China’s New Data Security and Personal Information Protection Laws [2022 Update]

For the purpose of identification, interdiction, and prevention, many governments, regulators, and businesses are collaborating to draw a distinction between fraud and financial crime. However, the boundaries are blurring, since the cyber threats are on the continuous rise, which is uncovering the extent to which online criminal activities have become interrelated and more complex. Due to this, a large number of well-established businesses are under the stress of cybercrimes, particularly, data breaches.
Like other countries across the world, China is also experiencing digitization. However, with the advent of digital file transfer and cloud storage by industries, data breaches, and identity theft crimes are occurring at a fairly high rate. Thus, there was a total of $6 trillion loss in cybercrimes globally in 2021. Thus, the government of China has come up with two new laws associated with data security and personal information protection which was legislated in the fall of 2021, aimed to provide a comprehensive approach to enhance data security, cybersecurity, and individual privacy.
Insights into Cyber Security and Data Protection laws in China
In recent years, China’s data protection and customer privacy regulation regime has been enhanced periodically to eliminate the risk of data breaches and identity theft. The Personal Information Protection Law (PIPL) became part of the ever-evolving regime on 1 November 2021 and is considered the country’s first comprehensive data protection law. The rule regulates the use of Personally Identifiable Information (PII) by individuals as well as businesses within the China boundaries. In addition to this, two other laws, regarding cybersecurity and data protection compliance, Cybersecurity Law (CSL) and Data Security Law (DSL) respectively.
Other than these laws, The Civil Code of the People’s Republic of China (The Civil Code) was also legislated in the first half of 2021 that provided the true rights of personal information protection and privacy. It was also made mandatory for every business to streamline its operation with these laws. However, under the Civil Code, a completely new era of data protection and privacy started. Meanwhile, the same patterns of amendments and emergence of new cybersecurity guidelines are also expected in 2022. Moreover, there are also specific standards and guidelines for industries such as finance, healthcare, and so on.
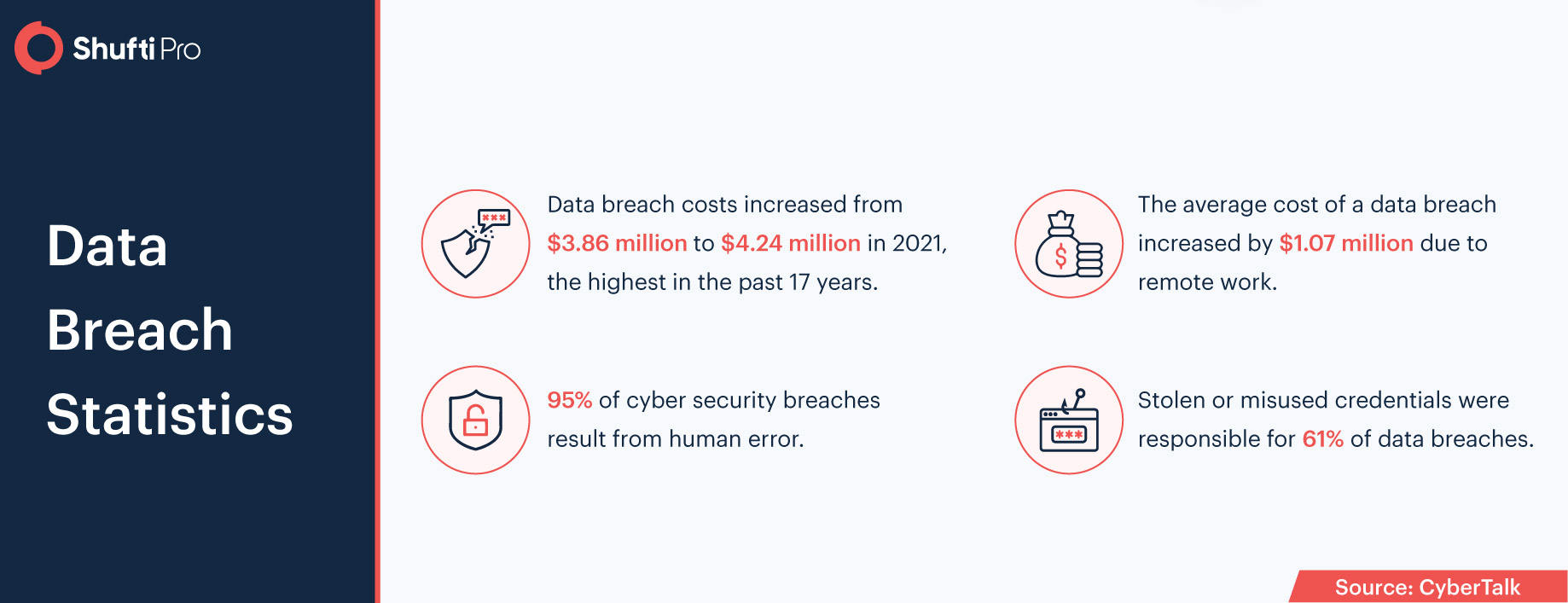
New China’s Data Security and Personal Information Laws
In accordance with the Data Security Law (DSL), a rigid framework is developed that classifies PII gathered and stored in China, based on its potential impact on the country’s national security. It also governs the storage and transfer depending on the classification level. However, this law is legislated as a response to the US Clarifying Lawful Overseas Use of Data Act (CLOUD Act).
Categories of Data
“Core data” under this law is comprehensively defined as any kind of data that can impact Chinese national and economic security, public welfare, or interest requires a maximum degree of guidelines and protection. “Important data” is the next highly sensitive level of data, but its scope is left undefined, as the national, regional, and designated authorities are expected to issue their own catalogs regarding important data.
Thus, data security laws imply that all the businesses operating in China need to collect and process and store customer data.
Localization and Transfer of Data
The DSL widens and clarifies data localization and transfer standards for “core” and “important” data yet for certain types of businesses that handle sensitive data. For instance, critical information infrastructure operators (CIIOs), that oversee the data dealing with infrastructure, informational networks, and natural resources must assure that data was generated and stored within China. Moreover, a rigid set of security self-assessment checks needs to be conducted before sending data out of the country. In addition to this, the DSL also directs some additional standards and regulations that must be developed for non-CIIOs.
Downstream Data Handlers
The DSL also expands the scope of regulation, like initial data collectors, downstream “intermediary service” that uses sensitive data for commercial purposes also need to be governed strictly. Thus, these downstream data handlers are obliged to verify the true identities of the parties before a data transaction is made, along with managing the transaction records. Therefore, in case data handlers fail to comply with DSL may face a regulatory fine of RMB 2 million, cancellation of business licenses, and an immediate shutdown of operations.
Data Security
The DSL mandates the businesses and financial institutions that are operating in China to establish and enhance the data security systems. On another hand, in case the shortcomings in the system are detected, instant remedial measures need to be taken along with notifying the customers, as well as regulatory bodies regarding the data breaches if it happens. However, if the companies handing information of at least “important data” are obliged to onboard security officers that would be responsible for securing data and submitting the risk assessment reports to the PRC authorities.
An institution that fails to meet the regulatory obligation and to secure customer data may face a hefty fine up to RMB 500,000, and if companies fail to improve their systems that resulted in data leaks may face fines up to RMB 2 million.
The Personal Information Protection Law
The personal information protection law (PIPL) is considered China’s first detailed law that governs PII protection and is developed after the EU has come up with General Data Protection Regulation.
“Personal Information” is broadly defined to cover “any information related to identified or identifiable natural persons stored in electronic or any other format.” So long as the information is “related to identified or identifiable natural persons,” even if there is not sufficient data for identification, the PIPL still applies.
The law is applicable to all types of data activities, for instance, storage, gathering, deletion, processing, etc.) involving the PII subjects in China along with the activities that are happening outside the country, yet aimed to provide services to the Chinese public. Non-compliant with the PIPL regulations could face a fine of RMB 50 million, 5% of the business’s yearly revenue, and all illegal gains would be seized.
Consent Requirements
Before gathering or handling PII, a data handle needs to get clear consent from the person whose information is to be obtained. Data handles that are collecting sensitive personal information – a data category that includes data subject, biometrics, religious beliefs, finances, location, and children’s details along with the purpose of data collection, aim to fulfill the PIPL requirements.
Data Localization and Data Deletion Requirements
In case, if the volume of PII collected or handled by the respective handler exceeds the certain described thresholds, data localization requirements could be triggered, and the data handle will additionally be required to onboard an information protection officer to oversee the whole handling and protection procedure. Other than this, they are also required to delete the collected information, once the purpose is fulfilled. When the data no longer serves its purpose, the retention period automatically expires. Thus, data must be deleted, before it gets into the wrong hands.
Restrictions on Transfer of Personal Information to Third Parties and Overseas
Before transferring the personal information to the third parties, either within China or across the border, the data subject’s detailed consent must be obtained and the recipient should ensure that the PII is used as per the terms and conditions of the consent.
For international transfers, the data handler needs to be utmost assured that the recipient has a rigid data protection system in places where their operations are aligned with the PIPL regulations. However, depending upon the classification of the data additional requirements may also apply.
General Compliance Requirements
To fulfill PIPL requirements, companies need to conduct regular self-assessments and audits in order to determine the information security risk and take necessary steps to enhance control systems. However, if the company qualifies as a “major internet service platform” more strict rules may be applied. In addition to this, companies that are using algorithms and automated decision-making functions to analyze personal information must abide by the transparency principle as per PIPL laws.
How Shufti Can Help
Shufti’s state-of-the-art identity verification services are embedded with all the features that can help data handlers to stay put with the regulatory obligations while ensuring that the customer’s data remain un-breachable. Businesses opting for robust identity verification solutions can overcome sanctions and fines for being non-compliant.
Following are the key benefits of Shufti’s ID verification services;
- Determines the real identity of the customers in less than a second
- Generate results with 98.76% accuracy
- Screenings the customers against 1700+ global watch lists
- Helps to stay put with the regulatory obligations and secures businesses from sanctions
Want to learn more about ID verification services for businesses?

 Explore Now
Explore Now













