COVID-19 & Telehealth Fraud: Why ID Verification Is Necessary

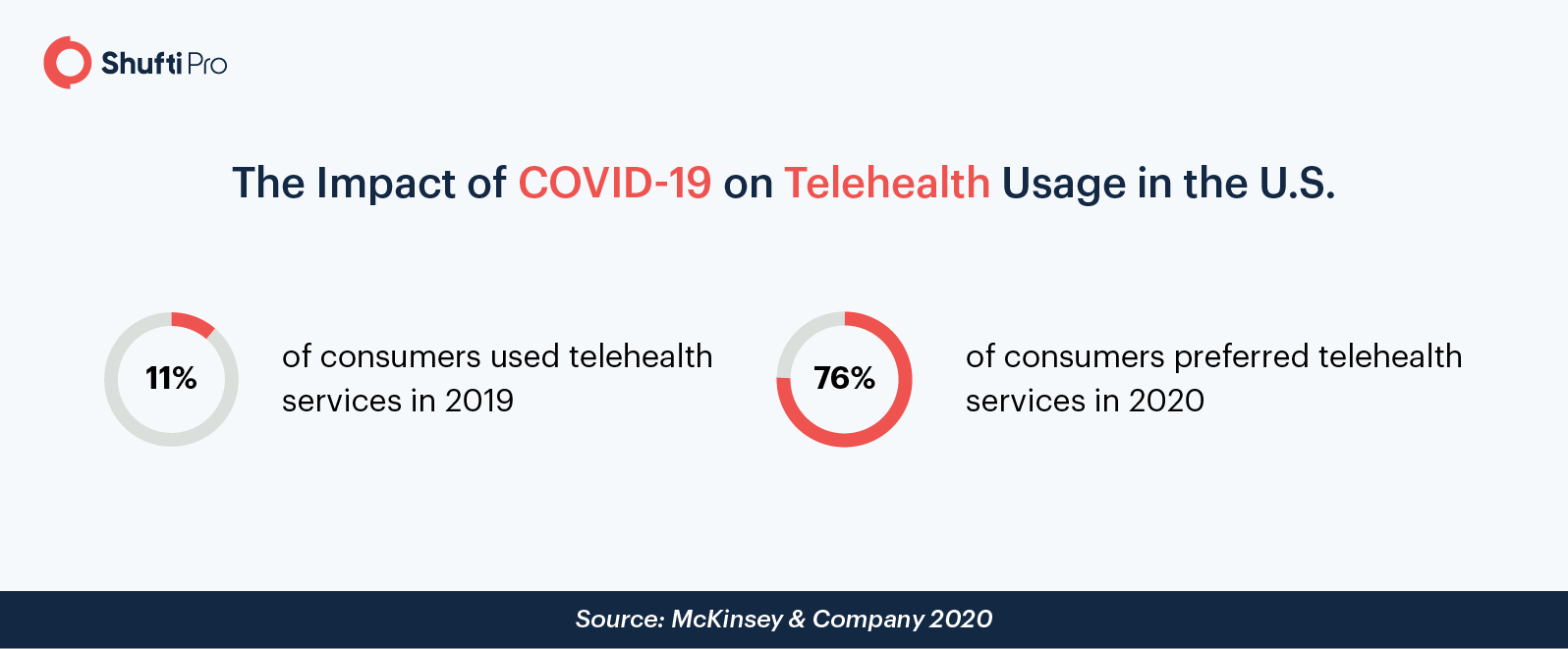
From being a medical coverage option to becoming a medical necessity, the telehealth industry has completely transformed. The Covid-19 pandemic taught us various lessons regarding our health, the adoption of healthy habits, and the way our current healthcare institutions operate. At the forefront of these lessons was the recognized need for remote and digital communication systems. Numerous industries are pivoting towards digital operations, and telehealth is no exception.
Take a look at the following statistics that are indicative of this trend:
- A 50% increase was reported in the number of telehealth visits in the first quarter of 2020
- Telehealth for individuals aged 18-49 increased from 68% in January to 73% by March 2020
- Approximately 71% of patients had considered telehealth in the early days of COVID-19, while half of them had already gone through with it
The market for telehealth is forecasted to reach a value of USD 186.5 billion by 2026
What are Telehealth Services?
In Telehealth Services, patients and specialists are not physically present in the same room. Instead, technology is used to hear and see each other, much like Skype and FaceTime. During the consultation, a patient and a doctor interact via a smart device or a computer screen.
Telehealth, also known as telemedicine, has allowed healthcare service providers to reach their patients remotely and continue to administer medical treatments as needed. While telehealth services bridged the gap between patients and physicians during the pandemic, it has paved the way for potential fraud risks.
The Data Breach and Account Takeover Diagnoses
Telemedicine fraud, such as data breaches, has the highest cost average, amounting to a value of USD 7.3 million. What makes it more concerning is the fact that this average is 84% higher than the global average cost for data breaches.
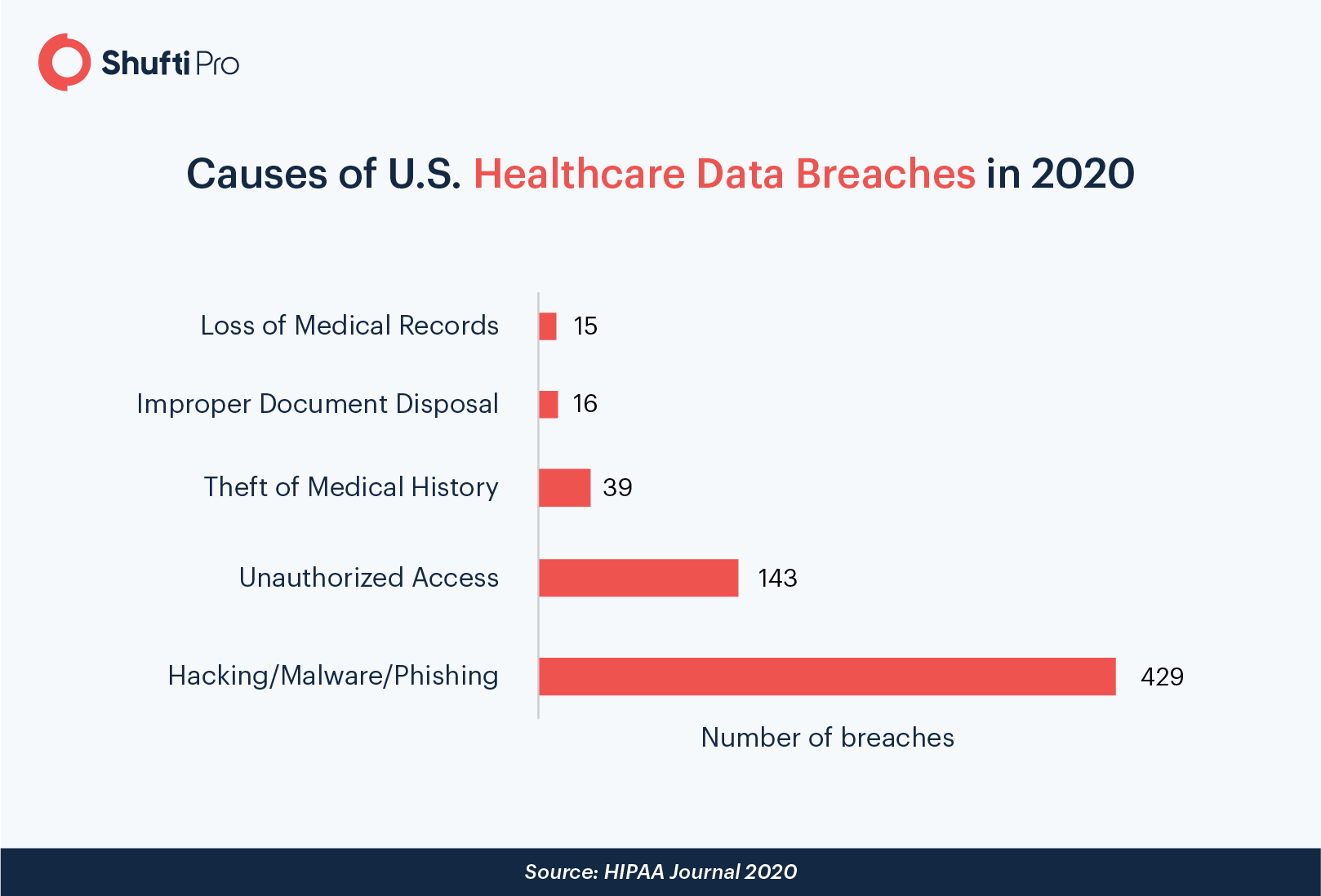
The main reason behind this industry being more attractive for criminals is that medical records contain crucial Personally Identifiable Information (PII), such as the patient’s age, address, ID card number, insurance details, medical history, etc. Once this information is stolen, it can lead to identity thefts, account takeovers, and countless more scams.
Additionally, the increasing institutional interest in digital platforms has empowered cybercriminals, providing them with more opportunities to exploit the healthcare system. By simply using the stolen data to log into accounts, criminals are able to impersonate legitimate patients to get their hands on medical insurance, prescription drugs, and free treatments.
The KYP Prescription
The state of the telehealth service industry is not all doom and gloom. Fortunately, there is a practical solution that can prevent telehealth fraud: The Know Your Patient (KYP) approach.
In a traditional setup, patients are required to bring ID documents to get their identity verified prior to receiving medical treatments. Similarly, patient identity verification becomes even more crucial in a virtual setup. This is particularly necessary as 175 million medical records were breached over the last decade. Robust telehealth solutions can significantly reduce this amount by streamlining the KYP process and related telehealth interactions.
Patient Identity Verification in Action
The KYP process starts during the initial stage of account opening. In this stage, the patient uploads an official ID document, such as a government-issued ID card, along with a selfie. The patient identity verification software automatically extracts the information provided through Optical Character Recognition (OCR) technology. Using artificial intelligence algorithms, the identity verification solution accurately verifies the information and the image, delivering the results in mere seconds. Once this is done, the patient can continue to receive the consultation or treatment.
Telemedicine service providers also verify the patient’s age during this process, so that minors can be weeded out by matching their age against the minimum age requirement. These security checks aid the telemedicine industry in minimizing fraud, meeting regulatory compliance standards, and providing enhanced patient experiences.
Legislation is Not Enough Anymore
For the US-based telehealth system, The Health Insurance Portability and Accountability Act (HIPAA) of 1996 is one legislation that companies need to be vigilant of. This act, which aims to fend off healthcare fraud, should be implemented hand-in-hand with patient identity verification solutions. By making identity verification a prerequisite for telehealth services, healthcare providers can be held accountable for non-compliance, while patients can be held liable for any sign of telehealth fraud.
If the use of robust identity verification software is mandated, a culture of compliance can be maintained in the industry. The advocacy of such software by third-party service providers results in the better provision of medical care, thus enhancing an industry that is expected to grow long after the current crisis.
Predicting the Future
With patients fully adapting to the virtual era of COVID-19, telehealth services will undoubtedly surge in demand — even post-pandemic. Once telemedicine and ID verification are combined, it creates a practical method of ensuring patient data security. While embracing and executing such methods can seem daunting, they must be utilized to provide seamless patient experiences. In the long run, such methods will not only safeguard patient identities but will also ensure health care data integrity on top of maintaining compliance with HIPAA standards.

 Explore Now
Explore Now













