Strong Customer Authentication (SCA) – Factors, Methods, and Benefits

In Europe, new customer authentication requirements for online payments were introduced on September 14, 2019. These requirements were part of the Second Payment Service Directive (PSD2) which are expected to be enforced by 2021. As per news by SiliconCanals, the internet commerce of the EU is expected to grow about 1 trillion dollars by 2022 and along with this, online fraud too. According to the European Central bank, every year online fraud on the EU cards is estimated to be about €1.3 billion. The increasing incidences of online payment scams call out stringent regulations in place that could help curb the fraud density.
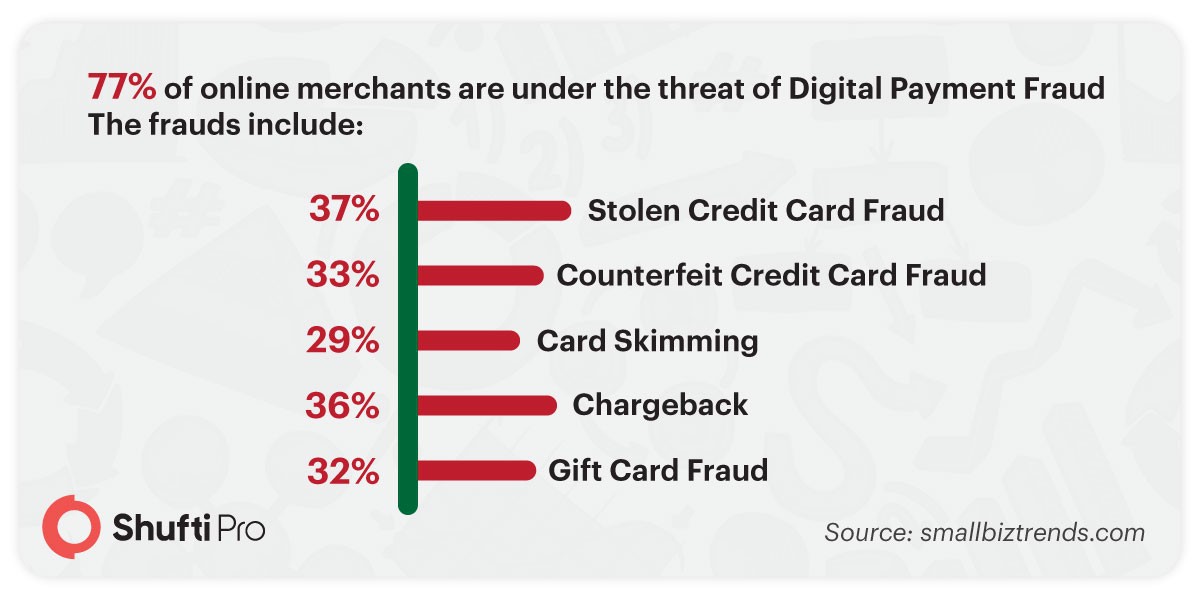
Digital payment scams and fraudulent transactions increase friction in the digital environment that ultimately becomes the reason for the reduced number of online conversions. According to a survey, 77% of online merchants are under the threat of digital payment fraud. These list of frauds include stolen or counterfeit credit card fraud, card skimming fraud, false chargebacks, and gift card fraud.
What is SCA?
Stronger Customer Authentication or SCA applies to customer-initiated online payments which means that SCA covers all bank transfers and digital card payments. The purpose of SCA is to provide stronger authentication in the checkout process regarding online payments and customer authentication.
Stronger Customer Authentication or SCA applies to customer-initiated online payments which means that SCA covers all bank transfers and digital card payments. The purpose of SCA is to provide stronger authentication in the checkout process regarding online payments and customer authentication.
Elements of Strong Customer Authentication (SCA)
The authentication process should include two of the following attributes (which is also known as two-factor authentication):
Knowledge: It corresponds to something that the user knows. For example, it could be the PIN, passwords, or any secret key required to access the account.
Possession: It is something that the customer has. For example, it could be a smartphone, token, or a smart card.
Inherence: It is something the customer is. For example, biometric elements such as face biometrics, voice patterns, fingerprints, etc.
Lack of authentication measures in place can increase the number of credit card fraud that comes up with multiple facets.
To protect the online payments and transaction processes, it is crucially important for organizations to employ stronger authentication mechanisms as per the recommendations by EBA. It states that the person who is claiming to be some identity is actually the person to whom that particular identity was assigned. Thus identity verification requires any of the two aforementioned elements for successful verification of an online identity.
Among these SCA elements, two are considered that questions the user what he knows and what he has. These two attributes correspond to the PIN, password, or 2-factor authentication that is based on an SMS which is been sent on the mobile number of user for verification purpose. However, these methods are prone to cyberattacks, large scale data breaches, and phishing scams which can be mitigated by including another SCA attribute that is “who the customer is”. With this, customer identification can be done through biometric verification that aligns with the need of verifying “the customer is who he claims to be”.
Accomplishing SCA through Biometric Verification
Biometric attributes such as fingerprints, face, iris/retina, voice, and similar unique biological traits are the strongest modalities of customer authentication. The increase of biometric technology on smartphones, thus, has made it possible to verify the online customers performing digital transactions. Biometric authentication verifies the customers against their facial biometrics. The facial features are detected and verified against the information stored in the database previously at the time of account registration.
The Biometric verification process ensures SCA while keeping intact the seamless customer experience and high online customer conversion rate. Biometrics eliminates the overhead of remembering PINs and passwords, provide high-end security over user accounts, and a robust authentication process.
Benefits of SCA
In this globally digitized world, there is a wide array of challenges among which digital accounts security and customer experience are the primary ones. SCA, therefore, provides the following benefits to cope with them in an effective manner:
- Reduces the damage of fraudulent transactions
- Secures digital payment services
- Reduces the potential of online payment scams and frauds
- Ensure PSD2 compliance
- Increases the confidence of cardholder in using online payment services
SCA requires advanced identity verification measures that could verify the identity of customers online in an efficient way, secures the digital payments services platforms against an array of digital frauds, and enable digital financial businesses to secure customer acquisition along with a high online customer conversion rate.
Key Takeaways
Strong Customer Authentication (SCA) is employed by customer-initiated online payments, including banks and digital payment platforms. It was first introduced in 2019 in Europe after the digital payment systems experienced a significant rise in crimes. Strong customer authentication (SCA) elements must include two of the three major ones; knowledge, possession, and inherence. Biometric authentication is a great step in identity verification and attributes like fingerprints, face, iris, voice, and other biological traits can make the strong customer authentication process more robust.

 Explore Now
Explore Now













