E-learning Platforms and IDV Solutions: A Natural And Much Needed Partnership

The advancement of modern technologies and telecommunication modes has made online assistance available to a broad spectrum of the population. The number of students taking the traditional education route has drastically dropped and most switched to online classes, colleges, and universities. The simplicity and convenience of online learning have made it a top choice as an educational medium.
E-learning has made it possible to reach a larger audience, as geographical boundaries no longer restrict the distribution of instructional material. E-learning endeavors have a vast amount of user data that authorizes such platforms to utilize machine learning algorithms to improve their educational techniques.
Consequential Upsurge in E-learning Market Size
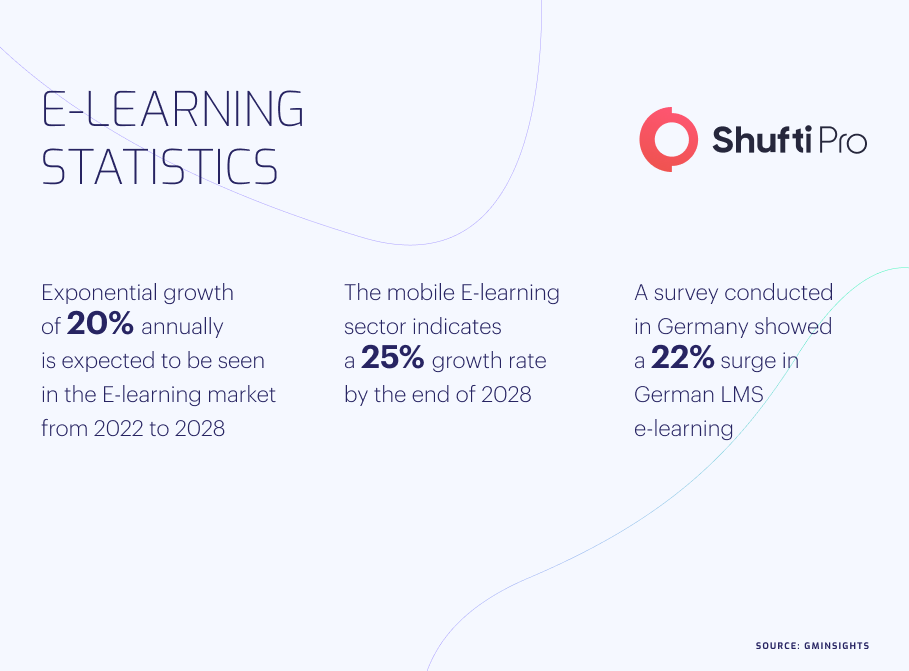
Since digitization has rapidly risen due to the Covid-19 pandemic, people are often left with no other choice but to utilize E-learning. Online education comes up with surprising features such as mobile learning, micro-learning, gamification, etc. the number of MOOCs (Massive Open Online Courses), represented an exponential growth up to 220 million from 300,000 within the last few years. According to Research and Markets, the e-learning industry is predicted to reach USD 350 billion by 2025. Ultimately, this online educational trend continues to grow in popularity and revolutionize how individuals of all ages can access and consolidate their academic knowledge. Other factors responsible for massive growth in E-learning are accessibility, flexibility, customization, and cost-effectiveness.
North America is clearly in charge of the direction of the E-learning market and is expected to show an 11.3% rise by the end of the year 2030. In 2012, the E-learning market was worth USD 215 billion and is expected to reach an estimated value of USB 645 billion by 2030.
Probability of Cyber Crimes Affecting E-platforms
The increased use of E-learning platforms has been documented, but little consideration has been given to security breaches in terms of education and research.Modern E-learning systems do not face the crucial security requirements as their use may lead to unwanted deterioration of the online learning process. This invasion of E-learning has led to the unfortunate emergence of cybercrimes. One in five percent of online educators has been the victim of cyber attacks since the start of COVID-19.
Ransomware is the most common cybercrime,designed to prevent user access to files by encrypting them and demanding a ransom for deciphering the encrypted data. The number of ransomware attacks decreased rapidly between the second and fourth quarters of 2021, going from nearly 189 million cases to 133 million. However, during the first half of 2022 the ransomware attacks increased as there were a total of 236.1 million cases recorded worldwide.
Password Hijacking is another everyday cybercrime on E-learning platforms. A hacker can try hundreds of passwords within seconds to gain access to your personal account information. To prevent this type of crime, it is recommended to use a password that is comparatively hard to crack, one that has uppercase & lowercase letters, symbols and numbers. Utilizing a single sign-on service like Okta or OneLogin will also alleviate the risk of password hijacking. Password hijacking mostly occurs when passwords are simple dictionary words or names that are easy to crack.
Third-Party Providers sometimes facilitate online organizations in delivering valuable courses, but they can trick you into a large economic loss. Before sharing any sort of crucial information with them, their authenticity must be verified. A study found that 28% of victims were attacked by third-party provider scams.
Spoof Attacks Another cybercrime becoming more and more common in E-learning is email, caller Id, website, and text/SMS spoofing. Here, the fraudster steals an identity for malicious purposes such as to gain access to authorized data directories carrying malware viruses.
Social Engineering Attacks Tricksters use psychological manipulation to coerce victims into making security errors or give them other confidential and delicate information. In such cases, it’s common for a perpetrator to look deep into the victim’s background and gather all the necessary information before proceeding with the attack. After the attacker gains his target’s trust, the victim himself reveals all the critical information and resources to the criminal.
Digital Tools Used for Cybercrime in E-Platforms
There are a number of digital forensic tools available online which are used by criminals to maliciously obtain personal data for their own use.
Ophcrack: This free tool to crack passwords is commonly used by fraudsters. The inventor’s implementation of rainbow tables is considered very logical. Ophcrack runs on numerous operating systems and even comes with a graphical user interface.
EnCase: This software tool is traditionally used in restoring evidence from removable hardware. EnCase allows the trickster to conduct an in-depth analysis of user files to gather personal data such as documents, pictures, and registry information. The software comes in several custom configurations for cyber security, security analytics, and e-discovery use.
SafeBack: This software is used to create multiple copies of either the entire hard disk drive or a part of it. The tool is a process similar to photography in terms of taking a snapshot of the hard drive and making an exact replica of the data.
Data Dumper: Freely available, this tool is command-line software that can develop mirror copies of disks suitable for digital analysis and cybercrime.
Need to Employ IDV Solutions to Advance E-learning with Precision
E-platform scams and frauds have disrupted online education systems and should be counteracted as soon as possible. Most of the tricksters performing cyber crimes in online learning are students. Cybercriminals are increasingly targeting online education centers for their redundant benefit. Data breaches, identity theft, blackmailing, and document fraud are the most commonly occurring E-learning crimes.
Online education can be made secure by utilizing IDV Solutions to minimize the cybercrime threat. When seeking student registration in online courses, educational organizations are responsible for providing suitable identification methods to establish their genuine identity. Before being admitted to any online courses, educational organizations should undertake strict IDV measures such as facial recognition, voice recognition, and fingerprinting. A secure ID and password for all online registered students must be assigned to them for adequate security. A proctored examination should be conducted to ensure the student taking the exam is the one who enrolled for it.
How Shufti Can Help
According to recent crime reports, E-learning platforms are in a constant struggle to tackle these sophisticated crimes. As 24/7/365 online connectivity is consistently presenting challenges for online learning platforms to tackle cyber crimes, there is a sudden need for identity verification solutions. Shufti services can help overcome cyber-attack threats in a variety of ways.
Shufti offers services such as document verification, consent verification, facial biometric verification, and two-factor authentication which boost confidence in providing online educational services. Cyberattacks and identity theft can be controlled with ~99% accuracy with the help of Shufti. In addition, Shufti can screen cybercriminals with access to 3000+ identity documents in 150 different languages leveraging AI technology.
Ready to discover more about our KYC solution for your e-learning platform?

 Explore Now
Explore Now













