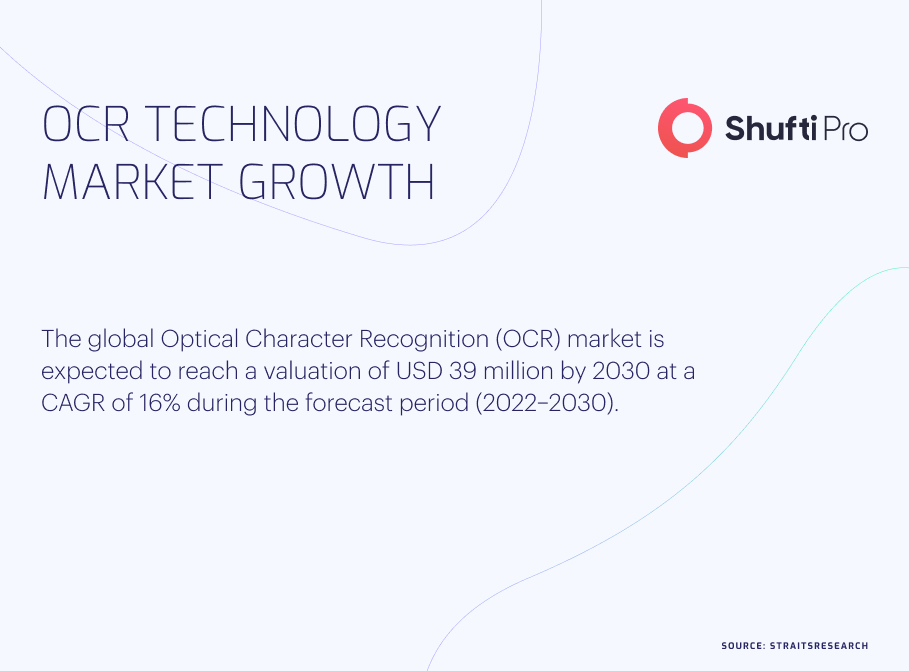
Optical Character Recognition (OCR) | Pushing the Boundaries of Data Extraction

There is a surging demand for swift and remote identity verification methods in our digital world where automated technology is taking over business operations. An online KYC check involves the support of artificial intelligence to detect fraud instances whilst helping businesses meet compliance and removing friction from onboarding procedures.
However, when it comes to practising Know Your Customer checks, companies mostly manually verify documents or use them with limited automation. This paves the way for fraudsters to manipulate the verification systems, further entailing inaccuracies in customer verification data and increasing friction in the onboarding journey. This is where OCR technology can help. Involving technology like Optical Character Recognition (OCR) aids the whole process and backs AI to completely automate identity verification, making it reliable, time-efficient, and instantaneous.
The History of Optical Character Recognition (OCR)
The optical character recognition OCR technology traces back to telegraphy in the 1900s. Emanuel Goldberg, a famous physicist, invented the first OCR scanner during the first world war. The machine was capable of recognising and converting the characters into the telegraph. In 1920, Goldberg made another breakthrough in OCR and went one step further and built a document retrieval machine, the first of its kind the world had ever seen. At that time, recovering data from film spools was impossible, but made possible with this invention.
In the 1970s, Kurzweil Computer Product was founded by Ray Kurzweil, who launched OCR products that could read and recognise printed text in almost every kind of font present at that time. The founder believed that the most significant use of OCR technology would be to help differently-abled people, particularly the blind, so the company’s products were developed to assist blind people in reading text aloud in a text-to-speech format. However, in 1980, Kurzweil Computer Product was sold to Xerox, as the company saw the potential to advance paper-to-computer text conversion and acquired it to further commercialise the OCR technology.
Before OCR technology got the world’s attention, manual data extraction and retyping was the only way to convert paper-based documents into electronic format. However, this process was time-consuming and led to many typing errors and inaccuracies.
Optical Character Recognition (OCR)
Waiting and delayed time rounds may have a multitude of ramifications and customer experience is one of the impacted factors. Let’s take an example of bank account opening, where the user experience benchmarks are set sky-high. To do so, an array of customer data is required to verify identity, which, if done manually, could take a week to process. However, the fast-paced world demands that the account opening process should be swift and transparent, with no surprises. This is where OCR technology needs to leverage, making procedures as per customers’ demands.
Optical character recognition is a way to process handwritten or printed documents and convert them into digital copies. OCR scanners’ performance depends on the quality of text and system. Neural networks have the ability to localise symbols, text, and characters, empowering businesses to extract data from documents in real time.
In traditional optical character recognition systems, the decision-making is in the hands of system engineers; however, in AI-backed OCR scanners, the decisions are made by neural networks and machine learning algorithms that mimic the analytical behaviour of the human mind. These algorithms are trained on millions of data instances – the larger the data set, the better the model works.
Let’s Take a Closer Look at the Inner Processing of OCR
Pre-Processing: When the users provide images of their identity documents, the OCR technology perfectly enhances the photo. It improves the quality of the provided image, removes the distortion, and fixes the unwanted noise to ensure the highest level of accuracy.
Text Detection: Once the ID document photo is pre-processed and set as per standards, the OCR thoroughly scans the document to detect and spot the hidden text using advanced techniques like edge detection.
Character Segmentation: OCR breaks the text into characters, known as segmentation, after detecting text spots. It’s like solving a puzzle, parting the one big thing into smaller pieces to understand accurately. This is the most essential part of the OCR as it prepares the image for data recognition.
Character Recognition: At this phase, the powerful AI and machine learning algorithms empower the OCR system to recognise each character separately in the segmentation stage. OCR scanner uses its capacity to decipher special patterns, shapes, or curves, converting them into readable text.
Post-Processing: Last but not least, the OCR system does not stop at character recognition, but at this phase, the scanner automatically searches for spelling or formatting errors to resolve them, ensuring the highest level of accuracy and readability.
Challenges & Limitations of OCR
The IDV industry is undergoing significant changes; companies are trying to enhance the processes by combining technologies like OCR. On its front, OCR technology comes with some limitations, which include:
Data Structuring
Whenever a customer uploads a picture of handwritten or printed documents, various steps are required to extract the essential information. The first and foremost step is ID document verification e.g. driver’s licence, ID card, or some other government-issued documents. To do so, OCR technology is leveraged to properly structure the information, which requires a search for fields businesses need to extract. The basic version of OCR with any other supporting technology like AI will need more accuracy to verify customers whilst ensuring state-of-the-art customer experience.
Image Rectification
When a client takes a photo of their identity documents, the images must be de-skewed if the photo is not perfectly aligned and reoriented so that the OCR technology can precisely extract the data, helping companies verify the personally identifiable information properly.
Coloured Background
OCR Solutions with empowered technology works well with grayscale photos as it easily converts them to a plain, black-and-white background, reducing the likelihood of blurry text and separating it from the background. However, if the documents are on a coloured background, the results may be inaccurate.
Glare & Blur Images
For businesses, receiving glared or blurred document images are ubiquitous. Whenever there are distorted images of blurriness in the ID photos, the probability of extracting data precisely becomes challenging, further increasing the risk of getting inaccurate verification results.
Photos Via Webcams
Optical character recognition poses another big problem for firms, particularly financial institutions, trying to offer their customers an omnichannel experience by letting users take photos of identity documents using web cameras in real-time. While most webcams cannot capture the picture at high resolutions, it can impact the accuracy of the data extraction process, increasing the risk of mistakes caused by OCR scanners.
Some ID Subtypes may Challenge OCR
The OCR scanners are trained based on thousands of machine learning and neural network algorithms that empower the OCR systems to recognise and characterise identity document types. However, if the OCR scanner is not perfectly attained on multiple data sets, it becomes a challenge for the scanners to categorise sub-types of identity documents. OCR is only useful if it’s loaded with the right actions and can extract data from any document.
OCR Technology at Shufti
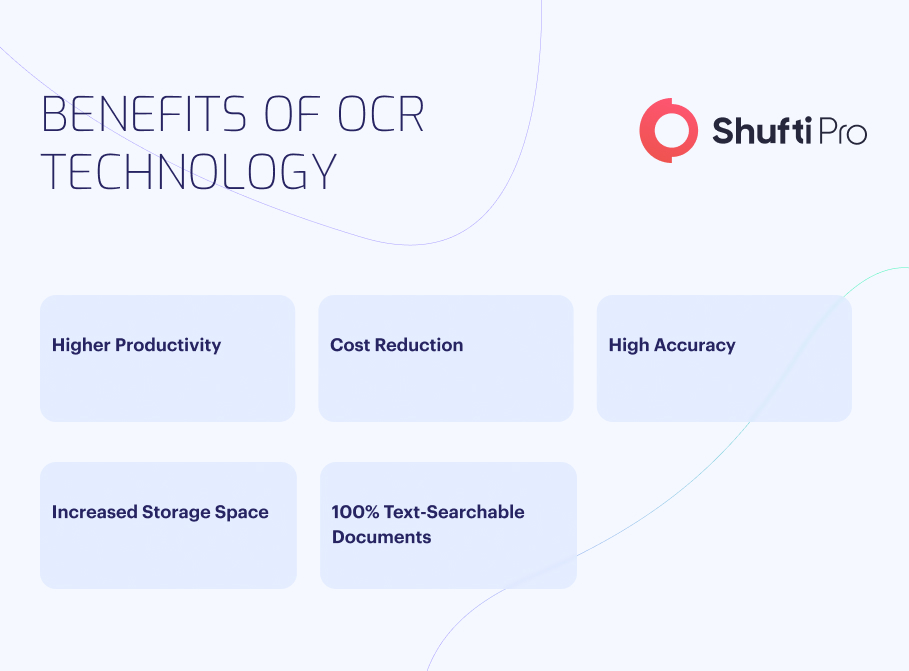
Since its inception, optical character recognition technology has been developed to extract data from different documents. OCR scanners are being employed across multiple industries, rendering various benefits, including automated data entry, information extraction, higher data processing speed, increased operational efficiency, and streamlined onboarding.
Shufti, a pioneer in providing identity verification services, used OCR technology as the core of the customer ID authentication process. Using automated OCR-powered KYC solutions, businesses can determine whether the identity data is legitimate or whether fraudsters are trying to manipulate the verification system. Shufti’s advanced OCR technology is leveraged with AI models that make it capable enough to extract text from identity documents in a matter of seconds. To verify the customer identity, our solution allows users to use the smartphone camera to take pictures in real-time or just upload pre-captured images. Rest the OCR-backed KYC verification works wonders.
Here are the key features of Shufti OCR Engine:
- Instant image-to-text data extraction
- Supports multilingual documents
- OCR Scanning for structured and unstructured documents
- Global coverage for 150+ languages
- Achieve unmatched accuracy of 90+% with Shufti’s OCR technology
- Access and download the extracted data (in the required format .pdf, .xlsx, .doc, etc.). Available on cloud storage
Want to see our OCR technology in action?











