A Basic Guide to Smurfing and the Role of AML in Combating It

Scammers employ various strategies to conceal illegally acquired funds, and one increasingly prevalent method is smurfing. It is important to note that not all forms of money laundering involve smurfing, and not all individuals acting as money mules can be classified as smurfs.
Smurfing refers to laundering money by fragmenting it into multiple smaller sums to bypass detection. Money mules who employ smurfing aim to avoid suspicious activity reporting thresholds by conducting numerous small transactions, thereby minimising the likelihood of arousing suspicion. Another type of smurfing is associated with fraud in professional gaming and real-money gaming, which involves the creation of multiple users accounts to manipulate the platform or rankings.
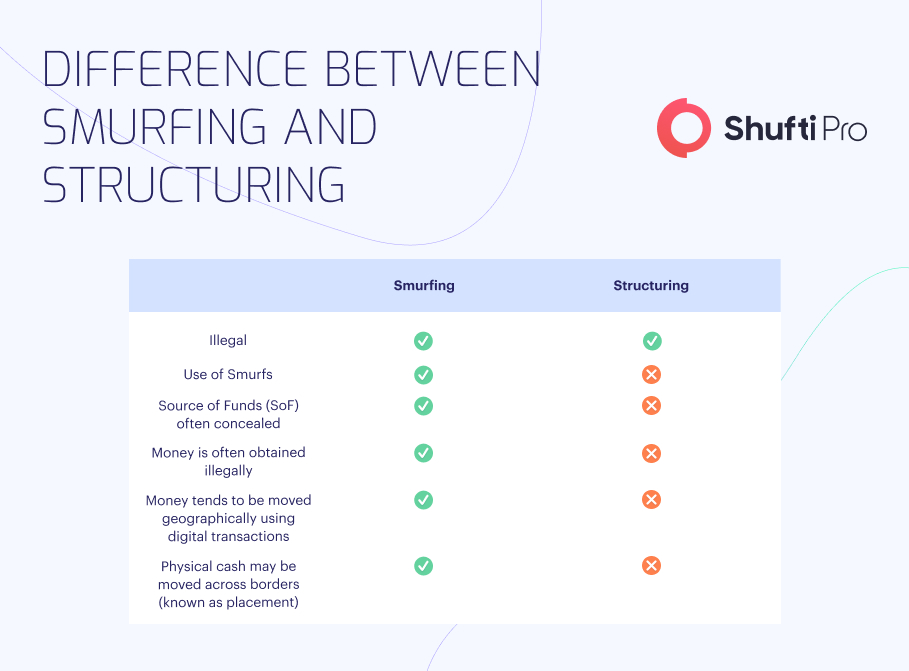
Smurfing vs Structuring
Although smurfing and structuring involve dividing large sums of money into smaller transactions, their goal and execution make them different. Smurfing primarily aims to bypass regulatory authorities’ detection and mask the laundered funds’ true origin and nature. On the other hand, structuring is primarily utilised to avoid reporting requirements without concealing illicit fund sources.
Another significant difference between both is their detection, as well as prevention methods. Financial firms and law enforcement agencies use various methods to identify and prevent smurfing and structuring activities. These measures include monitoring transactions that exceed reporting thresholds and investigating suspicious behaviour. However, smurfing is generally regarded as more challenging to detect due to its intricate nature involving several individuals and accounts, rendering it a more sophisticated type of money laundering.
How Does Smurfing Work?
Smurfing is a form of money laundering carried out by smurfs who act as money mules. For example, in 2016, the former head of the US Transport Security Administration, Kelly Hoggan, was removed from his position due to improperly awarding himself a bonus of $90,000. Hoggan divided the amount into nine payments of $10,000 instead of a single lump sum to conceal this activity. However, he was eventually apprehended.
The process includes the following:
- The Smurf receives unlawfully acquired funds.
- The funds are divided into smaller amounts, digitally or physically, just below the threshold that would trigger detection, reporting, or alert mechanisms.
- The smurf, individually or in collaboration with others, then launders or moves the funds separately, treating each smaller amount as a distinct entity.
- Once each smaller sum has been laundered independently, it can be merged into a single account if necessary.
- The criminal ultimately receives the funds.
What is Smurfing in Banking?
In banking, smurfing takes various forms, including money laundering and specific practices such as money mules and cuckoo smurfing.
Money mules willingly provide their personal information to criminals, enabling them to carry out specific tasks. These tasks often involve opening new bank accounts, granting access to another person, or facilitating certain transactions. Money mules typically engage in these activities for monetary gain.
On the other hand, cuckoo smurfing is a particular method employed in money laundering. Its primary objective is to create the illusion that funds originate from legitimate sources. This can be achieved by fragmenting substantial transactions into smaller ones through intermediaries or “cleaning” the money through various means. For instance, one approach could involve exchanging the funds for casino chips and requesting a refund.
Both of these methods fall under the broader category of smurfing, as they involve distributing funds among multiple third parties to launder them.
What is Smurfing in iGaming?
Smurfing takes on a different meaning in iGaming, which includes betting, online casinos, poker, and other real money games played on the internet. It involves setting up secondary accounts, regardless of whether they are permitted on the iGaming platform.
Smurfing in iGaming serves various purposes, including:
- Matching with unskilled players without revealing your actual skill level.
- Experimenting and learning without impacting the statistics of your main accounts.
- Engaging in multi-accounting as part of fraudulent activities, such as claiming unauthorised bonuses or facilitating scams like matched betting or arbitrage.
While most online real-money gaming providers prohibit multiple accounts per person, smurfing in iGaming is generally disapproved of or explicitly denied. Unlike smurfing in banking, it typically does not involve criminal activity. Furthermore, it’s worth noting that smurfing also extends to multiplayer and online video games in general. In these scenarios, skilled esports players often create alternate accounts to compete against unskilled players for benevolent and malevolent reasons.
Significance of AML Compliance Measures
The surge in money laundering cases poses a significant issue across various business and economic sectors. Therefore, it is crucial to establish policies and protect systems from this illicit activity. By implementing Anti-money Laundering (AML) solutions, financial institutions can effectively monitor transactions, scrutinise suspicious activities, and authenticate users. This proactive approach enables the early detection of unusual behaviour and keeps scammers at bay. Not only this, but it ensures compliance with regulations and prevents businesses from hefty fines.
How Can Shufti Help?
Shufti’s AML solution safeguards businesses from smurfing by providing comprehensive transaction monitoring and analysis. Our robust AML solution helps detect unusual patterns within seconds, identify potential smurfing activities, and enables enterprises to prevent money laundering and financial crime.
Find out more about how an AML solution can help protect firms from detecting certain crime types.

 Explore Now
Explore Now













