Multi-factor Authentication is being defeated’ warns FBI

For years, online businesses and organizations have been adopting various strategies and defense mechanisms to protect themselves from every kind of cyberattack. Cybercriminals are actively embracing technology to conduct sophisticated attacks online. This increasing trend of data breaches and digital frauds is a striking example of growing cyberattacks. Defending against these attacks has become a new normal for businesses worldwide.
One of the widely used methods to prevent these frauds is multi-factor authentication (2-Factor being the most common one). Although businesses and organizations are proactively using multi-factor authentication to protect their systems and data from perpetual business email compromise (BEC) attacks, the new warning from the FBI has surprised them unanimously.
According to the FBI, cyberattacks are circumventing multi-factor authentication through various social engineering tactics and technical attacks. In multi-factor authentication, the use of a secondary token or one-time generated code verifies and authenticates the identity of the user. But with the FBI’s new warning, businesses are quite bewildered.
FBI Warning: The Surprise Factor?
The reason for this perplexity is that businesses have yet to come across such attacks on MFA. So far, such attacks have been rare to witness.
Microsoft azure claims that multi-factor authentication blocks an unbelievable 99.9% of enterprise account hacks. Adopting this method is the least the organizations can do to protect their accounts as the rate of compromise of accounts is less than 0.1% for the companies that are using any type of MFA.
Even with the least compromise rate, the use of MFA is uncommon with less than 10% of the users per month (for enterprise accounts) – claims Microsoft. This statistic alone contradicts the FBI’s threat of MFA compromise, and businesses were not expecting it. However, the FBI states that the use of one-time codes and secondary tokens is not enough to back up the user and his credentials, nor is it sufficient to protect his identity.
How MFA is vulnerable to cyberattacks
Despite the endless struggle of businesses to protect the user’s information, by making account access harder and complex through two-factor and multi-factor authentication, it can still be vulnerable to breach. There is a high-risk that cybercriminals can attack and trick users into disclosing their credentials and authentication codes through social engineering. Or, they can create an account for themselves through the use of technical interception.
Phishing
Phishing attacks are a great example of social engineering. They can be used to lure victims into providing their credentials through a fake login page. Due to readily available technology and APIs, it is not difficult for criminals to create a fake login page. Attackers make use of different social engineering tricks (for example emails, fake job alerts, etc.) through which they tempt the users to click the link which is a clone of the original login page.
When the victims enter their credentials, the hackers fetch that information and pass it to the real login page, henceforth triggering the multi-factor authentication procedure. The victim is shown fake prompt requiring the texted or mailed code. Just like before, the hackers catch the code and complete the authentication process.
This is not as easy as it seems. Hackers need to be fast enough due to the limited time-factor associated with the code. But once the process is successful, there’s nothing that can stop them from carrying out their activities.
Password Reset
Many times, the authentication process can be bypassed through the “Forgot Password” procedure, if a hacker is in possession of “something you have” item (for example, email).
If the criminal/hacker has gained access to the victim’s email account where the verification link or code is sent, the attacker can easily use the “Reset Password” link and change the passwords to something else by following the instructions. Moreover, once he has access to the account, he can even change the recovery email and phone number, giving him complete access.
Third-Party Logins
The explosion of online platforms has introduced a new authentication process for enhanced user-experience – through third-party logins.
In this process, the user is offered an option to log in using third-party accounts and bypass the 2-factor authentication procedure. An example of such a case is “Login with your Facebook Account” or “Login with your Gmail Account”. In this case, an attacker can easily take over the accounts once they have access to your Gmail or Facebook credentials (through phishing and forget password procedures).
Brute Force Attacks
With the advancement of technology and automated tools, hackers have the opportunity to obtain user passwords and verification codes through brute force attacks. Through brute force, the attackers can gain limited-characters tokens. The tokens or verification codes are quite useless if the attackers get enough time to apply brute force and obtain the token.
Advanced Tools and Techniques
On the one hand, technology has helped organizations in securing their digital presence, while on the other, it has also contributed to the innovation of advanced hacking tools.
In its investigation, the FBI has highlighted different examples of tools and techniques that are being used to defeat multi-factor authentication. It includes web hacks, cyberattack tools like NecroBrowser and Muraen, not to forget straightforward SIM swapping. The main issue with MFA is that organizations find it an ultimate solution for the security of the institution.
Solutions to Cyberattacks
While massive data breaches and identity theft are on the rise, multi-factor authentication is becoming the standard procedure for most of the organizations to secure themselves from attackers.
No doubt, it is quite a secure method but hackers are now finding ways to get around MFA. While the risks are rare, the fact that a growing reliance on MFA can lead to growing attacks on MFA can’t be ignored.
FBI states that as per research 99% of the attacks are triggered by the person’s activities i.e. through clicking the link and falling victim to phishing scams as well as social engineering hacks. The most effective solution is to educate employees and consumers to recognize the phishing attacks so that they can try to avoid them.
Use of Biometrics
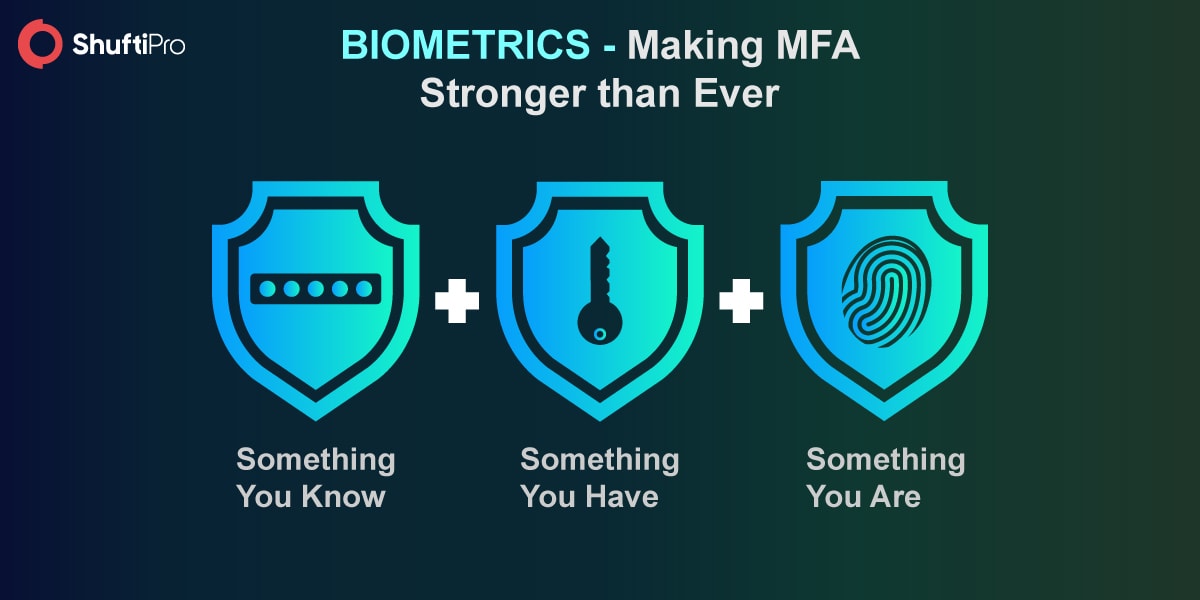
The multi-factor authentication can be secured just by adding an extra layer of security i.e. Biometrics.
The hackers can access something you know (credentials) and something you have (authentication codes) but they can’t access something you are (biometrics). Biometrics are the unique features of a person that can’t be stolen or changed. Incorporating biometric verification with 2-factor authentication can provide the most effective and secure authentication process.










