Online Identity Verification – The Hallmark of Surviving the Digital Upheaval

Embracing the digital world seems like entering uncharted waters where the challenges are novel, and the aftermath is unpredictable. Although, part of this may not be true, there do exist certain challenges that enterprises need to address to make customer experience purposeful and the digital space a safer place. The dawn of intelligent technologies like artificial intelligence and data science has opened new roads of innovation in customer relationship management despite the constant risk of cybercrime.
This blog discusses the importance of user identity in the digital space, the challenges associated with it, and what solutions companies have to offer in this regard.
Digital Identity – Why is it Such a Big Deal Today?
When we talk about the digital space, there are a lot of things to consider apart from quick digital transactions to opening online accounts safely. What is of essence is that any user browsing the internet, or using online services to buy products has a unique identification often called their digital identity. According to the UK’s Trust Framework, this is a representation of a person in the digital space allowing them to establish an identity to interact online. Digital identity is composed of trusted pieces of information called ‘attributes’ that are chunks of personal data such as the name, address, date of birth, etc.
While digital identity can work wonders, it has its fair share of challenges that need to be addressed. Businesses invest a lot of time and resources to come up with efficient and reliable solutions that guarantee their customers are safe from identity theft and various other cybercrime.
A Day in the Life of an Online User
From responding to online messages and using free Wi-Fi at the airport, to downloading apps and stumbling across phishing emails and data breaches, the digital space is full of challenges. Users in the digital space may acknowledge that they can blissfully browse their social media feed and give out their personally identifiable information (PII) to buy products from an e-store, but it is important to know that all of this does not come at the cost of compromising their identity information.
Who knows, your stolen online records may end up on the dark web without you even knowing, or the security code which you just shared on email ends up in a credit card breach? Consumers should take care while handing out their identity information particularly in the digital space that is full of unwanted actors.
The Importance of Positive Digital Footprints
The trail of information that a user leaves behind while sharing and interacting on different platforms in the online landscape is called digital footprints. It may include information that is actively shared online such as signing up to open an account, making a purchase, or putting in your credit card details for authentication.
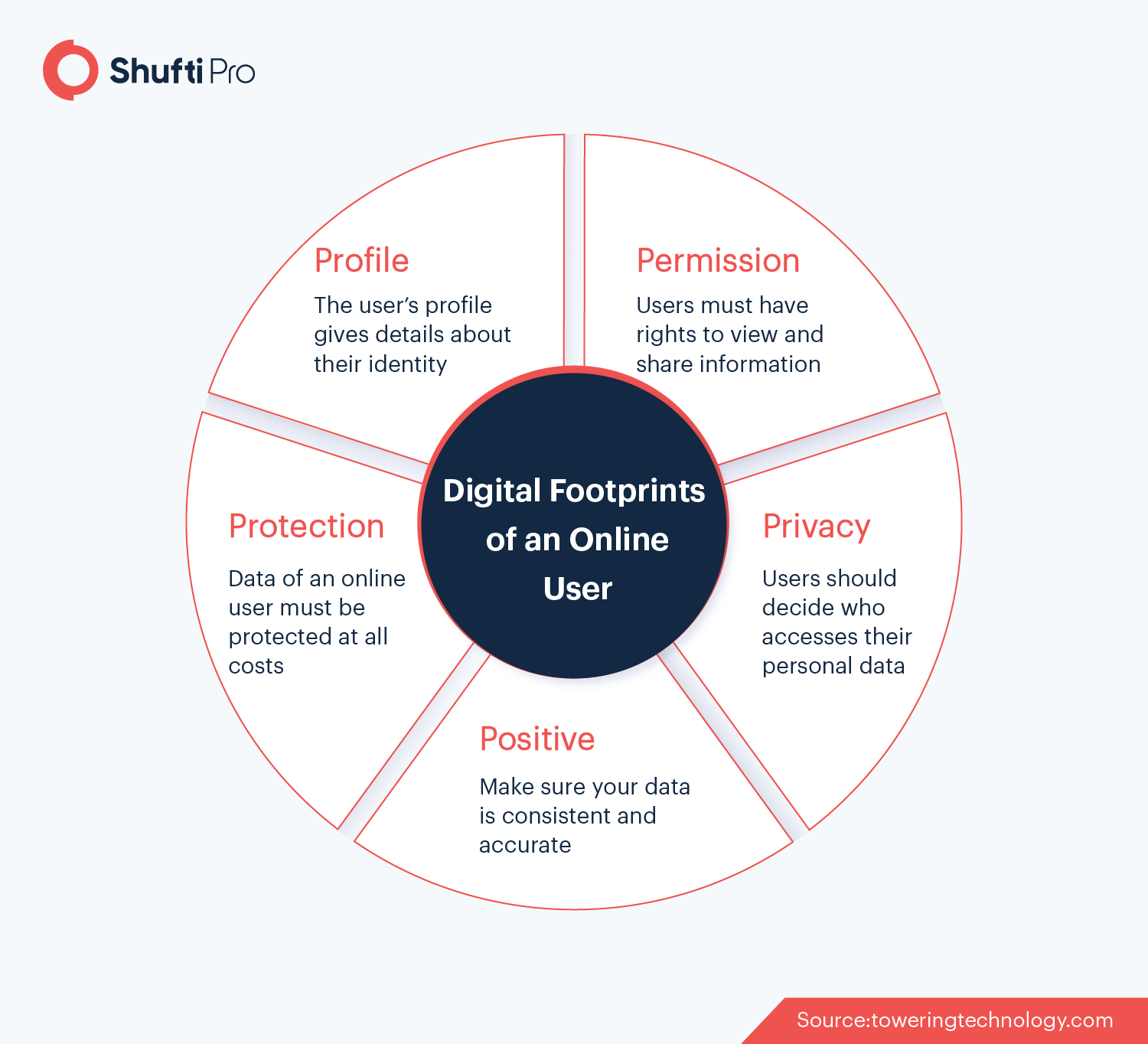
When it comes to businesses, unidentified digital footprints could result in criminals using false identities to open fake accounts, and use business services for money laundering, identity theft and related financial crime. Performing thorough screening of customers in light of robust due diligence regulations can help address this problem and allow effortless identity verification.
Challenges in the Digital-only World
Identifying and Verifying Customers
Whether your business operates physically or in the digital space, it needs to have a mechanism to make sure that any customer they onboard is legitimate. In corporate and banking terms, this is called Know Your Customer (KYC) through which organizations mitigate financial crimes such as money laundering and tax evasion.
With technology emerging, digital KYC is becoming popular in the market with intelligent facial recognition and AI-based document checks. Through these solutions, the identity of an online user could be analysed in detail with minimum effort and time by taking into account digital footprints and relevant data from user ID documents.
Protecting Children from Online Harms
You cannot stop children from using the internet, but supervision does help in this regard. When we talk about safeguarding minors from online harms, parents are not the only ones responsible. Businesses also have the moral and social obligation to make sure the privacy and security of children’s data is their top priority.
The recent Milestone Online Safety Bill by the UK government highlights issues regarding fake identities used by cybercriminals to deceive minors in giving out their personal data. In order to combat financial fraud and social media scams, it states robust measures to make the internet a much safer place for children.
There are certain service providers on the internet that sell age-restricted products which are not appropriate for children. These businesses may oftentimes need a digital age verification solution to help them comply with age specific-laws, helping them create a better brand image too.
Staying Compliant with Regulations
Operating in the digital space is not easy as it comes with a lot of responsibilities, one of which is stringent Anti Money Laundering (AML) obligations by regulatory authorities. These are mandatory for financial organisations since they are always on the verge of potentially ill cybercrime instances.
Considering this, compliance may not come at the cost of compromising user experience. This is why businesses have to maintain a fine balance between abiding by the rules and performing effortless onboarding and customer verification.

Surviving the Intense Market Competition
Digital adoption has become the need of the hour. In today’s technology-driven world, a business cannot survive without innovation. Companies are investing huge sums in technologies like Artificial Intelligence, Big Data Analytics and Machine Learning to outsmart their competitors using state-of-the-art methods. All this is essential for customers to enjoy a seamless experience while opening accounts and performing transactions at the comfort of their home through digital identity verification.
Why Digital Identity Verification is the Way Forward?
Since, today many businesses have turned towards the digital landscape amid the COVID-19 restrictions and the increased consumer demand, identifying who is a legitimate customer and who not has become even more significant. Shufti’s digital identity verification services powered by enhanced AI technology deliver accurate and quick results for real-time customer onboarding.
Recognising the needs of the digital space, Shufti has made its client-centric IDV solutions available in over more than 230 countries and territories with an additional free trial of 7 days. Apart from that, omnichannel integration, customized hosting page services, and a knack for an effortless customer experience makes Shufti different from other players in the market.
Have more questions? Get in touch with our experts.











