5 Best Practices to Combat Identity Fraud on Social Media Platforms

Social media has demonstrated extraordinary growth in the past decade as a result of improvements in internet speeds and availability. According to statistics, 5.4 billion people in the world use mobile phones, which is 69% of the population. 91.4% of companies use social media for the purpose of marketing and improving brand awareness.
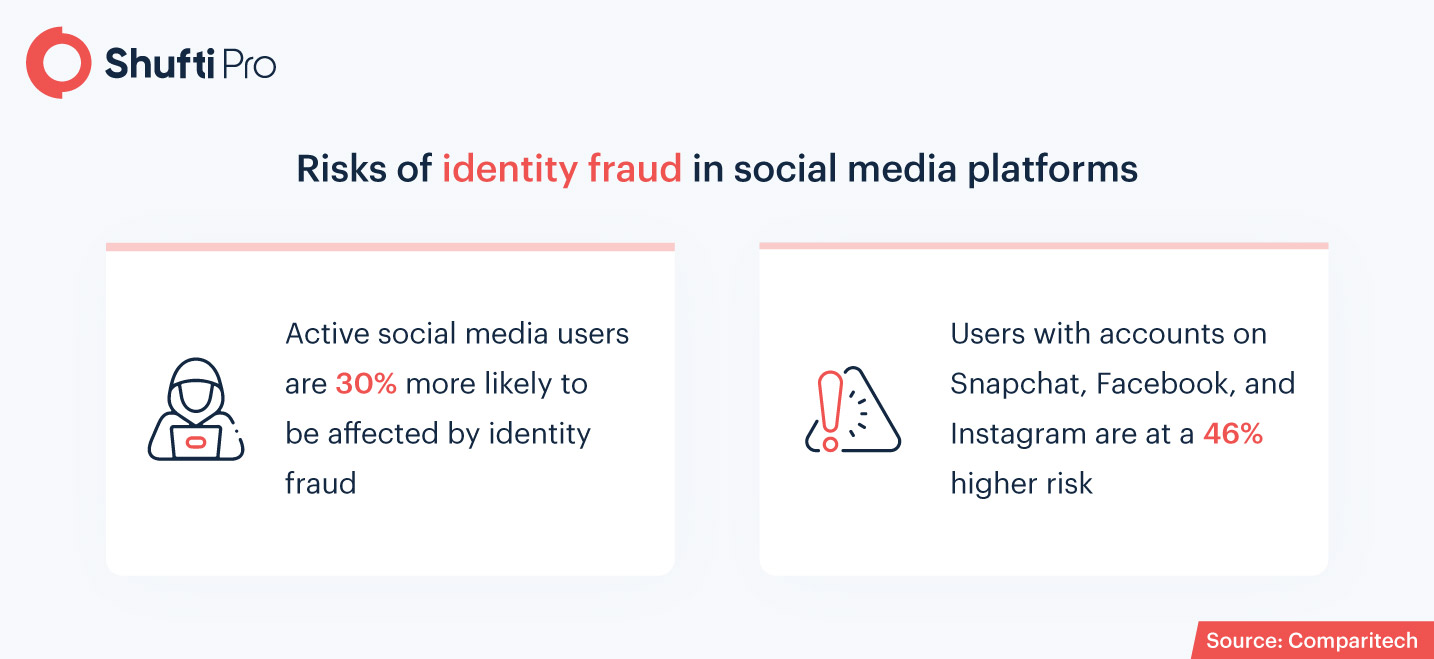
However, this popularity of social media doesn’t come without flaws and actually makes individuals and businesses quite vulnerable to identity fraud. This is proved by 49% of global social media consumers that are not willing to share their information with businesses on social media, and 33% of them lost trust in social media companies after being victims of scams.
A Spike in Social Media Scams
According to the Federal Trade Commission (FTC), social media scams in 2020 tripled in number from 2019, with a significant spike in the second quarter of 2020. These scams are mainly made possible due to the publicly available personal information on social media, as a Javelin report highlights 68% of the users share their birthdays and 45% of them mention the complete birthdate. Fraudsters exploit this kind of information provided by business pages on social media and use it to create fake profiles. These profiles are then used to trick people with fake income opportunities, giveaways, and online shopping fraud.

According to an ITRC report from early 2021, there has been a decrease in cybercrime through direct manipulation of business profiles into giving up their information, as fraudsters now resort to stealing identity-related information, usernames, and passwords by taking advantage of social media platforms. Considering the ongoing trends, social media platforms need to re-think their security measures and incorporate technology-driven solutions.
Secure Connections
Since financial gains are the common motive behind identity theft, securing payment methods, bank account information, and business networks are of equal importance. Businesses on social media platforms can reduce data losses due to identity fraud by securing their connections. This involves limiting entry points and cloud storage access to specified business personnel and creating backups of data.
Antivirus and Firewalls
Generally known measures for preventing identity theft include antivirus software and firewalls, which are now also available in the form of cloud-based services. Antivirus software assists businesses in the prevention of identity theft by detecting abnormal activity on the internet. It also allows monitoring of emails and bank accounts to protect confidential information.
Firewalls were invented when Microsoft faced the constant issue of cyberattacks in the 1990s, and are barriers created for protecting personal information by filtering the data going through an internet connection. If incorporated correctly, firewalls can help significantly reduce the risks of identity theft on social media by shutting down processes in case of unauthorized access.
Identity Verification
The primary reason why social media platforms make businesses vulnerable to fraud is the lack of identity verification measures, which leaves the door open for numerous fake accounts with the same name. Identity verification in social media can prevent the creation of fake business pages and scams that lead businesses to face monetary losses. That being said, enhancements in technology have given way to digital solutions making use of thousands of AI models to provide a sigh of relief to businesses.
Face Verification
In the past decade, the use of biometrics for verifying identity has proven to benefit business platforms and several other sectors due to the accuracy and convenience it provides. The global facial recognition market size in 2020 was valued at USD 3.78 billion and is expected to rise up to USD 10.2 billion by 2028. Biometric face verification not only eliminates the need to remember complicated passwords and PINs but also makes it easier to secure personal information using unique facial characteristics.
Shufti’s face verification solution assists businesses on social media platforms in diminishing identity fraud by preventing the creation of fake accounts. Making use of AI and deep learning, face verification allows verification in less than a second with an accuracy of 98.67%. This is achieved with the help of integrated technologies including 3D depth analysis, liveness detection, microexpression analysis, and AI mapping. Incorporating face verification in the registration process enables social media platforms to determine the true identity of the person trying to create an account, hence eliminating fraudulent activities.
Document Verification
Social media platforms collect data and allow traffic at a bewildering rate regardless of the nature of users, which often backfires due to numerous illegitimate accounts. Businesses running marketing campaigns on social media are susceptible to fraud as they provide their addresses and contact information on their pages. Unless identity verification processes are implemented, social media will continue to provide anonymity to fraudsters that aim to capitalize on publicly available business data.
Document verification is one such solution for restricting social media access for bad actors by requiring them to upload original government-issued documents. Shufti’s document verification solution uses an AI-driven engine to verify documents uploaded by registering users, ultimately allowing businesses to promote their products through a secure platform. The seamless verification process uses OCR technology to detect and verify 3000+ document types.
2-Factor Authentication
Protection of information on the internet is an issue faced by several industries like the financial sector, healthcare, and online gambling. The General Data Protection Regulation of the EU provides guidelines for ensuring data security and defining the purpose of data collection. However, social media platforms hardly provide data protection, as fraudsters commonly steal personal details to create clone accounts and use someone’s name for their own benefits.
Social media platforms need to establish guardrails against identity theft and business scams using a robust verification solution. Shufti’s 2-factor authentication allows social media platforms to place an additional layer of security in order to stop fraudsters in their tracks. 2-factor authentication requires an additional code sent to the user via email, SMS, or call as per their choice. Upon entering the code, Shufti’s 2-factor authentication solution verifies the user in less than a second.
NFC Verification
Several surveys about identity theft and social media scams have indicated that the majority of individuals are not concerned about protecting their information on social media. Another reason why social media platforms shy away from verification measures is the assumption that a lot of time is consumed to verify users’ identities.
Even though it is based on relatively older RFID technology, the processing time of NFC (Near Field Communication) verification is less than a second. Shufti’s NFC verification provides a faster alternative to authenticate users on social media platforms, where they simply have to upload an image of their NFC-enabled ID document to get started. The users then just have to tap the NFC chip on the device to get verified in less than a second.
Key Takeaways
Growing a business through social media platforms requires consistency and legitimate traffic, which cannot be achieved unless the platforms are secured. Both the business and its customers are deprived of the desired services and profits when fraudulent entities step in and manipulate confidential information to create fake accounts. Shufti’s identity verification solution helps businesses run their processes smoothly while ensuring customer satisfaction. By verifying the identity of users visiting social media platforms, the risks of fraud can be significantly reduced.
Want to learn more about KYC for your business?

 Explore Now
Explore Now













