Cybersecurity vs User Experience – Knowing the Art of Balancing

Several years of debate between cybersecurity and customer experience has driven most people crazy. In the digital world, people are still scared of sharing their details with online stores and e-payment systems. The idea behind online systems is to ensure a better user experience but will it be of any benefit for the company if security is compromised? I don’t think so. Along with great customer experience, firms cannot keep security and data protection at the end of the priority list. Nevertheless, balancing them both is not as easy as it sounds. Without any more stories, let’s discuss both the concerns in detail.
Experience and Security – Understanding the Tug of War
On one side of the story, businesses consider security above everything else. In the digitally advanced world, identity theft is one of the biggest concerns. After a spiking 3.36% increase in ID fraud, companies are now considering security before it adversely affects them in 2021. For this, identity verification is important.
On the contrary, none of the companies would want to compromise on the customers’ experience. However, many firms fail to provide a fantastic experience to their customers along with top-notch security. Ultimately, businesses have to choose one over the other.
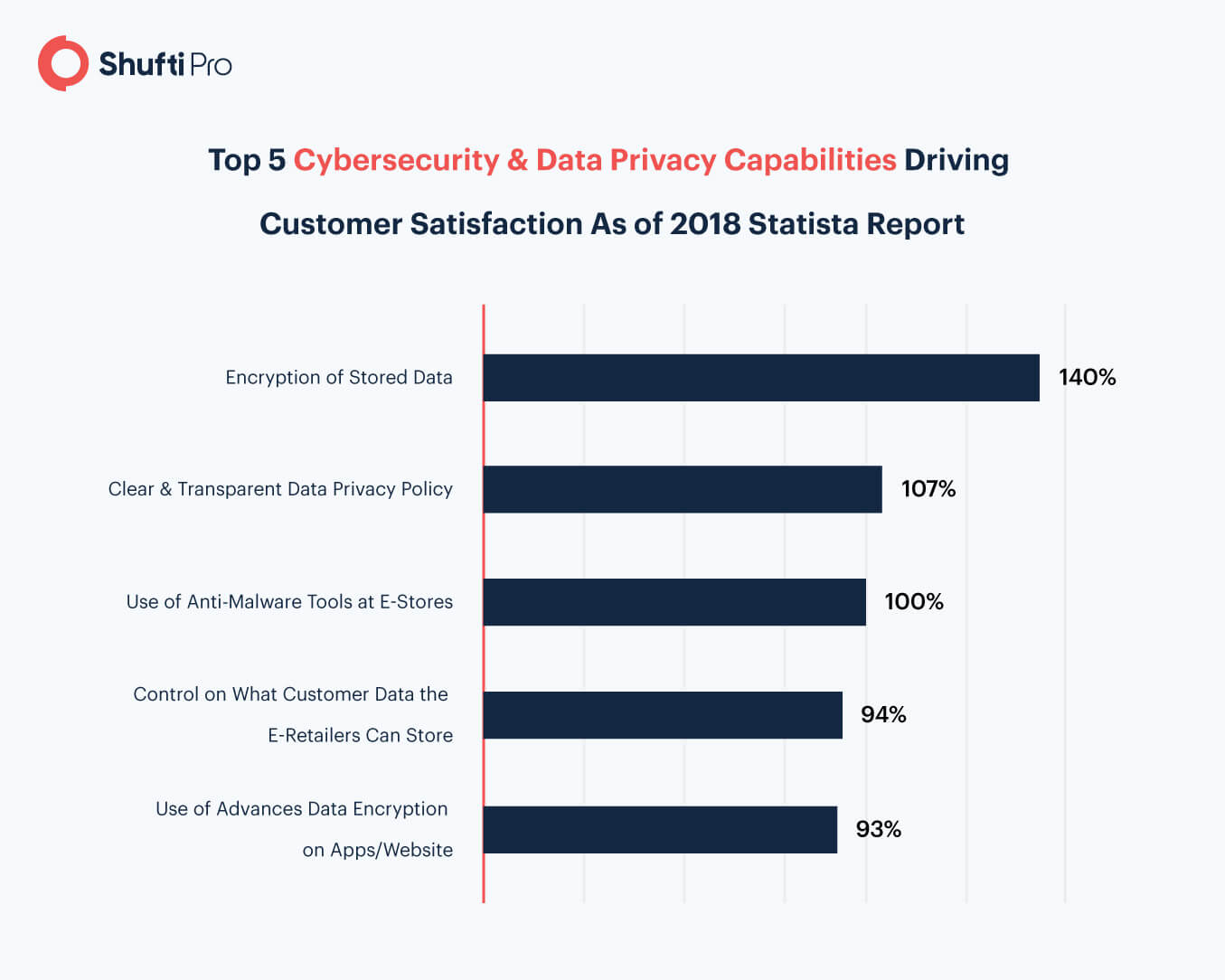
Tips for Balancing Customer Experience and Security
There is no chance of choosing only one of the two. Entreprises have to ensure both security and experience because dropping any of them has numerous consequences. The art of balancing security and use experience is not easy to acquire. Nonetheless, we have gathered some tips to help you out.
Understand the Hierarchy of Customer Needs
The famous Maslow’s Hierarchy of Needs is not just limited to employees now. Many researches have shown its use in the customer experience domain too. Businesses need to analyse the use and impact of their products/services on consumers. Every stage of the hierarchy must satisfy the end-users as well. This will also help you build the buyer’s persona.
Address the Common Issues
Many companies overlook common issues which become the primary cause of their downfall. Data breaches, identity theft, deepfakes, phishing attacks, etc. are commonly reported but businesses lack in taking robust precautionary measures. Furthermore, challenges while performing verification during onboarding or a transaction can increase abandonment rate. Not addressing these problems might lead to compromised customer experience and security too.
Encrypt Data with Additional Security Layers
Identity verification cannot be omitted but it should not be inconvenient as well. Moreover, they must be efficient enough to secure customer data. Always double-check security and add multiple layers of defense against ID fraud. Multi-tier security allows you to avoid any fraud attempts, whereas customers are satisfied with the firm’s security measures.
Test Your Services/Products on a Group of 5
Research suggests that testing products or services on a group of five people can be very helpful in making it efficient. It gets a lot easier to identify the drawbacks and resolve the issues on time. Testing always helps you overcome the challenges and in turn, your customers can have a great experience.
Improve According to Customer Expectations
The increasing customer expectations can help you a lot in improving all your systems (security included). At some point, you may not be able to reduce friction from the process but you can change how customers feel about it. For instance, you can change the design of the back office to make it more interactive and identity verification will become interesting for them. You can also add a short video that explains the process. Customers will appreciate your effort along with engaging more often.
Statistical View of Cybersecurity and User Experience
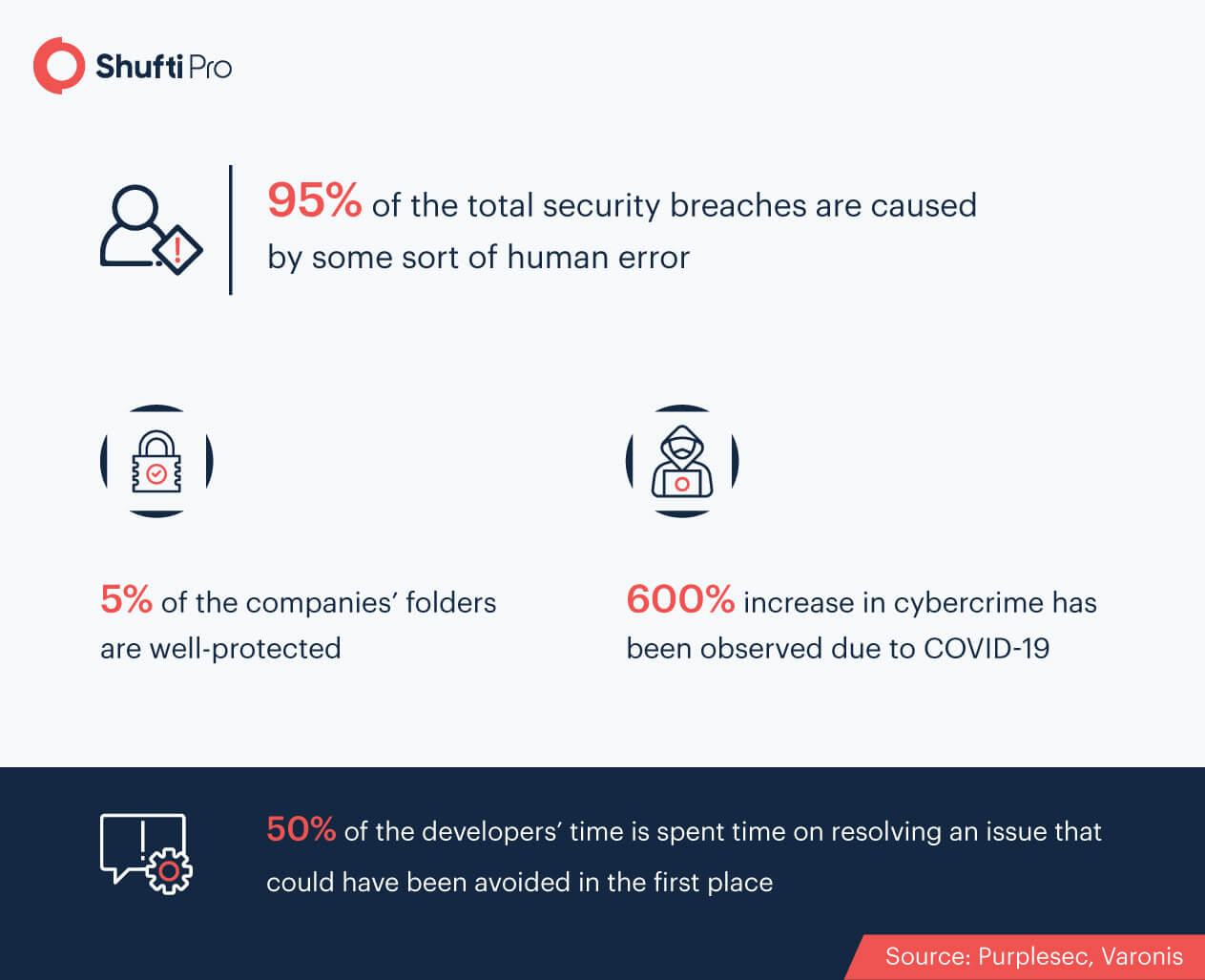
Blueprint for Better Customer Experience along with Security
Well, we have talked a lot about balancing the security and user experience equation but regulations are becoming rigid. ID frauds are increasing with every passing day, so what can be done to be compliant with the laws, protect your customers and provide a state of the art user experience? Wouldn’t it be great to achieve all this with one simple solution? Here’s the blueprint for the “security = user experience” equation.
Build a Better Customer Onboarding Process
It all begins with the onboarding process. No matter what your industry is, the customer onboarding process is the first impression and that must be perfect. Therefore, focus on creating the best customer onboarding process that is convenient for the end-users and helps you acquire legitimate customers only. Never forget to get feedback from your customers and stick to continuous improvement.
Suggested: Shufti’s Insights on Enhancing Customer Onboarding Experience
KYC and AML Compliance
The landscape of KYC and AML regulations has drastically changed this year. Criminal activities spiked high due to the pandemic, so regulatory authorities have imposed more rigid laws for KYC and AML. The customer due diligence (CDD) protocols have become more robust as per the regulations. If you haven’t checked these evolved regulations, check them out here.
Artificially Intelligent Speed of Processes
Artificial Intelligence has been marking its importance in every other department. From automated customer support to real-time identity verification, AI has a number of benefits for the corporate world. Applications of AI like machine learning can help you in developing top-notch processes. Thus, you can perform ongoing transaction monitoring and identity verification checks, enhance the use of products/services and much more.
In a Nutshell…
The majority of the companies are unable to balance customer experience and security. Even in the digital world we arguably live in, most companies are either focusing on improving customer experience or employing better cybersecurity measures. However, maintaining a balance between both of them is important. Customers demand an out of the world experience along with great cybersecurity measures. Some simple tips and hacks like improving customer experience using videos can be of great benefit for your business. Lastly, complying with the laws can help you a lot in providing great user experience along with cybersecurity.
Get in touch with us to know everything about security and customer experience.

 Explore Now
Explore Now













