts to achieve CCPA compliance.
CCPA Compliance Checklist
With the introduction of CCPA, the increased disclosures have become a fundamental part of businesses subject to new compliance. The organizations need to develop detailed privacy notices to present consumers when their data is collected. Moreover, they need to publically disclose the consumer’s right under CGPA.
Here’s a CCPA compliance checklist that defines a roadmap for companies to meet the CCPA requirements.
-
Know if CCPA applies to your business
The most important thing the businesses need to do for being compliant with CCPA is to first determine if they lie under obliged entities or not. CCPA law has mentioned certain criteria for an organization to be obliged by the law and some exemptions.
-
Review Personal information collection
To be compliant with CCPA, it is essential to figure out what personal information your organization/business is collecting from the consumer. The collection of the data is in fact, the fundamental of CCPA. Many times, the organizations are not fully aware of the type of data they are collecting from a user. For instance, the IP address of the consumer, which also falls under the definition of CCPA personal information.
-
Map data relationships
According to the California Consumer Privacy Act, the customer has the right to know what data is collected and for what purpose. To successfully meet this demand, companies need to develop data maps that clearly show the scope of personal information being collected, processed and stored. Moreover, it is mandatory to describe how the data is used internally and whether it’s sold or shared with third parties, if so then for which purpose.
-
Review policies for handling information
CCPA law intends to improve the way organizations handle consumers’ personal information. This requirement is driving organizations to review their existing policies and procedures first. For instance, what procedure would they follow if a customer requests to delete his data?
Let’s say the company follows the parallel topology of storing data which means other than server the data is stored in the systems as well. It means deleting data from the server isn’t going to be enough, the procedure has to be revised.
-
Update organization’s privacy policy
Updating the company’s privacy policies is a mandatory part of CCPA. These policies are for customers to describe in detail what data the organization is collecting and its purpose of collection. As per CCPA, the policies must include the following three things
- Consumer rights – describing what control a customer has over his collected information
- What is collected – describing what personal information is collected from the consumer side.
- How information is used – informing the customers that how the collected information will be shared i.e. for business purposes or selling to external vendors.
These three points must be described in detail in the company’s privacy policy.
-
Prepare for consumers’ opt-out and deletion requests
With CCPA allowing customers to go for opt-out and deletion requests, they are definitely going to use their right. To accommodate such requests, organizations have to be prepared. Dealing with consumers’ requests manually is not effective. Setting up an automated system to facilitate companies with delete and opt-out requests is the need of the hour.
For this, it is recommended to come up with a procedure for consumers by which they can request a copy of their data and data deletion.
-
Review third-party contracts and conduct audits
California Consumer Privacy Act puts a bigger responsibility on the organizations to keep track of the third-party collection of consumers’ personal data. In case of any violation, the company is held liable. Therefore, to avoid such situations in the future, companies need to revise their contract with third-party companies and service providers using customers’ personal information.
Just reviewing contracts isn’t enough, but the organizations need to conduct regular audits for the service providers having access to the data to know if there’s any loophole or threat.
-
Review security protocols and implement data encryption policies
Data privacy is the base of CCPA law and it means protecting consumers’ data by every means including data breaches. That’s why reviewing security protocols and implementing data encryption is equally essential for the companies to be compliant with CCPA laws.
-
Employee training regarding CCPA
Employee training regarding new company policies, data handling, and privacy laws is the core responsibility of an organization. Employees must receive in-depth training on every part of the California Consumer Privacy Act especially the ones that are directly applicable to their job roles.
The violation of the CCPA law can have stiff penalties and fines, therefore, companies need to be vigilant in developing new policies and procedures to comply with regulations.

 Explore Now
Explore Now













