Elevated Business Security: A Comparative Analysis of Identity Proofing and Identity Verification

In today’s digital age, businesses must have a robust identity verification system in place that fundamentally helps them to protect themselves from advanced security threats. In 2023 alone, identity theft cost US businesses an estimated $56 billion, accounting for a significant chunk of the losses incurred by cybersecurity threats. While digitization has enabled companies to provide services to individuals from all parts of the world, it has also exposed them to an increased risk of digital fraud.
To effectively battle the increasing threat of cybercrime, it has become imperative for businesses to verify individuals’ claims by validating their identities. Identity verification solutions enable companies to safeguard their data and that of their customers from cybercriminals. These solutions are essential in mitigating the risks of identity theft and other financial crimes.
Identity Proofing vs Identity Verification: An Overview
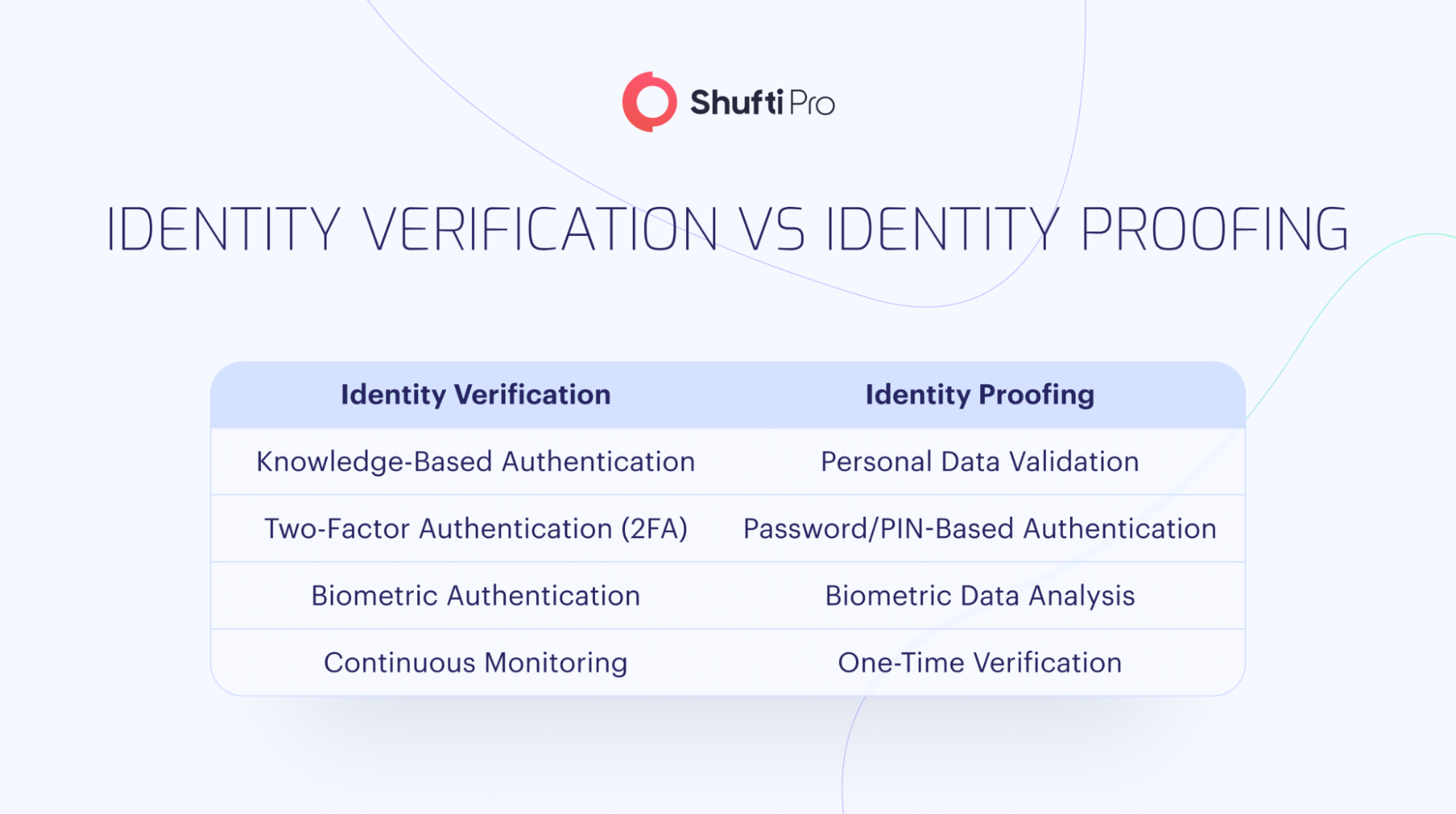
In general, identity proofing and identity verification are essentially the same processes, as their main aim is to confirm the authenticity of an individual who intends to establish a relationship with a business. However, these verification tests are different in terms of how they are conducted.
Identity Proofing is the act of demystifying the provided identity of an individual, verifying that the person attempting to establish a relationship with a business is who they say they are. This process can only be carried out using biometric data, document verification, and online authentication methods.
Meanwhile, online identity verification provides a comprehensive authentication solution for businesses that enables them to effectively verify various aspects ranging from identity to the source of an individual’s finances. The global identity verification market size is estimated at $ 13.10 billion in 2024 and expected to reach $23.73 billion by 2029, growing at a CAGR of 12.62%
Fundamentally, identity proofing and verification are two mechanisms that cater to a process known as Identity and Access Management (IAM), which essentially manages the verification of an entity and the access it has to a company’s procedures. IAM is essential to ensure the security of a company’s resources and protect against data breaches, fraud, and other malicious activities. It is also essential to ensure compliance with various regulations, including GDPR and PCI DSS, by verifying an individual’s identity.
The National Institute of Standards and Technology (NIST) explains the basics of an identity check by dividing it into two basic terms:
-
Claimed Identity
Users are required to provide personal credentials and information, such as a PIN, ID details, or other relevant data, during the registration process for validation purposes. The validation system uses the provided personal data to establish user identities for accessing sensitive information. Providing personal information is considered “claimed identity,” but there is a significant possibility of the data being incorrect or stolen, which can raise concerns about the user’s identity and security.
-
Actual Identity
Once the registration process commences, the information provided by the user is cross-matched against official government databases, which determines whether the information provided is correct. The term “actual identity” refers to a user’s valid and registered data, which is meant to be used for identification purposes.
While the difference between these two aspects may sound subtle and insignificant, there is actually a huge gap. Claimed identity comprises simple information, such as email addresses, with no mechanism to verify whether it is legitimate. Meanwhile, the actual identity is determined after an in-depth analysis and verification of the data provided by the individual.
Understanding Identity Proofing: The Basics
Identity proofing is the process of validating the data provided by a user to grant access to a specific function associated with the user. Identity proofing solutions aim to verify a user’s claim about their identity rather than relying on knowledge-based verification.
Identity proofing services have lower validation accuracy; however, they are viable for small processes as they require a user to provide documents to prove their identity. A general identity-proofing process can be divided into the following steps:
-
Resolution
In this part of the identity-proofing process, a user is prompted to provide personal information, which is then recorded. This provided identity data is then placed in the identity check solution to be verified.
-
Validation
The next step in the identity-proofing process is to validate the data gathered on an entity and establish a supposed identity. This step determines whether the data provided is legitimate and not incorrect and places it for further verification.
-
Verification
This last process in identity proofing involves verifying a user’s established identity based on the claims and data provided. Further proceedings involve verifying the gathered information for access granting, which keeps business processes safe and authorizes only verified users.
In contrast, ID verification is divided into five comprehensive steps, ranging from acquiring users’ accurate identity data from government databases to verifying it against global criminal records and sanctions. It offers companies a more secure verification solution than identity proofing and ensures that businesses remain safe from cybercriminals and fraudsters.
How Does Identity Proofing Differ from Identity Verification?
Identity proofing and verification differ in efficiency, with identity proofing being less efficient. One reason for the difference in verification requirements between a general verification firewall and a financial institution is due to the scale of the processes involved. Identity proofing may be sufficient for the former, whereas identity verification is necessary for businesses that require more security.
-
Personal Aspects of Users
A robust identity-proofing solution allows businesses to collect users’ personal data, such as name, address, date of birth, and social security number, which is then associated with the user to establish an identity claim. In a standard identity proofing use case, a user is validated just with the identity claim, whereas identity verification services go one step ahead and conduct an in-depth verification check on users.
-
Document Validation
In some cases, users must also provide documents such as a government ID or passport, which are used as an identity claim rather than manual data. However, in this case, there is a threat of fabricated documents and forged identities, which an average user cannot spot. Companies need to have a more advanced verification solution in place to effectively eliminate the threat of fake documents while validating a user.
-
Biometric Data Analysis
The utilization of biometric data, such as fingerprints and facial recognition, is becoming increasingly prevalent in efforts to enhance identity proofing. However, there is a significant threat of deepfakes that imitate the fundamental biometric features of a legitimate user. Identity-proofing solutions can effectively verify biometric features; however, they can fail at catching deepfakes and fabricated biometric features, which might expose a business to a significant cyber threat.
Identity proofing may not be as compliant with global regulations compared to Identity Verification (IDV), which ensures a company’s compliance with the rules of the jurisdiction in which it operates.
Identity Verification with Shufti: Enhanced Verification for Businesses
Shufti is a full-scale verification solution for businesses that enables effective user verification globally. Our services are available globally in over 240 countries and territories. Our solution provides a multi-level verification process, OCR data extraction in over 150 languages, and robust security firewalls that can instantly detect fraudulent IDs.
We help businesses navigate through complex regions, and our identity verification system maintains regulatory compliance. Our cutting-edge solution stands as an impenetrable fortress of identity verification. With our top-notch security measures, we ensure that no entity is granted unauthorized access.
Still unsure about how Identity Verification can help you enhance your security?

 Explore Now
Explore Now













