On-Premises Identity Verification – A Solution to Prevent Data Breaches

From virtual modes of communication to digitised solutions for operating efficiently, the perks of digitisation for businesses are hard to count. With the advent of technology, all the businesses are enjoying numerous advantages but so are fraudsters. Cloud storage is bringing convenience for not only organisations but criminals as well. It works like a goldmine for fraudsters to fulfill their malicious intent. These storages were designed to keep all the data secure. Unfortunately, these storages can be illegally accessed with the help of Artificial Intelligence and Machine Learning algorithms. Customer information stored during the verification process is not safe anymore on databases. Companies acquire very sensitive information during identity verification and store them in the back office for later use. But are these back offices secure nowadays?
Cyberattacks are on the rise and combating them is another big challenge for companies. Robust identity verification measures can prevent fraudsters from causing trouble from your platform, but how to secure information obtained during the process? On-premises identity verification service is one such way of preventing data breaches. Curious to know about data breaches and a credible solution for the issue? Read this blog to know more.
What are Data Breaches?
A data breach is a cybercrime that occurs when cybercriminals gain access to a company’s database and violate sensitive information. This usually happens because the security measures of the organisation are not strong enough to prevent fraudsters from penetrating the cloud storage.
After acquiring information, the information can be used for synthetic identity fraud, account takeover, and creating fake profiles on social media. Generating forged documents for traditional verification purposes is not a big deal for criminals. The IBM reports state that the average cost of every lost or stolen data is $150 and millions of records are stolen every year. The huge financial loss for any company is hard to mitigate. Hence, a better solution is needed to prevent data breaches.
What is On-Premises Identity Verification?
On-premises identity verification is an AI-powered strategy that allows companies to verify their customers without storing any confidential information on a database.
- Data privacy and security
- Caters to the complex architecture of data-sensitive businesses
- Builds customer trust
- Prevents data breaches
Some Popular Cases of Data Breaches
Every year, companies across the globe report data breaches and the lost trust of customers. The first data breach was in 2005 when DSW, a footwear warehouse, lost records of one million customers. Since then, renowned businesses have been under a data breach attack losing millions of records, customers, and money to fraudsters. Here are some of the famous brands that have suffered significant losses due to breaches.
P&N Bank
The finance industry is not safe from financial crimes and Australian bank P&N faced a data breach when it was conducting a server upgrade through a third-party host service. The reports say that 96,000 customers were informed about the breach, but the exact number of lost data is still unknown. Information breached included names, phone numbers, account details, and balance details of the customers.
Social media platforms are used everywhere nowadays and Instagram is getting popular every day. However, it experienced a data breach attack as well earlier this year. A third-party partner of the platform named Social Captain helped followers in increasing their followers. Unfortunately, the vendor exposed records of millions of users, and a bug was used to access Instagram profiles associated with the vendor without using any credentials. It is highly recommended by Instagram to never share your passwords with any third-party no matter what happens.
Marriott
The hotel giant, Marriott, has unfortunately experienced a data breach twice within the last two years. The first one was in November 2018 that impacted 500 million guests and the second one was in the first half of 2020 that impacted 5.2 million guests.
Marriott partnered with Starwood in 2018 and was unaware of the unauthorised access that fraudsters gained in 2014. This was the first data breach for Marriott. The second attack was a third-party data breach and phone numbers, account details, and other sensitive information were compromised.
LinkedIn and Twitter
LinkedIn’s data breach was yet another successful attempt at fraudsters back in June 2012. The attack impacted 165 million LinkedIn users and the password-reset notification only indicated 6.5 million user accounts that were accessed. The actual number was unknown until 2016 when reports stated that approximately 165 million users were impacted.
Another popular social media platform, Twitter, was also under a data breach attack in 2018 and around 330 million users were impacted. Twitter notified all the users that there was some glitch that unmasked passwords and the internal network can access them through the internal log. The giant said that there was not a breach but reports and users showed suspicion. The actual number was never disclosed by Twitter and encouraged all users to update passwords.
Read more about data breaches: Data Breaches in 2019 – A Year in Review
Impact of Data Breaches on Businesses
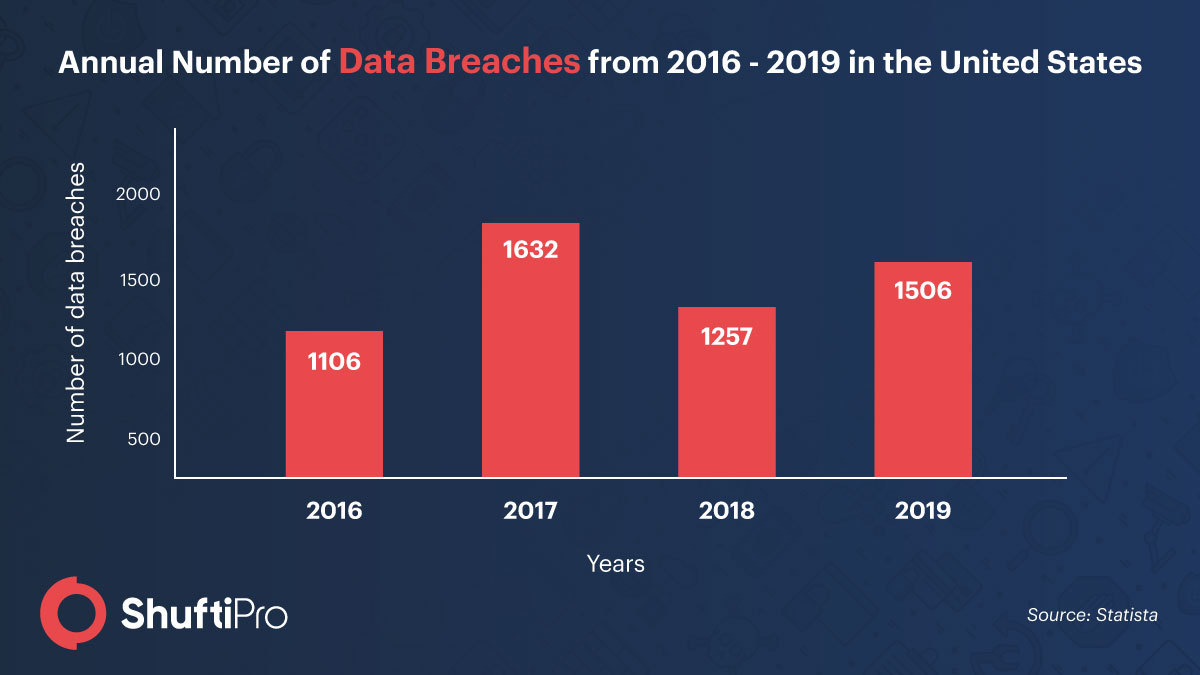
Data breaches have never ended well for organisations and the increasing number is another big issue that needs to be addressed. The US has reported 540 data breaches in the first half of 2020. God knows where these numbers will end on a global scale. One of the most terrifying effects of data breaches is the damaged reputation of the company. Building customer trust is the priority of all businesses and a data breach can exploit trust in no time. Customers provide information for verification purposes with the trust that their information is secure with the organisation and all of it goes away in seconds. A report from PwC states that 85 percent of the customers do not shop from businesses that were under a data breach attack. Hence, protecting the platform is essential so that you can retain customers.
Amid the bad repute of the company, businesses also suffer from huge financial losses every year. According to reports from Juniper, cyberattacks cost businesses two trillion dollars in 2019. God knows how 2020 will end for companies when everything has digitised. Hefty fines from the government are another big loss.
Apart from the catastrophic damage, companies also have to face the loss of data like blueprints, designs, campaign plans, and other confidential information.
How Can On-Premises Verification Help?
Verifying customers has been a necessity in different industries for a long time. It ensures that legitimate customers are onboarded and fraudsters stay away from the organisations. Banks, insurance companies, fintech firms, and several other sectors are under data breach attacks every year. This not only makes digital verification for customer onboarding a strategic priority, but there must be an effective solution for the data stored on the cloud storage during onboarding and verification.
Considering the need, there must be an on-premises identity verification solution in every sector so that no data is available for fraudsters’ benefits. Adopting an on-premises identity verification neither affects the accuracy of the results nor it consumes extra time. The benefit is that none of your customer’s data is stored in a database. You and the end-user can view the data only during the verification process.
It All Boils Down To…
Sophisticated plans from criminals are making it challenging for organisations to avoid data breaches. Fraudsters are coming up with better strategies for their devilish plans. All businesses can do is either protect the data with enhanced security measures or choose on-premises identity verification that does not store any record. Shufti’s on-premises identity verification solution ensures that you onboard legitimate customers and do not store any of their data that fraudsters can exploit. You can prevent huge financial losses, customer dissatisfaction, and bad brand image like other businesses by providing robust verification and on-premises that ensures all the benefits.
Get in touch with our experts to know more about on-premises identity verification.

 Explore Now
Explore Now













