Why Digital Identity Verification is Booming – A Detailed Insight

According to the report “Digital Identity & Document Verification Market & Technology Analysis & Forecasts 2019-2024”, services of digital identity and document verification are estimated to be a market of $15 billion by 2024. Goode intelligence says that the estimation is a 20% increase in the global market as compared to 2019. There are several perspectives that are fueling this growth. Among these, one is the increasing digital frauds due to which businesses face several issues. The second being identity verification a requirement by local and global regulatory authorities.
What is Digital Identity Verification?
A process of identifying the digital identity of an individual. It ensures the authenticity of an online user by verifying personal and biometric information. The identity verification process is conducted to facilitate the provision of services and entitlement.
Identity verification is performed to verify each identity that is becoming part of your system. It is important to deter the risks of digital fraud by capturing, verifying and recording user identities. Lack of digital identity verification practices result in heavy monetary loss and are vulnerable to business reputation.
From Manual to Digital Identification
Previously banks and other financial institutions used to verify onboarding identities manually by verifying them against documents and biometrics. Traditional verification practices are time-consuming and require additional human power. On the other hand, it is hefty for customers to wait in queues for hours. But, it is not less than a challenge to ensure business security from bad actors in digital platforms. Either it is a bank or any online business, its digital problems need digital solutions that are now available in the form of digital identity verification.
With the advent of digitization, there is a need to take advantage of AI and ML technologies and its algorithms to automate the verification process. The integration of technology-based API with online systems ensures identity verification of each onboarding identity in real-time. Just to make sure that no unauthorized or suspicious identity becomes part of the legitimate system, identity verification is performed at the time of account registration and sign-in.
Factors Fueling Growth of Identity Verification Market
Small and Medium Size Enterprises are experiencing high risks frauds in the form of cyberattacks. These businesses either limit the scope of business services but need to cater to a large population. A bad actor can ruin the seamless business processing with its malevolent activities. Large enterprises hold a higher identity verification market share. However, SMEs lack digital solution integration for fraud prevention due to financial constraints. Although being KYC and AML practices, a regulatory requirement, small businesses are moving towards integration of identity verification services into their system that automatically verifies each onboarding identity without compromising user experience.
Identity Theft
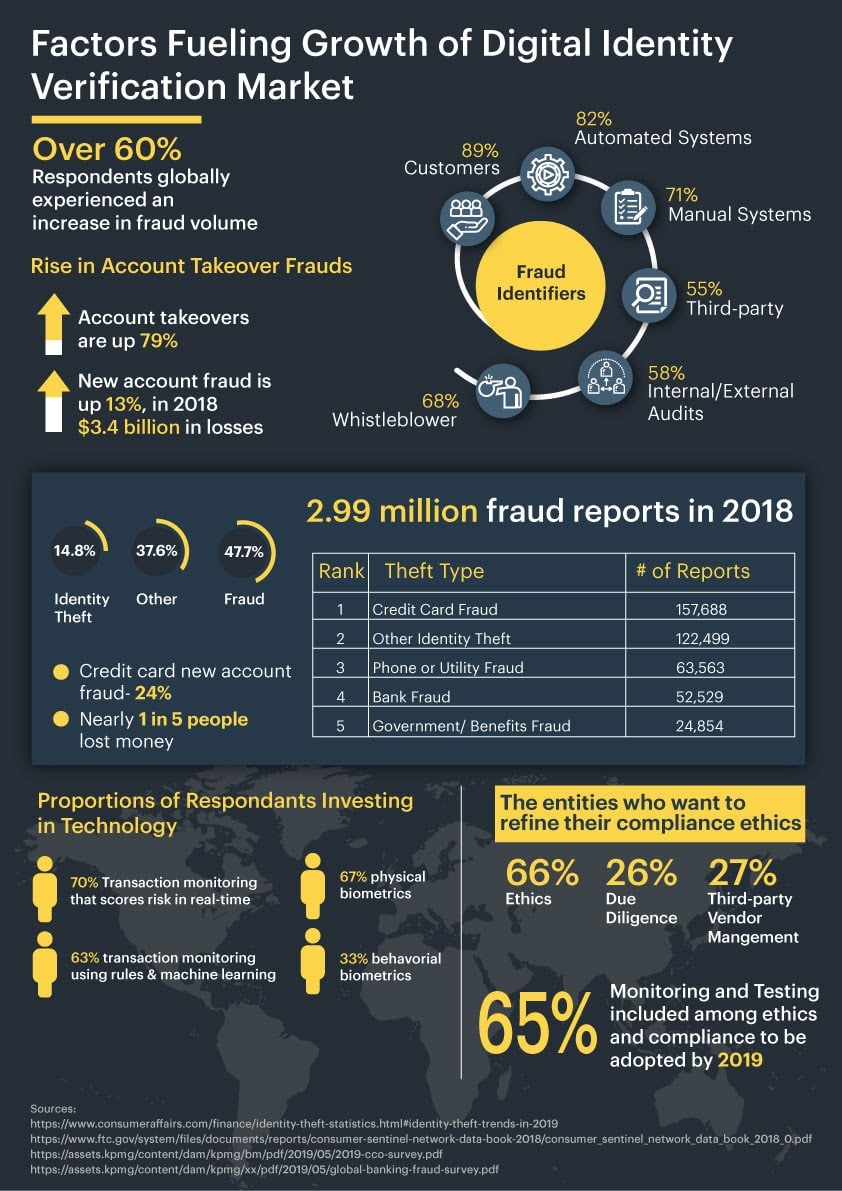
In 2018, a report by the Federal Trade Commission presented 1.4 million fraud reports. The loss due to these fraud totals to be $1.48 billion. Most common frauds, according to FTC’s, Consumer Sentinel Network Data Book, are debt collection, imposter scams and identity theft. High-risk customers target online platforms and find out loopholes that can help them commit these frauds.
Who is at risk of Identity theft fraud?
Most of the online users who neither take security alerts seriously nor report irregular online activities/warning signs regularly are prone to the incidences of identity theft. Children and old people are most likely to be attacked by identity theft. Their identities are helpful for criminals as they have not previously been used in any criminal record and a clean state for fraudulent activities can be gained. Similarly, old people’s identities are targeted through the internet or email phishing scams. Their identities are considered trusted because of their age and help fraudsters easily commit.
Credit Card Frauds
Credit card frauds are prevailing in the category of identity theft frauds. 167,000+ online users reported credit card accounts that are opened with their personal information. Cybercriminals earn millions every month by hijacking financial information of customers in the form of the credit card information. In 2018, more than 57,600 websites lost their confidential data from payment forms. New accounts are exposed to credit card frauds more.
Account Takeover Frauds
Account takeover frauds rose up to 79% in 2018 as compared to the previous year, 2017. Fraudsters use innovative technologies to hijack the accounts of online users. Using malicious scripts they use credentials stuffing techniques in which an automated script uses combinations of usernames and passwords to take out the right credentials user has saved an account with. The account takeover fraud is followed by many other frauds, for instance, stolen identity information is used in various fraudulent activities among which money laundering and terrorist financing are highlighted.
How Automated Digital Identity Verification Helps?
Unauthorized access, root to various online frauds. Identity verification solution helps cut these roots by identifying each identity access to your business platform. It seems a long process of verifying identity, but if it takes just 30 seconds then?
A digital identity verification solution is robust that identifies the individuals in real-time without compromising user experience. It helps authenticate. Using document verification, identity is verified by capturing the details from documents using OCR technology. Similarly, biometric authentication is done that verifies identity in seconds using facial recognition technology. Small as well as large businesses are integrating these technologies to make their platforms secure from any fraudulent access.
Due Diligence Compliance
Identity verification is more than an approach to avoid online fraud, it is a regulatory requirement in several countries to ensure customer’s data protection and privacy. GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) are regulations for customer data privacy to prevent it from getting into bad hands. Moreover, the growth of the digital identity verification market is driven by Know Your Customer (KYC) Anti-money Laundering (AML) and Customer Due diligence (CDD) requirements.
Digital identity and document verification consist of these four steps:
- Asking the user, “are you a real person?”
- Verifying authenticity of documents
- To ensure that you can continue business with the individual
- Enhanced due diligence to verify customer background
Among these, in the last step, identity is screened against global watchlists and PEPs records to make sure that your onboarding customers are not part of any criminal activity. Customer screening helps mitigate the risk of onboarding an entity that could be high-risk for the business.

 Explore Now
Explore Now













