Safeguarding Telecommunication Industry with Robust ID Verification Solutions – What Shufti Offers

Technology transformation, growing transactions and global digitisation are increasing the potential risk for cyberattacks on the telecom industry. The total dependency of telecommunication service providers (TSPs) on digital solutions, the internet, wireless networks, and IP addresses can provide fruitful opportunities to commit illicit acts. However, suspicious activities or businesses found guilty can put TSPs into legal sanctions, fines and compliance-related issues.
Historically, many telecom businesses have responded to such matters by analyzing the situation based on data collected by various geographic locations or departments. For instance, when the TSPs determine potential fraud, an investigation team may be created to investigate the likelihood and scope of a bogus scheme. For a variety of reasons, this approach seems to be inefficient to fight modern crime schemes. Therefore, to help the telecom industry, FinTech companies are coming up with AI-powered anti-fraud and identity verification solutions that aim to ensure legit entities get serviced while overcoming the risk of scams.
Telecommunication Industry [Overview 2022]
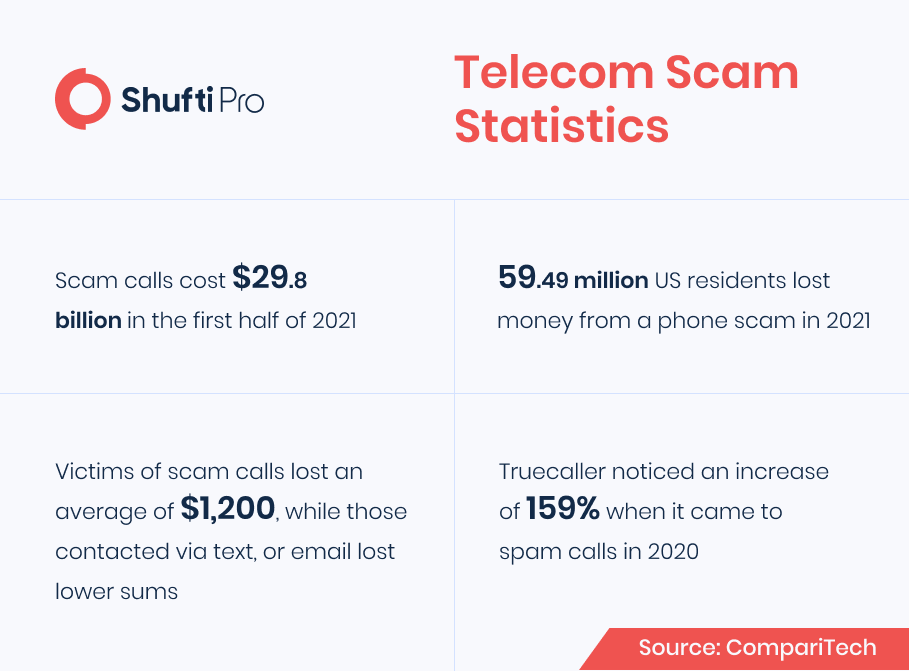
Like every industry, the telecommunication sector is also under the stress of criminal activities. Telecom scams including international phishing attacks, traffic pumping
interconnect bypass fraud, and various others have been highlighted as the greatest cause of revenue loss, with figures averaging between 3 to 5% of businesses’ annual profits. In addition to this, the global loss accounts for $55 billion annually, making the telecom scams a bigger business than international drug trafficking. According to the IDC estimates there are around 200 various types of fraud that exist, but the number is increasingly growing with the emergence of new technologies.
However, telecommunication scams are becoming sophisticated, making it hard for businesses to counter them precisely. The present regulations provide minimal protection measures to curb illicit activities. Whereas, many telecom service providers remain silent and do not report fraud for fear of undermining clients’ trust along with confidence in the security of their own services. In addition to this,
Spanish Cops Bust SIM Swap Fraud Gang
The country’s law enforcement authority reported arresting an organized crime group for sim swapping fraud, the technique used to get unauthorized access to victims’ bank accounts across Spain. The police published that eight cybercrime gang members were arrested based in Catalonia and Seville and their 12 bank accounts were also blocked. However, the investigation started in March 2021 when the law enforcement authorities received multiple complaints from the public that they had determined unauthorized access or suspicious activity on their bank accounts.
According to the Spanish Police, the gang members pose as bank representatives, using malicious links to trick victims into sharing personal as well as financial information. The sensitive data included credentials, credit card pins and ID card numbers. This appeared convincing enough for the telecom service providers that they were legit customers. By practising the tried-and-tested SIM swapping technique, criminals requested the victims’ mobile numbers be replicated to a new sim with all controls. By doing this, they easily log into the bank accounts, receiving 2FA codes, enabling them to gain access and get hands-on with their funds.
NY Individual Pleads Guilty in $20 Million SIM Swap Theft
An individual from New York was suspected of helping to steal more than $20 million worth of cryptocurrencies through wire fraud. In addition to this, the criminal was also part of an organized crime group that was alleged to have stolen around $100 million from cryptocurrency investors through the SIM swapping technique, in which the cybercriminals gain access to the victim’s phone and use that to take over targeted entity online identities along with financial information. The law enforcement authorities stated that the fraudulent SIM jacking is frequently abused by criminals who intend to exploit telecom service providers by tying a victim’s phone services to a new SIM card so that they can control their mobile phones. Unauthorized SIM swaps are committed by cybercriminals who already have access to victims’ sensitive information. However, as many financial firms and digital service providers mostly rely on two-factor authentication, the criminals get the multi-factor codes and can through security measures seamlessly.
United Kingdom’s Telecommunication Sector Regulations
Telecom law and regulations in the UK are particularly driven by Communication Act 2003 (CA 2003). The Act is a replacement for the Telecommunication Act 1984. There are the basic laws that set up the Office of Communication (Ofcom) as a regulatory body to regulate the UK’s telecommunication industry. However, instead of providing the licenses to the communication service providers under the Telecommunication Act, the new law governs mobile service providers by means of general authorization based on the conditions of the market in which they are operating.
This legislation enforces various European standards aimed at unifying, simplifying and enhancing telecommunication laws across the EU member states. CA 2003 also gives power to the Ofcom, which is the prominent regulatory body governing telecom service providers in the UK. The role of Ofcom is to develop and enforce laws associated with the telecom sector, along with the Competition and Markets Authority (CMA), to promote fair competition among the telecommunication service providers by implementing such laws.
Additionally, as a critical part of Ofcom’s regulatory standards, the department needs to take an approach to intervention and will only do so when it’s evidence-based, consistent and transparent. Furthermother, the regulatory authority is also answerable to Parliament. The Department for Culture, Media and Sport (DCMS) is the government department that is responsible for establishing a telecommunication regulatory framework within the country. Moreover, Ofcom has also proposed a 2021/2022 plan of work that focuses on ongoing investment in enhancing the mobile network quality across the UK, ensuring individuals and companies are serviced justly while making efforts to govern online harmful content to safeguard the locals.
How Shufti Can Help
The telecom sector and communication service providers are being challenged by cybercriminals and finding it hard to curb reverse engineered scams. Due to this reason, online accounts and financial wallets are more likely to get breached. Thus, the credibility, as well as the reputation of service providers, is at stake.
Shufti’s identity verification services are an ideal option for the telecommunication industry as it allows mobile service providers to identify clients’ real identities before getting them on board. Powered by thousands of AI algorithms our solution can authenticate with 98.67% accuracy in less than a second. In addition to this, the telecommunication service providers can also make risk assessment reports of high potential risk clients.
Want to know more about Identity verification services for the telecom industry?