7 Identity theft protection practices for Business and Recuriters

Identity theft is now no more a cause of concern for the individual users only as corporations and businesses around the globe have also started feeling the heat from frequent data breaches and employee frauds because of lax identity theft prevention measures. In 2017, there were 1,579 data breaches that exposed 179 million records held by businesses. According to the same study, account takeover was the most frequent method of identity theft used by online identity thieves and it took at least a few months before a user got to know that their identity was even stolen by someone else.
A smart question to ask here is that what does a business has to do with the stolen identity of a user? Well! It is important to understand that current employees hold several assets – financial or administrative – that can be exploited by identity thieves for personal benefit that will eventually lead to losses for businesses. Moreover, a stolen identity can be used to land a job at a prestigious job opening as well. According to The Federal Trade Commission, most common types of identity theft are:
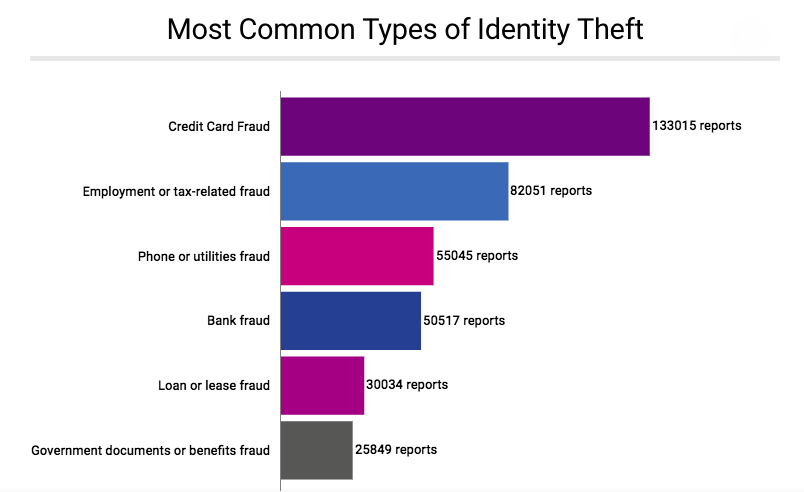
Source: Federal Trade Commission
Now, it does not take a degree in cyber crimes or special expertise in identity theft protection to understand the dangers attached to identity theft for businesses. Most companies use credit cards for business expenses and the 2nd most frequent type of identity theft is employment fraud which means in the absence of a reliable KYC verification, job candidates can use a stolen identity to land a job that they are not fit to perform and who can guess about the true intentions of a candidate that uses fake personal information to get a job.
How Identity Verification is relevant to you?
We understand that there is still a lot of confusion in the business community, especially in Small and Medium-sized Businesses (SMB) that should they be using OCR based ID verification and KYC solutions to implement fraud prevention and identity theft protection. Most of them are stuck to cost spendings that have to be allocated for KYC verification, but they need to appreciate the value of financial risk that is thwarted by every KYC check. It is better to spend a moderate amount on a KYC software rather than losing a significant chunk of revenue through identity theft or online frauds.
Based on studies done regarding online identity thefts, businesses require identity theft prevention to fight off:
- Job candidates with fake credentials
- Online scammers from adopting the identity of one of their employees
- Data breaches that can potentially leak customers personal information
- Unauthorized Access to centralized company resources
There are many other scenarios that can be quoted here to explain the significance of Identity verification services, but today we want to discuss the need for Digital KYC in the recruitment process and internal operations of a company. We will be addressing online fraud prevention practices that can not only protect individual identities of your employees but can also help secure the business interests of your companies.
Identity theft protection
Companies and businesses operating all over the world collect personal information from their workforce. Starting from interview phases to eventual hiring and going till payment disbursements, there are various points in a company’s life cycle in which personal information is collected and in case of any changes (e.g. address, phone number, emergency contact number etc.), the employer wants their employees to get their personal file updated accordingly with required departments (accounts, HR, Admin etc.)
Having the best identity theft protection available for internal operations becomes trickier for businesses that have remote working jobs to fill or have a centralized governance model for branches and offices located in different cities. For multi-national companies, having operations spread out to several continents, things become even more complicated with the threat of identity verification becoming more real than ever in the modern age of data breaches and dark net-based data black markets. All such companies need ID Verification and KYC verification not only to hire employees with genuine credentials but also to adopt identity theft protection measures to secure the corporate and personal information of their employees.
-
Adopt Best Practices for Identity theft Protection
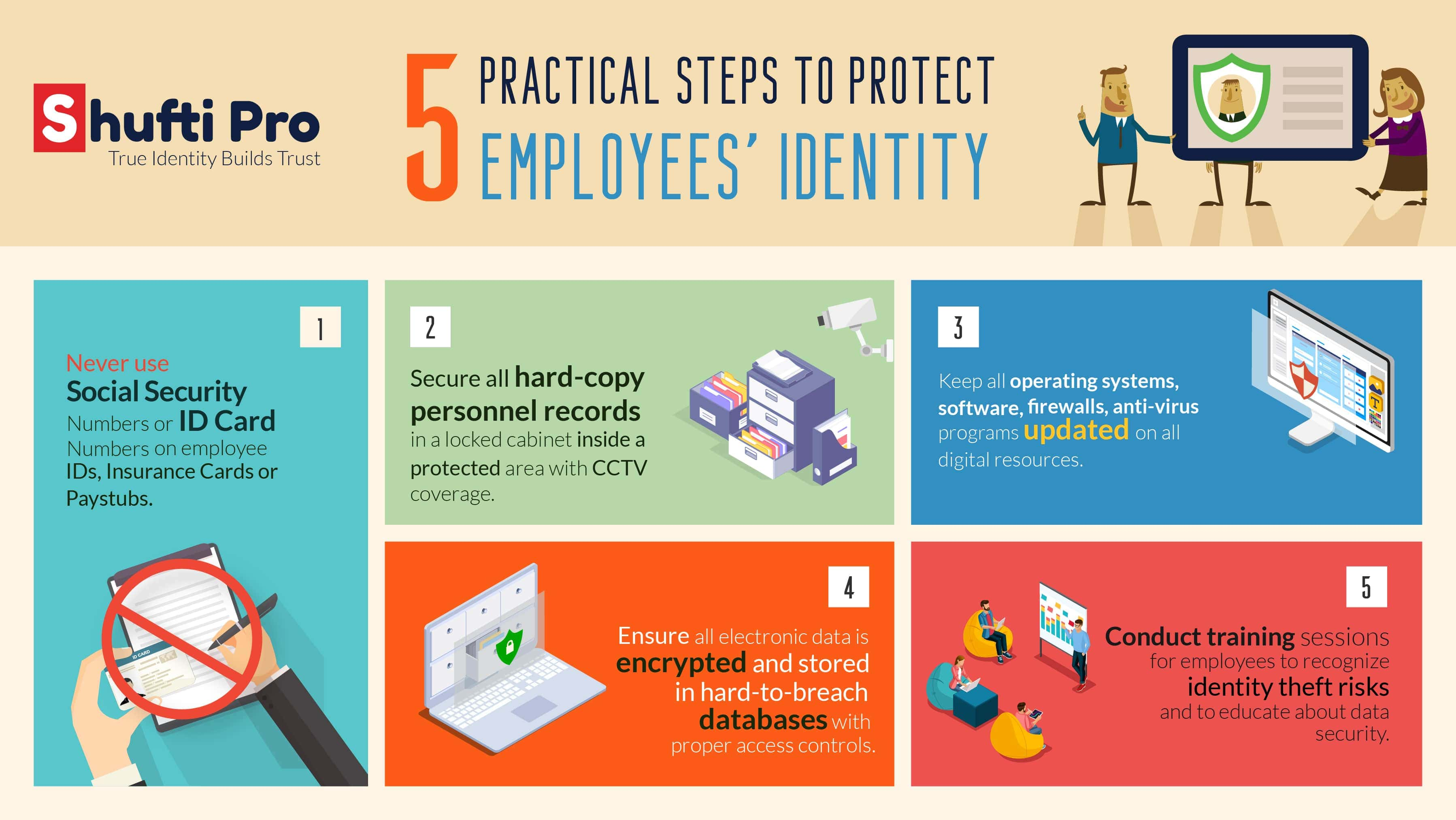
All over the world, companies and businesses are adopting strict measures to ensure that all the personal information of their employees is secured. Identity theft prevention requires that only a select number of employees have access to such information. Financial Information of the company employees is also kept safeguarded both in hard copy as well as the soft copy to ensure that record is kept safe in case, any of the two set of records is damaged during a natural or digital disaster.
Most companies not only take measures to apply all necessary checks to thwart any attempt of identity theft but also involve their workforce into their identity theft protection practices. In order to achieve this, regular training sessions are conducted to make sure that the workforce is well versed with the idea of identity theft, how online identity theft prevention works and what they can do to ensure that their personal or professional information does not land into wrong hands.
One of the most common methods to ensure that personal information of employees is not compromised is by ensuring that the Social Security Numbers (SSNs) or other important Identity Document numbers are never published on employee ID cards, pay stubs or on their insurance cards. Any identity thief will have its work cut down in case they ever get hold of such a trivial yet informative document.
When it comes to identity verification and fraud prevention tactics, the entire system is more of a “House of Cards”. One wrong move and the entire system of online fraud prevention can come down like a sand castle.
-
Use Biometric Verification
Biometric Verification is a preferred mode of verification for most companies performing functions such as Check Out attendances to providing secure access to centralized resources. Now, it is perfectly fine identity theft protection solution for on-site verification but in case of remote workers, trying to access centralized resources, biometric verification requires higher budget if you utilize only conventional mediums of biometric verification i.e fingerprint scan or iris scans. It will either require special smartphones with the ability to verify fingerprints or special hardware for performing iris scans.
Facial verification is a much more reliable source of biometric verification, requiring no special hardware equipment. Either a phone camera or a webcam can be used to recognize unique facial features of a verifying member of the workforce. Shufti is a perfect KYC verification and online identity verification solution offering facial verification using Artificial Intelligence. You can use it with document verification to perform full fledge identity verification not only for an existing employee but for a newly hired employee as well, both for onsite or remote duties. Remote hiring process becomes fully automated and secure for companies with the help of identity verification services from Sufti Pro.
-
Secured Centralized Assets
Businesses having a centralized database or knowledge base that has to be accessed by only select few, can surely take help from ID verification. To make the process entirely hassle free and easier. Already, businesses are asking for integration of OCR technology into KYC software, something that has been achieved successfully by Shufti. With Broad language support and Artificial Intelligence working acting as the backbone of Shufti, secure access to centralized assets becomes a piece of cake, without having to worry about identity theft. Only a person with genuine credentials can access personal records of employees of a company, making the entire procedure air-tight as far as fraud prevention and identity theft protection is concerned.
-
Financial Vigilance & Auditing
Business and corporations usually use credit cards for financial transactions and in order to pay for various office-based expenses. In order to make sure that your business has not become a victim of a credit card fraud, you need to check vigilantly for all the credit card statements and cross-check them with accounting departments in order to make sure that all the purchases performed via company credit cards are accounted for and in line with business side needs of the company. You find a single red flag, even a purchase of a few dollars that looks dubious or suspicious, don’t take it lightly.
-
Set Usage Ethics for Work Resources
Companies allow their employees to use company resources (laptops, Wi-Fi devices, and smartphones) even from their home in order to allow for flexible work environment. All employees availing flexible working hours must be fully told about their responsibilities regarding identity theft protection. They must know that they cannot save confidential information on these digital resources and neither can lose them, otherwise all of your company’s resources will become vulnerable to an identity theft attack.
-
Collect Consent for Verification
If you intend to verify the personal information of a would-be-employee through a KYC software to ensure identity theft protection, make sure that you collect proper consent from that candidate. Governments requires companies and businesses to receive the consent of a user before any KYC check is performed against their provided information. Apart from a compliance requirement, it is courteous to give a potential candidate a necessary heads up for a KYC verification.
-
KYC verification with real-time results
There is no better way to use the best identity theft protection except for using KYC verification from Shufti that is available in 225+ countries and supports over 150 official languages. Several verification services are offered by Shufti and even more KYC verification solutions using a mix of various technologies and verification services. The 4 verification solutions from Shufti includes:
Identity Verification – Shufti can verify the identity of an end-user using a mix of facial verification, document verification, address verification, and 2-factor authentication. All the personal information can be collected in less than 1 minutes and verification results are presented in real-time.
InstantCapture – This identity theft prevention solution is developed by Shufti to make the entire identity verification process easier to perform for end-users. Using OCR technology, Shufti can extract personal information from an identity document including ID cards, driving licenses and passports.
AML Compliance – Most companies require to check for financial risk attached with a person before they hire him, even for a remote working position or for the post of a consultant. Shufti has a large databank containing financial risk information from 3000 databases and profiles from 1000+ sanction lists and watchlists.
Biometric Consent Verification – Released just recently, Biometric Consent Verification is the most secure format of identity verification that makes identity theft virtually impossible. Of all the KYC solutions from Shufti, Biometric Consent Verification is the only solution that offers support for both customized identity documents (employee cards, special access cards etc.) and handwritten note verification.
In case any business doesn’t want to avail a full KYC verification solution from Shufti and wants to use any individual verification service from Shufti, they can do just that as Shufti has designed its entire SaaS product with flexibility being the core feature for its customers. Shufti offers following verification services to its global clientele:
- Customized Document Verification
All these identity verification services and identity theft protection solutions are perfect for authenticating the true identity of a job candidate or in case you ever find that a person claiming to be one of your employees is actually your employee and not someone who just got hold of personal or professional information of the employee that he/she claims to be.
Shufti is offering a free trial to all the businesses who want to check the prowess of our verification services. Contact us now, if you also want to adopt a hard-to-breach identity theft protection for your remote recruitment and internal operations.
Recommended For You:
- How Identity Theft Protection Can Increase Your Profit!
- Social Media and Identity Theft Frauds
- Biometric identification Analysis and Facial Recognition Technology

 Explore Now
Explore Now














