KYC/AML Compliance – An Anti-fraud Mechanism for E-wallets

As more and more countries had to enforce lockdowns because of the pandemic, remote working and dependence on online platforms became the new norm. This new manner of working, however, also led to a heightened risk of fraud in the financial services sector. Such frauds took multiple forms – identity thefts, account takeovers, money laundering, and more.
With criminals becoming empowered through the remote setting, the monetary nature of e-wallets made them highly susceptible to cybercrimes. While the USD 6.6 trillion industry is set to revolutionize how we make payments in the future, its regulation became necessary for the prevention of fraudulent activities. Therefore, in the same way as other industries, e-wallet firms are also required to comply with the KYC and AML framework as stated by global regulatory authorities.
What is an E-Wallet?
In simple terms, it is an online wallet for your smart device. To perform an e-wallet payment, a customer has to place their device near an NFC reader. Using NFC technology, the payment is made within seconds. Popular examples of e-wallets include Apple Pay, Android Pay, and PayPal.
The Emergence of E-Wallets
The growing customer acceptance of online platforms, development in the field of artificial intelligence, increasing demand for smartphones, the emergence of advanced technologies like 5G, and the growth of the digital payment industry are a few of the key factors behind the rapid emergence of e-wallets.
The COVID-19 pandemic also impacted the payment industry, accelerating the adoption of cashless transactions to avoid physical contact.
The following statistics represent the growth in the e-wallet sector:
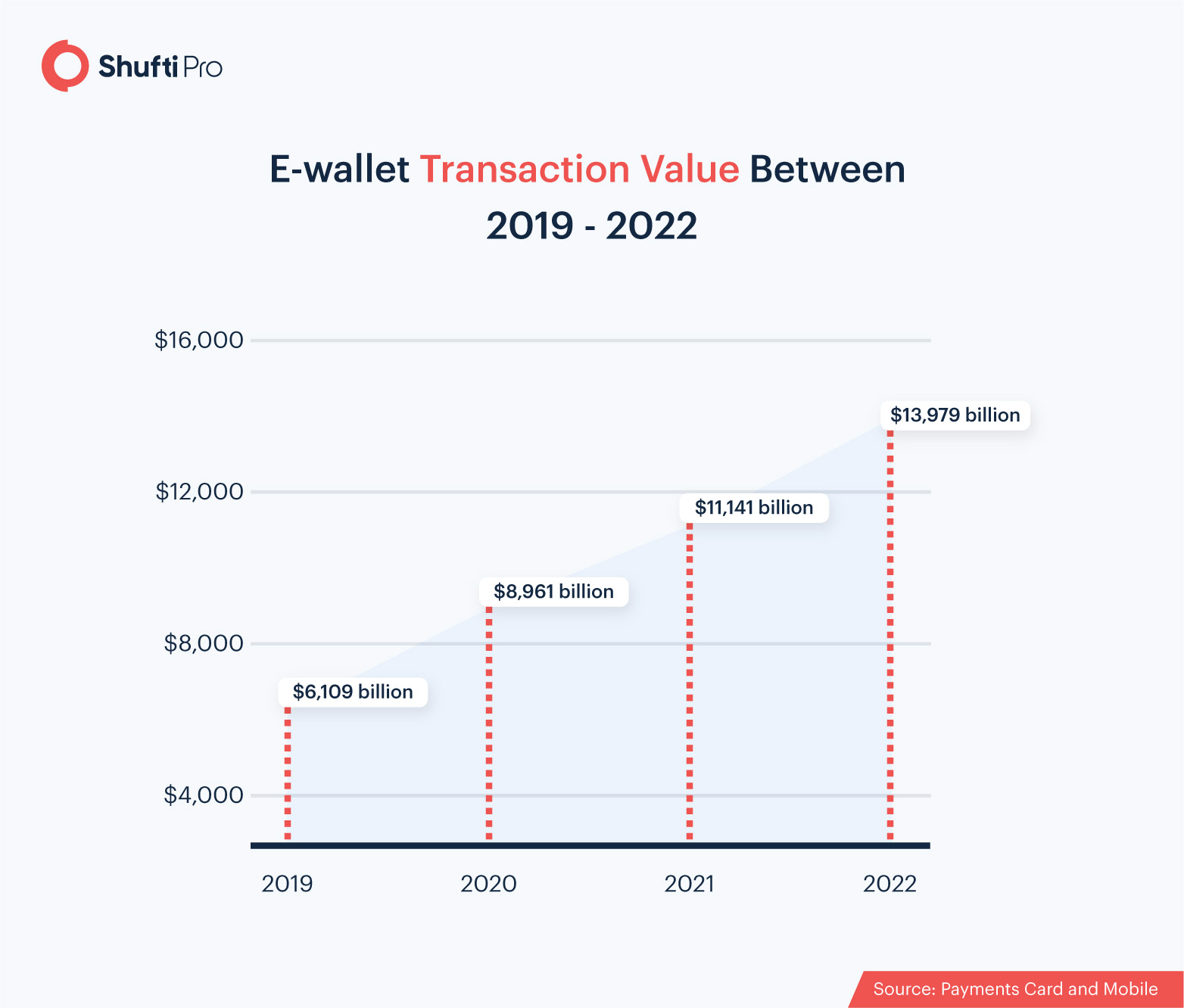
Digital Wallets and Fraud Prevention
The increased ease with which funds circulate through online channels is a double-edged sword. It has paved the way for bad actors – hackers, identity thieves, drug cartels, and even money launderers – to hide the source of their illegally obtained funds in plain sight. The United Nations revealed that the global amount of money laundered accounts for 2-5% of the GDP in a single year. According to the FCA (Financial Conduct Authority), approximately £100 billion is laundered each year through the UK alone. Considering this, robust and constructive anti-money laundering measures are imperative for businesses worldwide.
In the context of e-wallets, regulations regarding fraud prevention can be divided into two main groups:
1. E-KYC
Electronic KYC, abbreviated as e-KYC, refers to the remote verification of customer identities during the initial sign-up process. The process is implemented on an ongoing basis, triggered by events such as a customer performing large transactions or opening a new account.
2. AML Screening
AML compliance requires the background screening of customers against criminal watch-lists, Politically Exposed Person (PEP) lists, adverse media stories, and global sanctions.
Understanding E-KYC For E-wallets
The goal of an e-KYC process is to verify the true identity of customers using an e-wallet application. As a result, customer-related risks are evaluated and analyzed. This process not only ensures maximum security but also allows an e-wallet firm to avoid hefty fines and penalties due to KYC/AML non-compliance.
The basic e-KYC process covers the following:
- Identity Verification – to verify a customer’s Personally Identifiable Information (PII)
- Identity document scanning – to verify and authenticate the information provided in the registration form
- Liveness check of the customer – to weed out imposters
During this process, an official identity document is verified to rule out the following:
- Expired ID documents
- Modified ID documents
- False or stolen documents
- Invalid ID card formats
E-wallet service providers also use biometric facial recognition to their advantage, adding an extra layer of security to the e-KYC process. With the help of liveness detection, the customer using an e-wallet is verified by analyzing their live presence. This involves the detection of facial expressions, eye movements, etc. to identify potential spoof attacks by criminals.
Risk-based Approach to AML for E-Wallets
The FATF has laid out a risk-based AML/CFT framework which all the member states are required to implement. Under this regulation, e-wallet service providers are obligated to conduct a risk analysis of every customer to rule out potential criminal threats. In practice, AML compliance procedures of e-wallets should include the following measures:
1. Customer Due Diligence
CDD checks are carried out to verify the identity details of the customers. This involves the verification and authentication of the customer’s full name, address, date of birth, etc. For customers assigned with a high-risk rating, EDD (Enhanced Due Diligence) measures need to be implemented.
2. Transaction Monitoring
To identify suspicious activities that may be indicative of money laundering, e-wallet service providers should monitor customer transactions. In the case a suspicious transaction has been detected, the firm has to file a Suspicious Activity Report (SAR) to notify the authorities.
3. Ongoing Screening
E-wallet firms need to eliminate the risks of reputational and financial damage by performing ongoing customer screening. During this process, the e-wallet users are verified against global sanctions and criminal watch-lists. This process is necessary for the identification of red flags, such as:
- Discrepancies in the customer identity verification process
- Unusual transaction patterns
- Suspicious transactions by PEPs
- Frequent international transfers following deposits being made into e-wallets
- Multiple account registrations
The Value Proposition of KYC/AML for an E-wallet
The replacement of hard cash as the preferred method of payment is not a regional phenomenon – it is a trend emerging on a global scale. More and more consumers are foregoing the use of paper-based cash and opting to pay through their smartwatches, contactless cards, or e-wallets. Here’s what the global picture looks like:
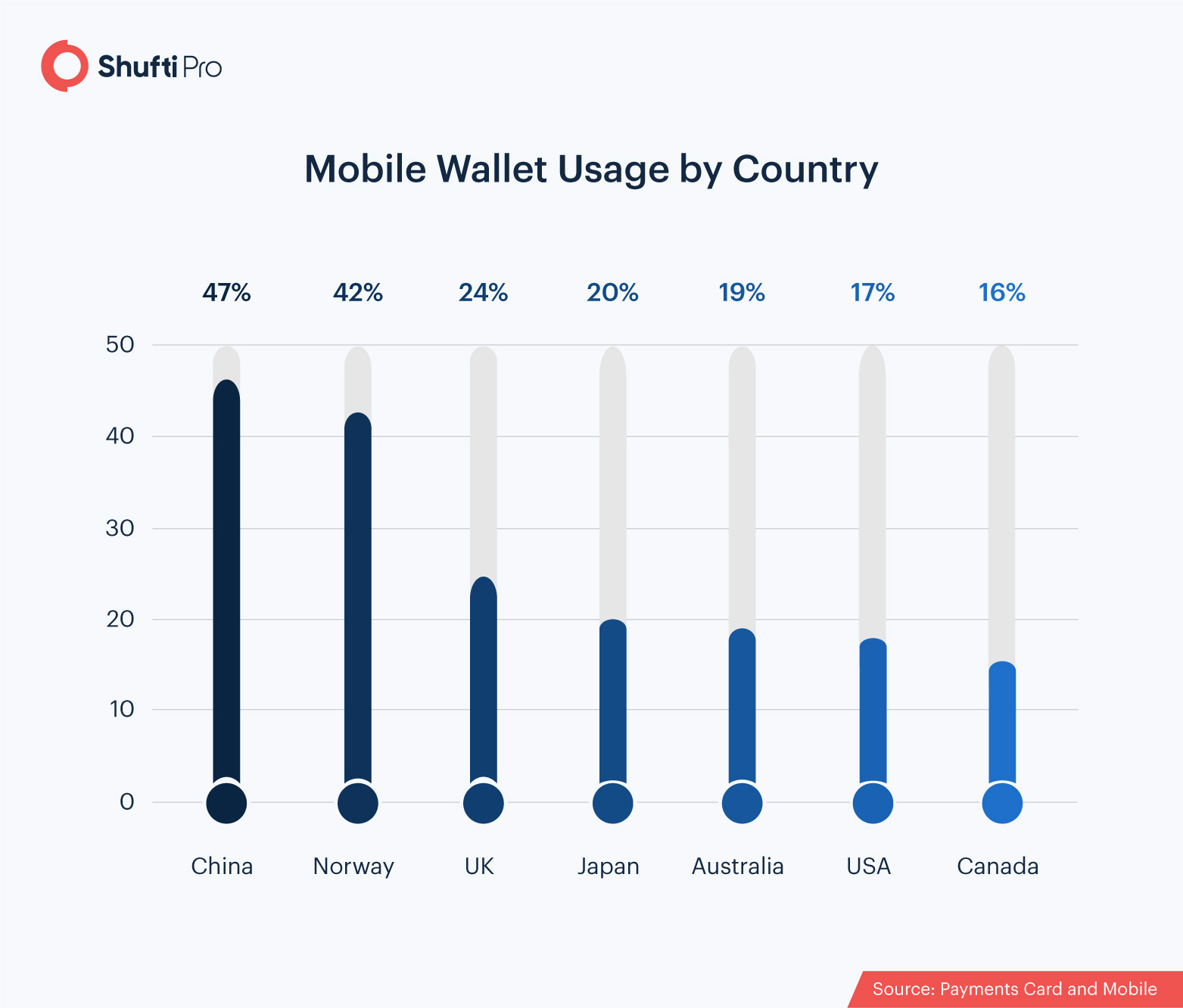
With e-wallets processing billions of payments worldwide, securing online transactions has become more critical than ever. With the help of KYC and AML monitoring solutions, all the involved parties can avoid becoming the victim of criminal players. Additionally, biometric facial recognition should be employed by e-wallet providers for real-time identity verification, fraud detection, and conformity to global KYC/AML compliance standards.
Want to learn more about how e-KYC works? Get in touch with our experts right away!

 Explore Now
Explore Now













