Age Verification for Social Media – Protecting the Younger Victims of Online Scams

With a significant majority of students diverting from their usual school routines due to the COVID-19 outbreak in the past year, more time was spent using the internet than revising courses. This was clearly a negative situation as it resulted in the slowing down of childrens’ learning process, but that’s not all – the increased social media usage by children makes them vulnerable to scams involving personal details and financial data.
Over half of the world’s population is using social media and some of the prominent platforms like Facebook, Instagram, and TikTok are of particular interest for the younger generation. The naivety of teenagers opens up various doors for scammers to take advantage of them through seemingly interesting advertisements and fake surveys that appear to be from legitimate sources. Similarly, fraudsters exploit the immaturity of children in online shopping platforms to gain access to sensitive payment details.
How does Online Age Verification Work?
Online Age Verification allows businesses to verify the age of their customers to prevent minors from identity fraud. End-users are required to submit their personally identifiable information through an online form. Additionally, a photo of the users’ identity document is required. Extracting details using OCR technology and matching them with the provided information allows accurate age verification.
Digital services, products, and online shopping platforms offering a vast variety of items are all one-tap away in today’s tech-driven era. This ease of access means that individuals of all ages are interacting, performing uploads/downloads, and transacting through online platforms.
Identity Theft on Social Media
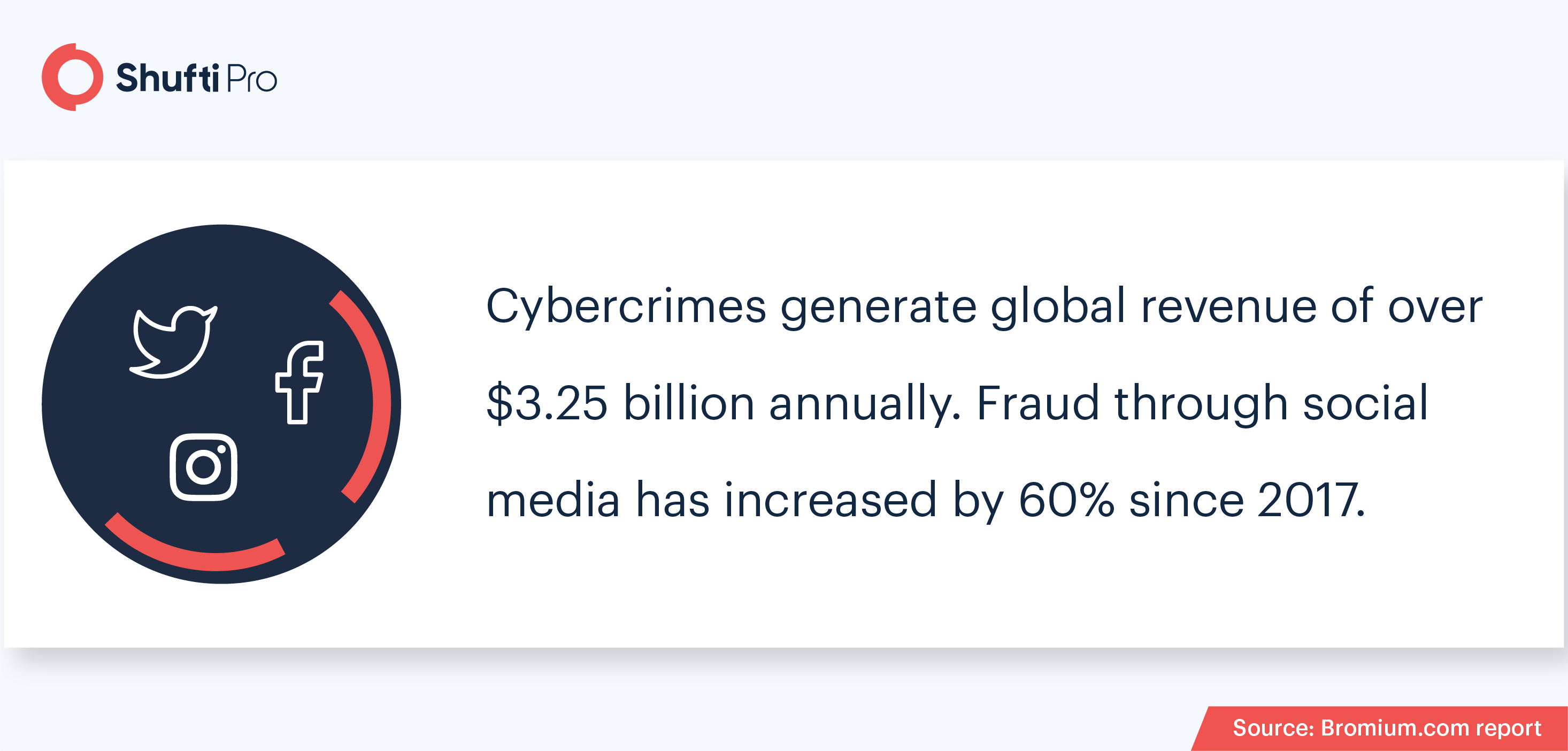
Faking identities is a relatively simpler task while using social media platforms as no physical presence is required. According to The New York Times, 5% of the total Facebook accounts were fake as of December 2020 – that makes over 90 million accounts. Most of the social media scams are being operated through these fake accounts to represent a made-up business or organization.
Fake details of business pages are used to fool individuals, particularly the younger ones, into believing that they are communicating with legitimate companies. Not only Facebook, but also Twitter, LinkedIn, and the commonly used dating sites are prone to identity theft and other numerous scams. Primarily, social media platforms used for businesses lack identity verification checks, but with the rising number of scams targeting minors, age verification is an essential measure to secure these apps.
Influencer Scams
The common perception when the word influencer is mentioned is of successful accounts that have millions of followers. Looking at the bigger picture, however, new types of influencer scams have emerged. Instead of promoting businesses or services, influencer scams are seen to promote fraud. Once influencer accounts on social media surpass a certain level of followers, they get incredible reach from users of all age groups.
That being said, the root cause of these influencer scams is the lack of identity verification for business accounts on social media platforms. Considering this scenario, identity verification measures need to be implemented in social media platforms so that the creators of these fake influencer accounts are filtered out. This can help in restricting fraudsters from creating social media accounts, hence eliminating these scams altogether.

Financial Scams
Although financial scams are generally targeted at a wider range of age groups, teenagers are more prone to getting affected by them. Apart from credit card scams, several types of financial scams are being operated through social media platforms, where the younger individuals are made to believe that they will earn a certain amount in a short time. Fake businesses offer interesting investment opportunities through emails, texts, and advertisements.
A pyramid scheme uses a hierarchical network marketing system to pull in money, where the base of the pyramid is created by investments from new victims. The money is used to provide returns to earlier investors in the upper portion of the pyramid. Ponzi schemes are the most common type of pyramid scams that offer big returns for investments and steal money from individuals on social media. Young individuals in their late teens often become victims of these schemes in the hope of starting an independent life. These schemes are eventually revealed when there are no new investors and the scammers can’t pay back.
Offers on Expensive Items
Social media ads for prominent market brands of electronics and other running items are commonplace, and it’s usually obvious that they are fake. The prices at which the particular expensive items are advertised are hardly a fraction of their original price, making it clear that the ad is from an unreliable source. However, minors looking for low prices often act hastily and provide payment details to the scammers posting too good to be true ads.
Brands like Nike and Apple are hot favourites of children who anxiously wait for new products. Not just children, but fraudsters also keep an eye out for the new features in limited edition products to post their own fake offers on social media to get inside the heads of teens. These fraudsters know well enough that kids always wish to have the latest items in the market, and capitalize on the unsupervised usage of elders’ financial information by children. Without age verification solutions, teenagers pay for services without considering the actual prices, for which their parents have to ultimately pay.
Scholarships and Job Offers
One of the common concerns of young students is the money required for their higher education. Targeting this weak point of teenagers, scammers design fake scholarship schemes and job opportunities in order to rake in bank account details. What appears to be the fee for a particular job application is actually a scam, which results in monetary losses. Age verification solutions for social media platforms can provide a solution to put an end to these scams and secure the digital landscape.
Student loans also bring about opportunities for fraudsters to carry out illegal activities and make money. Older teens are targeted in these kinds of frauds where a fee is charged for potential elimination of debts. Imposters take the desired amount and then disappear leaving no traces. Parents also face a complicated situation when it comes to education and agree to pay fees when required, but the social media scams are seen to make the most of teenagers on platforms like facebook, where their activities are not being monitored.
Unfortunately, teenagers cannot be taught to handle fraudulent information as it comes in various forms and uses different mediums. The common solution to these scams is incorporating age verification solutions in social media platforms, and identity verification for businesses selling products or services through social media platforms.
Concluding Thoughts
The need for keeping sensitive information like addresses, passwords, social security numbers, and bank credentials cannot be stressed enough. However, Shufti offers digital solutions that are easy to incorporate. Social media platforms can simply integrate the APIs to abide by the age verification laws.
Shufti’s age verification service allows social media platforms to verify the age of end-users during account opening. Henceforth, minors can be prevented from accessing age-exclusive products/services.
For further information regarding age verification solution, get in touch with our experts.