First-party, Second-party and Third-party Frauds – How to Stop them?

Most businesses don’t lose customers because of poor services but due to weak security measures. Criminals take advantage of security loopholes and carry on with their fraudulent activities. of this, fraud losses are increasing every year, leading to a tarnished brand reputation and massive losses for the victims.
According to the Association of Certified Fraud Examiners’ Report to the Nations of 2020, businesses lose an estimated 5% of annual revenue because of frauds. Criminals are smarter now and use technologically advanced ways of scamming. Businesses need to stay one step ahead of fraudsters to strengthen fraud prevention procedures. Today, businesses are using AI-powered fraud prevention solutions to safeguard data-sensitive channels.
What is the Most Reported Fraud so far?
According to the Federal Trade Commission, imposter scam was the topmost fraud of 2020. It received nearly 50,000 complaints, costing USD 1.2 billion. In imposter scam, the fraudster pretends to be some trustworthy individual, convincing the victim to send money.
Evolution of Frauds
There is sophistication in the way fraud is committed nowadays. Furthermore, new frauds have entered the digital landscape within the past fifteen to twenty years. With time, the frauds have transformed just like other gadgets and technologies.
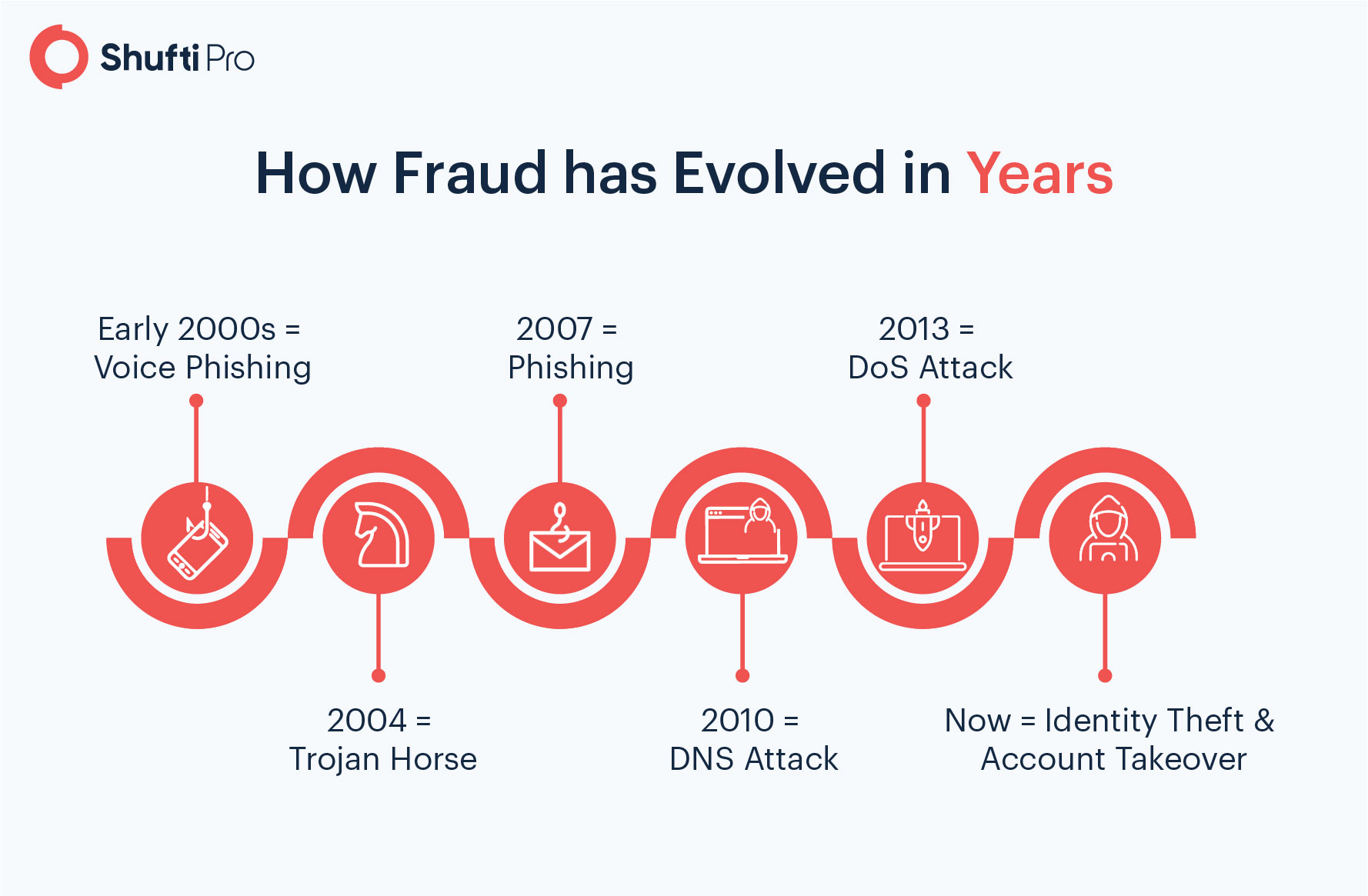
Voice Phishing in early 2000
Criminals use telephonic call mediums to impersonate a government official asking for bank account details or some other sensitive information. This is generally known as voice phishing or vishing. The success rate of this type of fraud was high in the early days but dropped as people became aware of it. Voice phishing scams are still happening. Countless cases were reported during the Covid-19 pandemic where fraudsters would pretend to be health organization’s representatives asking for sensitive information such as their medical insurance details.
Trojan Horse in mid 2000
Everyone who has watched Troy is aware of the Trojan horse, as it became the reason for the fall of the Greek’s powerhouse. In computing, it is malware concealed with legitimate software. For instance, a user downloads video editing software which in reality turns out to be spyware.
In late 2000, phone-based phishing attacks evolved into email-based scams. This is a type of social engineering, similar to voice phishing, but an email is sent instead of a phone call. Criminals usually ask for online account credentials or bank ATM pins through this technique.
2010 and Afterwards
The last decade experienced great innovations; wireless communication, AR (Augmented Reality), holograms or intelligent phones, and much more. On the downside, crooks also began using these types of technologies.
Today, there are organized numerous criminal groups that employ tech experts. They help in manipulating the location of computer systems using IP (Internet Protocol) masking. It becomes difficult for policing authorities to catch them as there is no valid IP address associated with them. IP masking makes DNS (Domain Name System) and DoS(Denial of Service) attacks easier to deploy.
Identity fraud is disrupting digital businesses currently. They are subcategorized into account takeover and identity theft. Later we will discuss both terms in detail.
To know more, download Shufti’s Global Identity Fraud Report 2020
Depending on their execution ways, frauds are divided into three types, here they are.
First Party Frauds
A person or group gives false and incorrect information while buying a product or applying for service in first-party frauds. The intention is to get free or low-cost services. It is done when fraudsters have the objective of not meeting their commitment.
When applying for a loan, a person lies about their financial details or job. They claim to have a high monthly income to receive a heavy loan. Another example is insurance fraud, where a crook files a false claim.
In chargeback fraud, an individual denies the purchase of an expensive order. In this case, the card issuer has to return the amount.
Second Party Fraud
In second party fraud, a person gives the authority to use his information for any illegal purpose. Second-party fraud is much more complex as compared to the first one because the information is correct and no one will report its misuse.
Money mules are the best and easily understandable example of second party fraud. People give their bank accounts to money launderers so that they can use them for washing ill-gotten funds. The accounts are used to create a cycle of transaction or funds transfer.
E-commerce sites suffer from this, individuals give their accounts to use for buying products online. Their friends or family members sign in from a different device, making the whole process look legitimate.
Suggested Read: Anti Money Laundering – What is AML compliance and why is it important?
Third-party Frauds
It involves the misuse of a person’s information by stealing their credentials to take over their account. Two examples can be mentioned here; the first one is identity theft and the other is account takeover.
Criminals steal data by hacking into databases or sending phishing emails. Banking accounts are mostly taken over because they can make money from them. Synthetic identity theft is also an associate example of third-party fraud where a blend of legitimate user data and fake user data is utilized. It is tougher to detect as compared to normal identity theft.

Fraudsters apply for loans through some other personal identities as they do not have to pay back. The real owner of that identity negates taking loan payments and the business suffers in the end.
Don’t Worry, Shufti is here
Shufti provides solutions for businesses to combat the rising number of frauds. Its identity verification service helps organizations to onboard authentic users only. It verifies the information of a user by confirming it through official identity documents. The user just has to upload an image of an ID card, driving licence, international passport, or other official documents to have themselves verified. Shufti verifies each end-user in only 30 seconds, with an accuracy rate of 98.67%. For online account security, businesses can also use 2-Factor Authentication provided by Shufti.
Businesses can have a better position in the market by using identity verification and fraud prevention solutions. Not only this, it will help stay compliant with global KYC (Know Your Customer) regulations.
For more information on identity verification and 2 FA, give us a call.









![Harnessing the power of AML Screenings to Uncover Politically Exposed Persons [PEPs] Harnessing the power of AML Screenings to Uncover Politically Exposed Persons [PEPs]](https://shuftipro.com/wp-content/uploads/n-img-harresing.webp)


