5 Effective Ways Shufti Combats First-party Fraud

After analysing fraud incidents of the previous year and the current one, we observed an interesting trend. The majority of frauds detected fell in the category of first-party frauds. Crooks are using sophisticated techniques to exploit lenders, banks, and other financial institutions. From social engineering attacks to fake user identities, fraudulent activities are showing no signs of slowing down.
Fortunately, machine learning and AI-enabled technologies play a major role in assessing and detecting risks, leading to an enhanced fraud prevention approach.
What is First-Party Fraud?
First-party frauds occur when someone uses either their own identity or a fabricated identity to avail goods or products without the intent to pay back or commit fraud through impersonation and misrepresentation. Common examples of first-party fraud include bust-outs, money mules, and synthetic identity thefts.
Segmenting First-Party Fraud
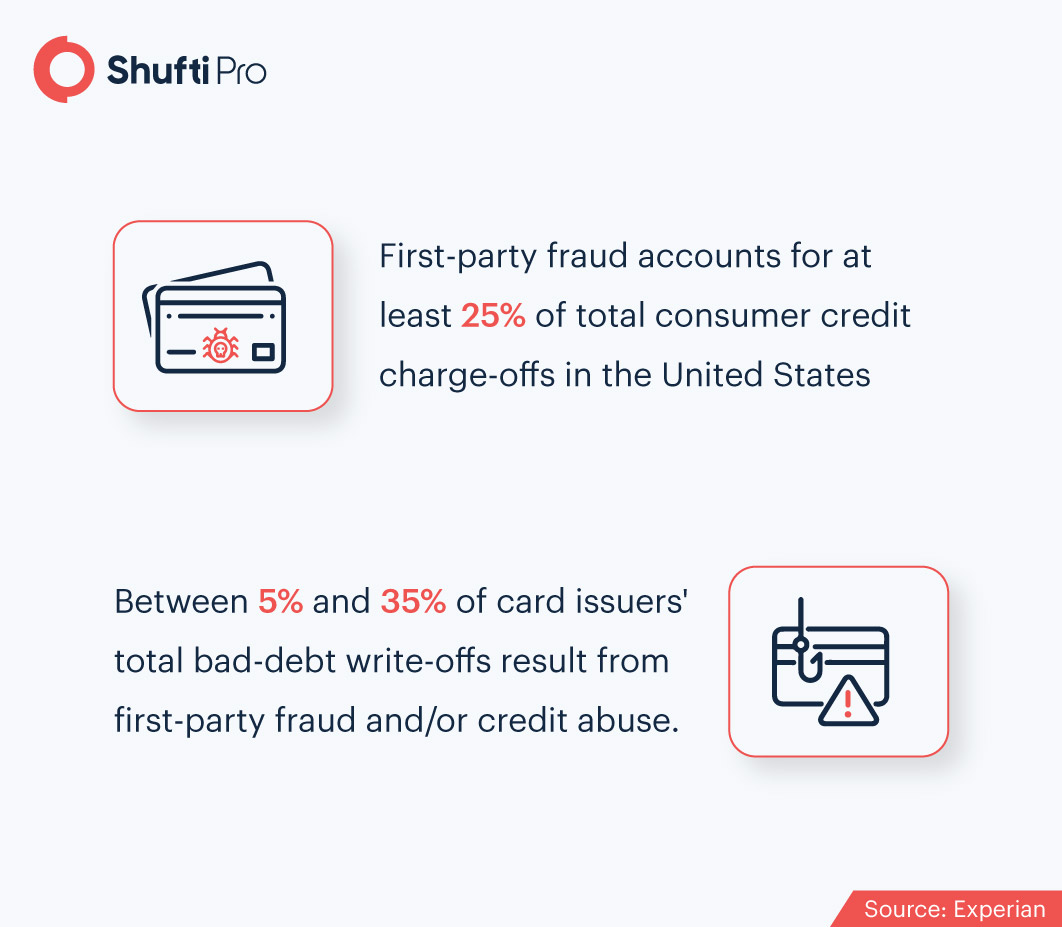
Today, the majority of frauds (29% of total fraud cases) occur through impersonation and false representation. By faking their true identity or misrepresenting their intentions, criminals are able to steal sensitive information, resources and money. Here are the top five techniques used by perpetrators to commit first-party frauds.
1- Bust Out
Bust out fraud, also known as sleeper fraud, is the most common type of first-party fraud. It occurs when an individual uses a credit card under their own name or through a fake identity, to perform transactions. Initially, the criminal maintains a good credit history, only to abandon the account after bouncing the final payment.
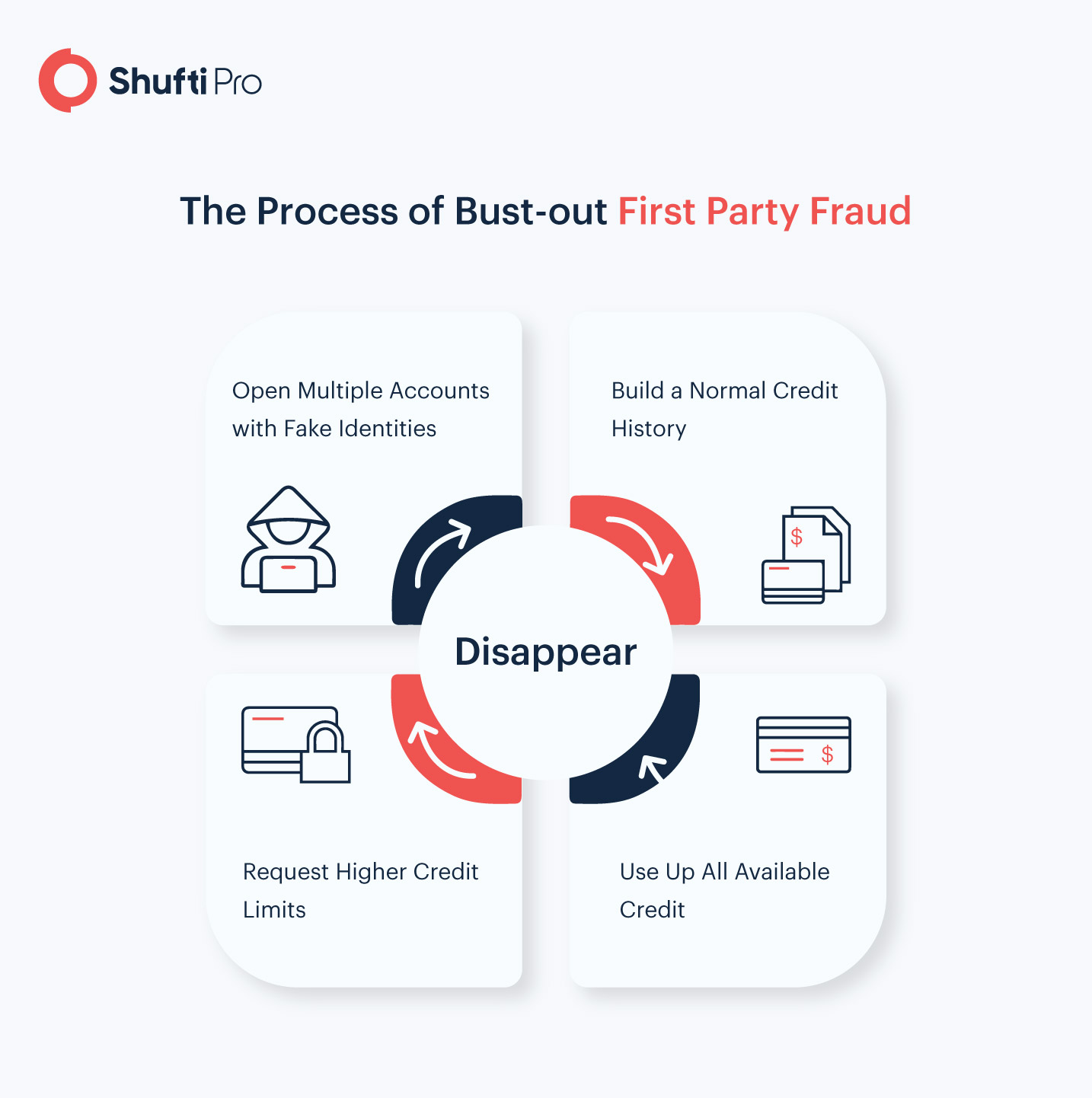
When it comes to bust out frauds, bank cards are criminal’s favourite medium. However, fraudsters also use retail cards, and other secured or unsecured loans for the same purpose. According to expert estimates, 1000 to 2000 cases of bust out frauds are detected by banks each year.
The solution? Ongoing KYC. For a bust out fraud to be successful, it is necessary for the criminal to fool a bank’s KYC process. This is usually accomplished by providing false information through fraudulent documents. Shufti’s KYC process involves a careful assessment of all verification attempts by not just artificial intelligence algorithms, but also human experts. This hybrid approach ensures that no fake document, not even the slightest pixel modification, goes undetected. As a result, the fraud attempt is detected during the initial stage of onboarding, leaving no room for bust out frauds to proceed.
2- Synthetic Identity Fraud
Synthetic identity fraud is an advanced version of identity theft. In this type of fraud, fraudsters steal parts of another person’s identity and combine it with fake information to forge a new identity. Synthetic identity fraud has become the fastest-growing crime in the US today, accounting for 20% of all credit losses. What makes this threat highly alarming is that 85-95% of this fraud is left undetected due to the advanced modification methods used by criminals.
Is there a way businesses can safeguard themselves against such imposters? Fortunately yes. Shufti’s Video-based KYC service has the ability to weed out synthetic identity thieves with an accuracy rate of 98.67%. The process involves digital face-to-face interaction between a KYC expert and the end-user, automated document authentication, as well as biometric facial verification. With this unique combination in place, a rapid and foolproof security mechanism is ensured against synthetic identities and other spoof attacks.
Download Report: Video Interview KYC – Efficient & Secure Customer Onboarding
3- Chargeback Fraud
Chargeback fraud refers to a situation when a cardholder disputes a transaction to get their money back while retaining the good or service purchased in the first place. This fraud is referred to as a first-party fraud transaction, since the cardholder tries to make illegal monetary gains through the dispute. Industries that are the primary targets of chargeback frauds include e-commerce, retail stores, and financial institutions.
Biometric consent verification provides the best solution for combating ever-increasing credit card frauds such as false chargeback. Under this process, customers are authenticated simply through a live selfie and unique printed or hand-written note. With consent note verification, imposters filing for false chargebacks are caught within 15-30 seconds, as the consent video serves as the proof of their purchase.
Suggested Read: Why a Business would need Biometric Consent Verification?
4- Money Mules
Where drug mules transfer drugs from one point to another on behalf of others, money mules do the same with money. This is typically executed either through the money mule’s own bank account or by opening multiple other accounts to transfer money to a third party – usually a criminal money laundering ring. Between 2015 and 2019, fraud reports tripled from USD 1.1 billion to USD 3.5 billion, much of which was enabled by money mules. These numbers continue to increase well into 2021, making the detection of these culprits highly crucial for businesses.
A simple process that businesses can use to detect money mules and their fraudulent transactions is known as KYT. Abbreviated for Know Your Transactions, KYT procedures are performed to verify and monitor the customer activities on an ongoing basis. By keeping a tab of all the transactions being made, suspicious cash, payment card, and cross-border transfers can be detected within seconds.
Another method commonly used by banks for customer risk profiling is Anti-money Laundering (AML) screening, which involves transaction monitoring, Politically Exposed Person (PEP) and sanction screening, and ongoing risk assessment.
Read More About Money Mules: Jobs in the Frame For Money Laundering
5- Shell Companies
When it comes to forming B2B relationships, companies need to keep an eye out for shell companies. These companies exist only on paper, offering the fraudulent owners the perfect opportunity to launder money or evade taxes. In case business dealings are made with shell companies, hefty fines and penalties can be charged by global regulatory authorities on top of a damaged brand image.
However, the authenticity of any business entity can be verified through Know Your Business (KYB) procedures. Shufti’s KYB service provides an automated and comprehensive method for mitigating the risk of fraud. It involves the detection of shell companies through the verification of the UBO’s, business documents, stakeholders, corporation licences, and more.
Suggested Read: Know Your Business – What Does it Mean & How can it Protect Your Company?
Summing It Up
In this era of technological advancements, artificially intelligent solutions are available in abundance. However, the key to winning the battle against first-party fraud is to choose the technologies that are difficult for fraudsters to fool. Shufti’s fraud prevention solutions provide companies with a cost-effective means of performing risk assessments, ongoing screenings, and AI-based identity verification – all of which are necessary to mitigate the threat of fraud. Thus, if you are a company looking to prevent first-party fraud, Shufti’s automated solutions are the answer you are looking for.
Contact our experts to learn more about combating first-party fraud!

 Explore Now
Explore Now













