DSAR Under GDPR and CCPA – Understanding the Key Differences

Data protection is one of the key concerns of organisations these days. For the same reason, data protection laws have increased in different parts of the world. A study reveals that only 10% of the global population had data protected until last year. The study further states that approximately 65% of the population’s data will be secured by the end of the year 2023. The Cisco Consumer Privacy Survey shows that 84% of people are concerned about data privacy in the digital world and want more control over how their data is being used. Given the rising concerns of end-users, law-making bodies have enforced certain data protection regulations that provide consumers with the right to disclose their data. Arguably the European General Data Protection Regulation (GDPR) gives Data Subject Access Request (DSAR) to the residents. Similarly, there are many other regulations for data privacy like the California Consumer Privacy Act (CCPA), PIPEDA in Canada and LGPD in Brazil. Let’s take a look at the key differences of DSAR under GDPR and CCPA.
What are the Seven Principles of GDPR?
The General Data Protection Regulation (GDPR) is responsible for the data protection and privacy of individuals belonging to the European Union (EU). It sets out the following seven key principles:
- Fairness, lawfulness and transparency
- Data minimisation
- Storage information
- Accuracy
- Purpose limitation
- Security
- Accountability
What is DSAR?
DSARs are not new since companies and government authorities have been using them for many years now. However, data protection and privacy regulations imposed several changes that make it convenient for consumers to request data access. A DSAR is a request from a data subject to your firm. As per regulatory requirements, you are obligated to provide all the information as soon as possible.
Article 15 of GDPR states,
“A data subject should have the right of access to personal data which have been collected concerning him or her and to exercise that right easily and at reasonable intervals, to be aware of and verify the lawfulness of the processing.”
According to Title 1.81.5 of CCPA,
(a) A consumer shall have the right, at any time, to direct a business that sells personal information about the consumer to third parties not to sell the consumer’s personal information. This right may be referred to as the right to opt-out.
(b) A business that sells consumers’ personal information to third parties shall provide notice to consumers, pursuant to subdivision (a) of Section 1798.135, that this information may be sold and that consumers have the “right to opt-out” of the sale of their personal information.
(c) A business that has received direction from a consumer not to sell the consumer’s personal information or, in the case of a minor consumer’s personal information has not received consent to sell the minor consumer’s personal information shall be prohibited.
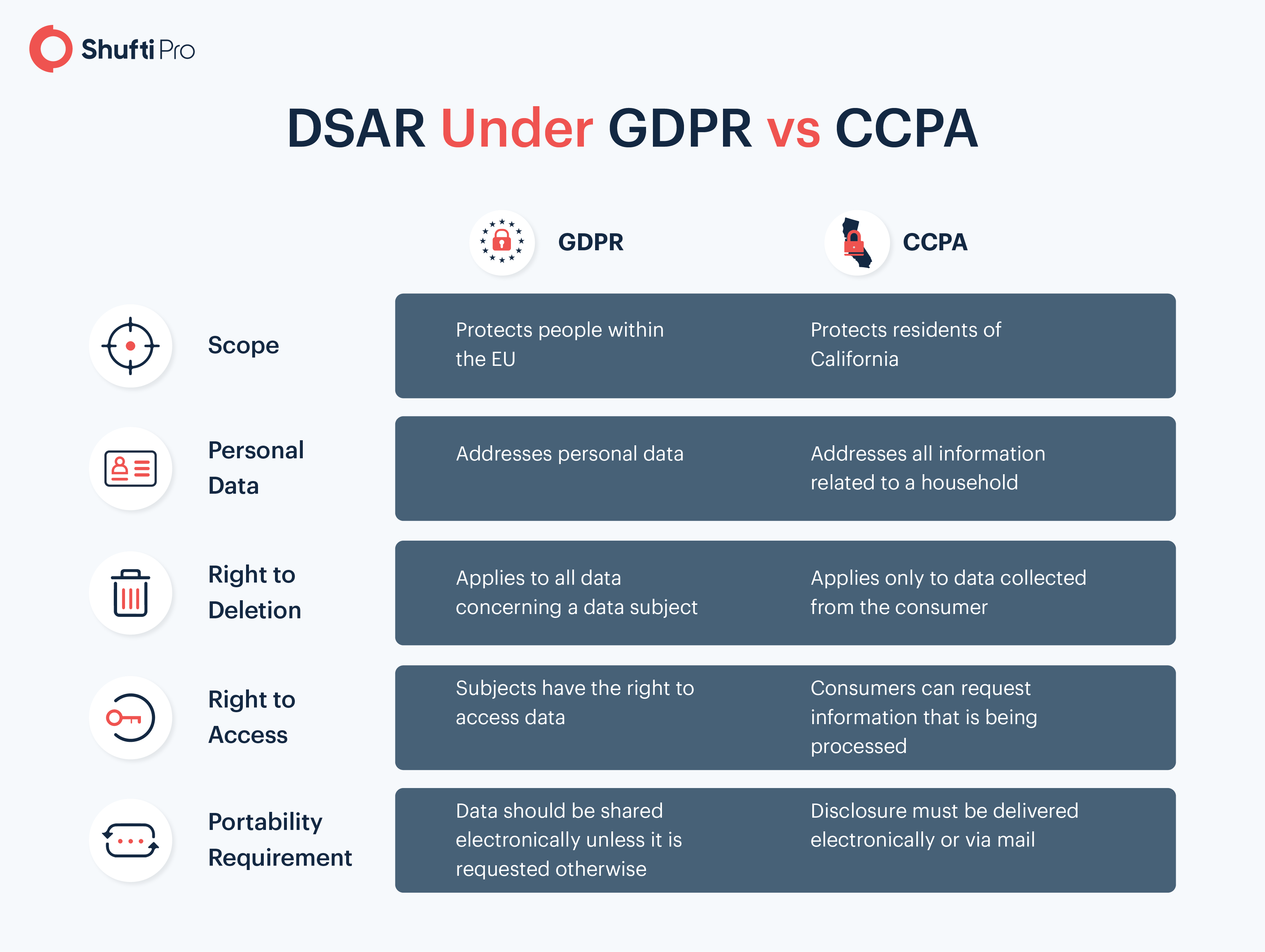
DSAR Under GDPR and CCPA
Under GDPR and CCPA, the DSAR has the following differences and similarities:
DSAR – The Key Considerations
With DSAR, there are some common expectations. A few of them are:
- A company will respond to the request or take action
- The response will include all the information
- Action will occur in a defined period
For companies, one of the fundamental requirements is to maintain a record that a response was provided on the request. Companies must track the date of the receipt and the date of response.
Businesses have a certain time limit to respond to DSARs. As per GDPR, firms must get back to the request within 30 days. On the other hand, the CCPA has imposed a 45-day restriction for the responses. Other timelines include:
- 10 business days for confirming the receipt of the request
- 15 business days for responding to opt-out requests
- 90 business days for informing vendors to not sell consumer information
- Two years for maintaining the log of the requests
DSAR – The Key Exceptions
There are some exceptions to DSAR for organisations under certain circumstances. A common exception under GDPR is the disproportionate effort. Companies cannot use DSAR exceptions for not responding to the requests.
California Consumer Privacy Act (CCPA) allows organisations to delete requests. For instance, if a consumer requests a deletion before the warranty period ends, the company is allowed to do that.
In simpler words, there are many exceptions of DSAR and they vary according to the jurisdictions, laws of the state and many other factors.
DSAR Checklist for Organisations
Here’s how businesses can opt for responding to DSARs:
- A system that can efficiently receive and process all the requests
- Verification of identities of data subjects upon receiving requests
- Data collection and review of the processed requests
- Remediation plans
- Plans for delivering the requested information
Can businesses refuse to respond to DSAR? Yes, under certain circumstances, companies can turn down a request. Here are some of these reasons:
- Searchable and accessible format of personal information is not maintained
- Compliance is the purpose for processing personal information
- Information is not used for commercial reasons
- The data is used for national security or law enforcement
- The data subject has made multiple requests for disrupting the system
Key Takeaways
Data protection and privacy are the major concerns of law enforcing bodies and organisations. Different regions of the world have imposed various regulations like GDPR in the EU, CCPA in California, LGPD in Brazil, etc. The Data Subject Access Request (DSAR) provides consumers with the right to access their data. Under CCPA and GDPR, the DSAR provides visibility and control to the data subjects. Although there are certain exceptions of DSAR under certain situations, data subjects still have the liberty to request access, deletion or closure of their personal information.
Got questions about data protection and privacy? Our experts are always there to assist you.

 Explore Now
Explore Now













