7 Ways to Protect Your Children from Identity Theft

Living in the digital world, the word “Identity theft” makes us more than a little nervous. Knowing that someone out there is using your identity for criminal activities sound so scary. It is even more surprising for parents to know that stealing their children’s identities is easier. What makes it more frightening is the nature of the theft that it may take too long to discover the crime.
No one can provide better protection to children other than parents. Parents are ultimately the best protection against child identity thieves. However, the lawmakers are now actively taking part as well in raising awareness about this matter. In fact, there are some movements for the protection of children’s data – for instance, National Child Identity Theft Awareness Day.
Moreover, the government is introducing Child protection laws – The Digital Economy Act 2017 – to protect the identities of children in the digital world. These laws enforce the digital platforms to incorporate age verification checks to their digital platforms to keep minors away from the dark web and age-restricted mature content.
National Child Identity Theft Awareness Day
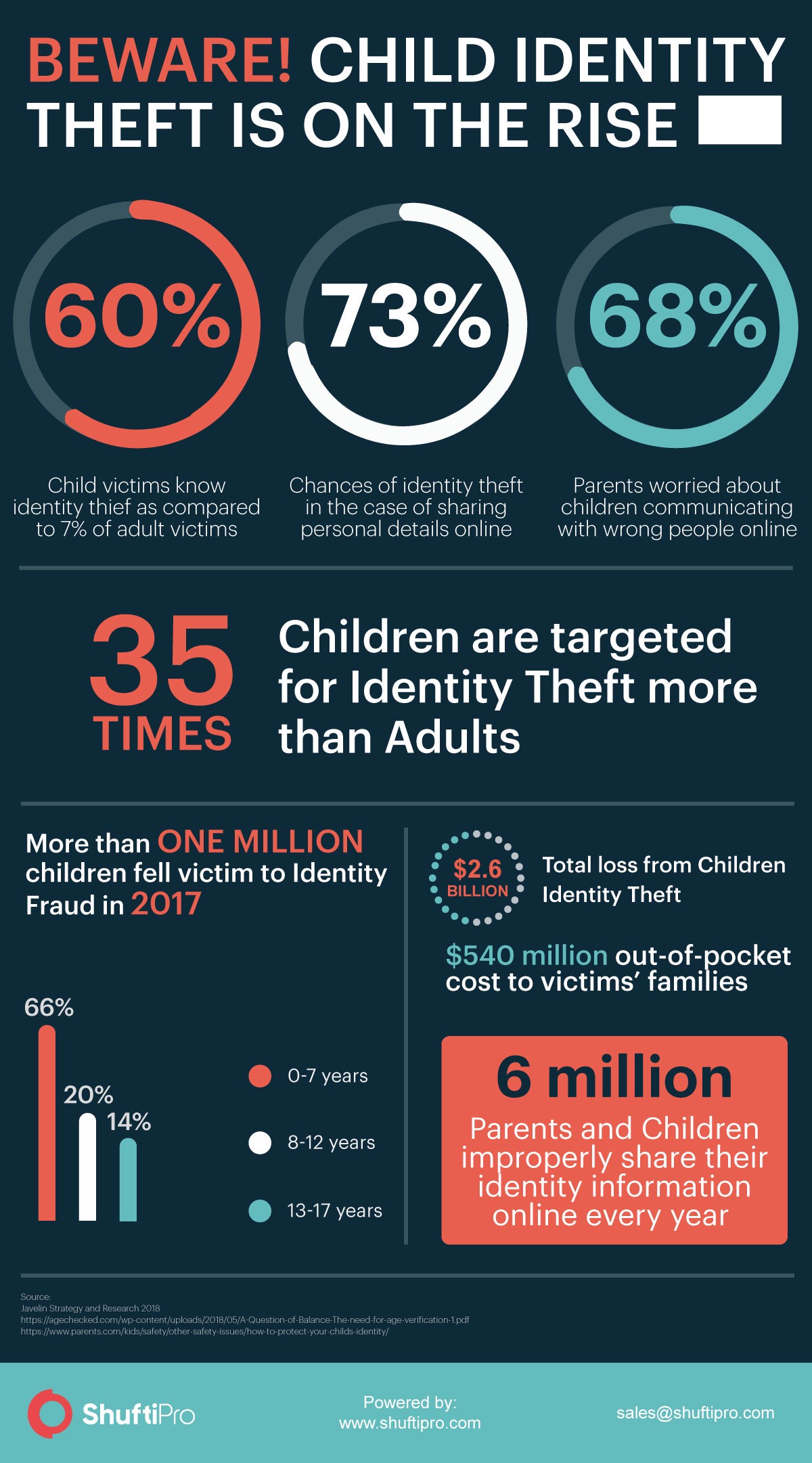
Identity theft is becoming a worldwide issue. Every year millions of people fell victim to this crime and lose billions due to frauds that occurred using stolen identities. According to The Harris Poll, around 15 million Americans fell victim to identity theft in 2017. Not just the adults but the children are equally or more on the target list of identity thieves. According to Javelin’s Report, more than a million children were the victims of identity theft in 2017 which resulted in a loss of $2.6 billion.
Taking into account the alarming situation of children identity theft, the world’s leading global information services company, Experian, started the movement “National Child Identity Theft Awareness Day” – held on September 1 every year. The aim of this movement is to educate the parents about protecting their children’s sensitive information. Most parents are unaware of the reasons and vulnerabilities that lead to identity theft. As per a study, the children who are bullied online are nine times more likely to fall victim to identity theft.
Identity thieves primarily target children because of their clean histories and the criminals can use their information for a longer period of time without getting caught. The reason is parents are oblivious of the fact that their child’s identity is under threat. Hence they don’t necessarily check their children’s credit report.
The Cultivating Threat
The nature of the crime “Child Identity theft” to stay undetected for a longer period of time makes it hair-raising. Every year criminals succeed in exploiting millions of children’s identities. The explosion of the internet and smart devices is not helping either, instead, it has fueled up identity theft to an alarming rate.
Tips for Parents to protect their Children Identity
Parents are often under the wrong impression that their child’s identity will never be stolen and that’s what they do wrong. Even if you are sure that your children are safe, a few preventive measures won’t hurt, right? There are some common red flags parents don’t pay attention to and hence their children get stuck with privacy problems.
Here are some simple tips for parents to protect their precious bundles from falling victim to this rising crime.
Look out for Red Flags
The best way to deal with the problem is to know its root causes first. Once you are aware of the factors that can lead to some problems then you can easily combat that. In order to protect your children from identity theft, you must look out for warning signs. Just imagine you come across a pre-approved credit card offer in your child’s name. It may sound some computer glitch to you. But what if it’s not?
This can be a warning sign that someone is using your child’s identity. If you ignore this thinking of it some computer mistakes then it may lead you to a major problem.
Monitor your child’s Social Media
Living in the world of mobile phones and tablets, children using the internet is not something new. Every child now has a presence on the internet whether it’s about watching cartoons on youtube, playing games or using social media. You have no idea who the fellow gamers and anonymous friends are. They can even be identity thieves or pedophiles.
Allowing your child to explore the technology isn’t bad but leaving them on their own may have a negative impact. If you are letting your children participate online then make sure to monitor their activities. The passwords of the accounts must always be available to parents so that they can check regularly with whom their children are interacting. Children may find it their privacy breach or may just hate the idea of giving their passwords. But it’s essential for their protection.
Protect your Child’s Social Security Number
The social security number is the key to a child’s identity and is the first thing that identity thieves target. They can use it to unlock many hidden doors for their benefit. The stolen SSN can be used for multiple purposes – the creation of synthetic identities being the significant one. These identities can be used to open a bank account, issue a credit card, get a bank loan or a car and health insurance, etc. By the time such frauds are detected, it has already caused enough damage.
To avoid these situations, as parents what you can do is obtain SSN for your children first and then keep it safe. Parents need to be vigilant in sharing the children’s SSNs. there are many organizations that ask for children’s social security numbers even though they don’t need it. In such cases, parents should inquire about which purpose are they going to use it.
Open Joint Bank Account
Parents are often seen opening bank accounts on their children’s names to deposit saving checks and bonds. But these savings accounts can pave the way to identity theft. Since once your child’s account has an account, it means that there will definitely be bank statements, emails and letters from the bank. The fraudsters can access that information by some means and use it to get their hands on your child’s cash. Moreover, criminals may use that account to do business or for illegal transactions like money laundering, terrorist funding, etc.
If you are opening an account on the child’s name then make sure to link it to your account as well, or open a joint account. It will help you keep an eye on the transactions and monitor the payments. Whenever there is some suspicious activity you can be notified instantly. Sometimes, clever crooks use the child’s account to take loans from banks which they have no intention of returning. In those circumstances, the child’s name will be reported to the agencies which may lead to a severe mess, difficult to clean up. By having a joint account, your permission will also be required in order to process any payment or loan.
Dispose of Data Carefully
The discarded data is worth a million in the dark web since the criminals can use it for multiple illegal reasons. You need to be very cautious while throwing away the garbaged documents. Always dispose of the documents, or anything addressed to your children before throwing them out. The things that are wastage for you can be valuable for crooks.
Safeguard your smart devices
The advancement in technology has opened new doors for cybercriminals to exploit the user devices and obtain the personal data stored in it. It is your duty as parents to secure your smart devices in every possible way. Never store your sensitive data on laptops or mobiles. Always keep it stored in external hard drives or flash USBs.
Moreover, set strong passwords for your devices and install security apps and antivirus software to keep them secure.
Find and Freeze Credit Report
We often think that children don’t have any credit histories so why would identity go after them? That’s where we are wrong. The clear status of the child’s credit history intrigues the thieves since using their identity they can apply for credit cards, open utility accounts, take out loans, commit tax frauds and many other forms of digital fraud. Timely check the credit history of your children. If no credit report exists then it’s best otherwise immediately get the report and proclaim it to the respective authorities. It may be a sign of possible identity theft.

 Explore Now
Explore Now













