eIDAS and eIDs – The Shift in Identity Verification in the EU & Beyond

- 01 Impact of the eIDAS Regulations
- 02 EIDAS Regulations for the United Kingdom
- 03 Amalgamation of eIDAS and AMLD - Digital Single Market
- 04 The Legislative Framework for ID Verification by eIDAS
- 05 Interoperability of eIDs as per eIDAS
- 06 Shufti’s IDV Suite - Answer to the Shifting ID Verification Trends
- 07 In a Nutshell…
In the digital world, ensuring the security of international transactions is the ultimate goal of all companies. The European Union’s eIDAS or Electronic Identification and Trust Services legislation monitors identity verification, authentication and electronic transactions in the region. This legislation allows secure cross-border transactions and removes all digital barriers. Moreover, creating a predictable regulatory environment for a secure and swift electronic transaction system is a lot easier with eIDAS.
Let’s take a look at how identity verification has shifted in the EU.
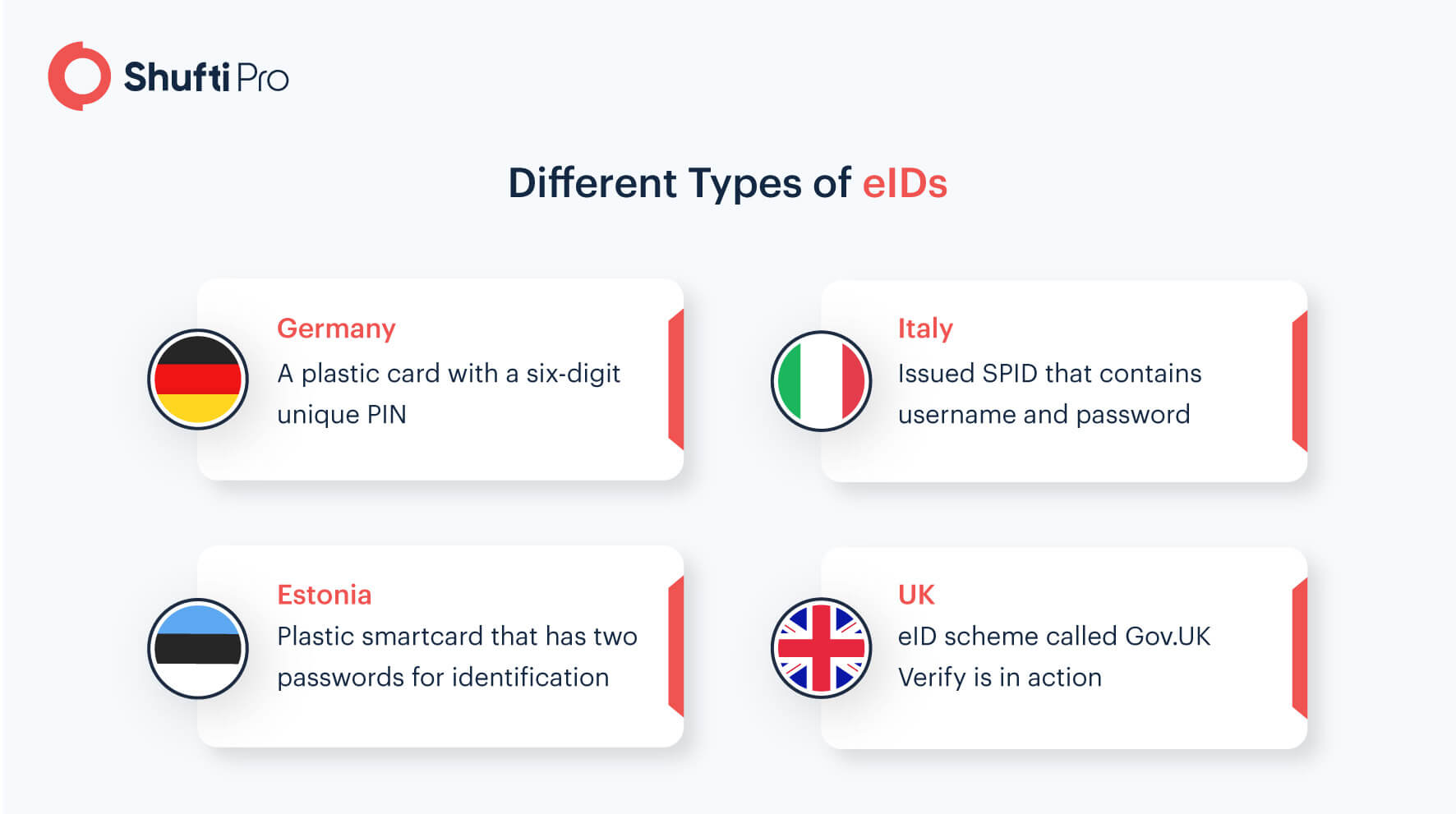
What is an eID?
In the high-speed digital space we live in, the conventional government-issued ID documents like passports and ID cards are no longer effective. So, electronic or chip-based ID documents are now in use in many countries. The chip in this document contains all data about the individual allowing seamless ID authentication and verification in organisations.
Impact of the eIDAS Regulations
The regulations from the eIDAS:
- Ensure that everyone can use their electronic IDs to access public services available in any EU region
- Create an international market for trust services like e-signatures, e-seals, time stamps, etc. by ensuring that they will work across borders along with the same legal status as the paper-based ones
EIDAS Regulations for the United Kingdom
The electronic identification and trust services for e-transactions in the internal market are regulated by the eIDAS regulation 910/2014. However, the UK adopted eIDAS regulation and altered the regulations post-Brexit. Additionally, the Electronic Identification and Trust Services for Electronic Transactions Regulation 2016 was also changed. Now, these guidelines are referred to as the UK eIDAS laws.
Companies offering trust services in the EU have to comply with eIDAS laws of the European Union. This also includes operations under the supervision of a regulatory body from a different EU state.
Amalgamation of eIDAS and AMLD – Digital Single Market
The EU created a ‘Digital Single Market’ by incorporating Anti-Money Laundering (AMLD) with the eIDAS regulations. The digital single market brings uniformity in customer onboarding. Organisations across the European Union can remotely verify customers making customer onboarding frictionless.
The eIDAS regulation article 920/2014 provides AMLD with the control to verify and onboard clients in a safe, simple and remote way by removing all barriers in the customer acquisition process.
Suggested: | 6AMLD of EU – A detailed insight
The Legislative Framework for ID Verification by eIDAS
As per the eIDAS regulations, standards for digital identification are:
- Create a credible ecosystem with maximum technical sureties to secure individuals and companies
- Article 24 of the legislation avoids the personalisation act before getting a certificate in the Registration Entity and allows identity verification through video calls (generally called the video KYC process)
- Consequently, it allows new licenses in eIDAS laws that lead to new digital identity verification mechanisms without harming the security of the processes
- The eIDAS laws introduced digital identity verification methods for the first time in history. This reduces the physical interaction between companies and customers
- The financial and telecommunication sectors are now capable of acquiring customers digitally anytime. The framework established by the eIDAS is entirely new for organisations and end-users
- Apart from all these, eIDAS and AMLD5 together have reduced costs and saved time along with a great user experience during the customer onboarding process
Interoperability of eIDs as per eIDAS
Given the differences in eIDs across countries, the main goal of the eIDAS is to remove all sorts of barriers for identification. For instance, an individual with an Italian eID residing in Estonia should not be bound to use the Estonian eID. To ensure interoperability of the eIDs, the eIDAS is working on an IT infrastructure called eIDAS nodes.
Shufti’s IDV Suite – Answer to the Shifting ID Verification Trends
Electronic or eIDs have changed the identity verification game. Now, customers believe in the digital process rather than physically visiting the company. However, the change in identity verification is not a problem anymore. Shufti offers multiple alternatives for one problem. Although all our ID verification services are remote, there are two options that can help every firm irrespective of their industry. Let’s take a look at both of these:
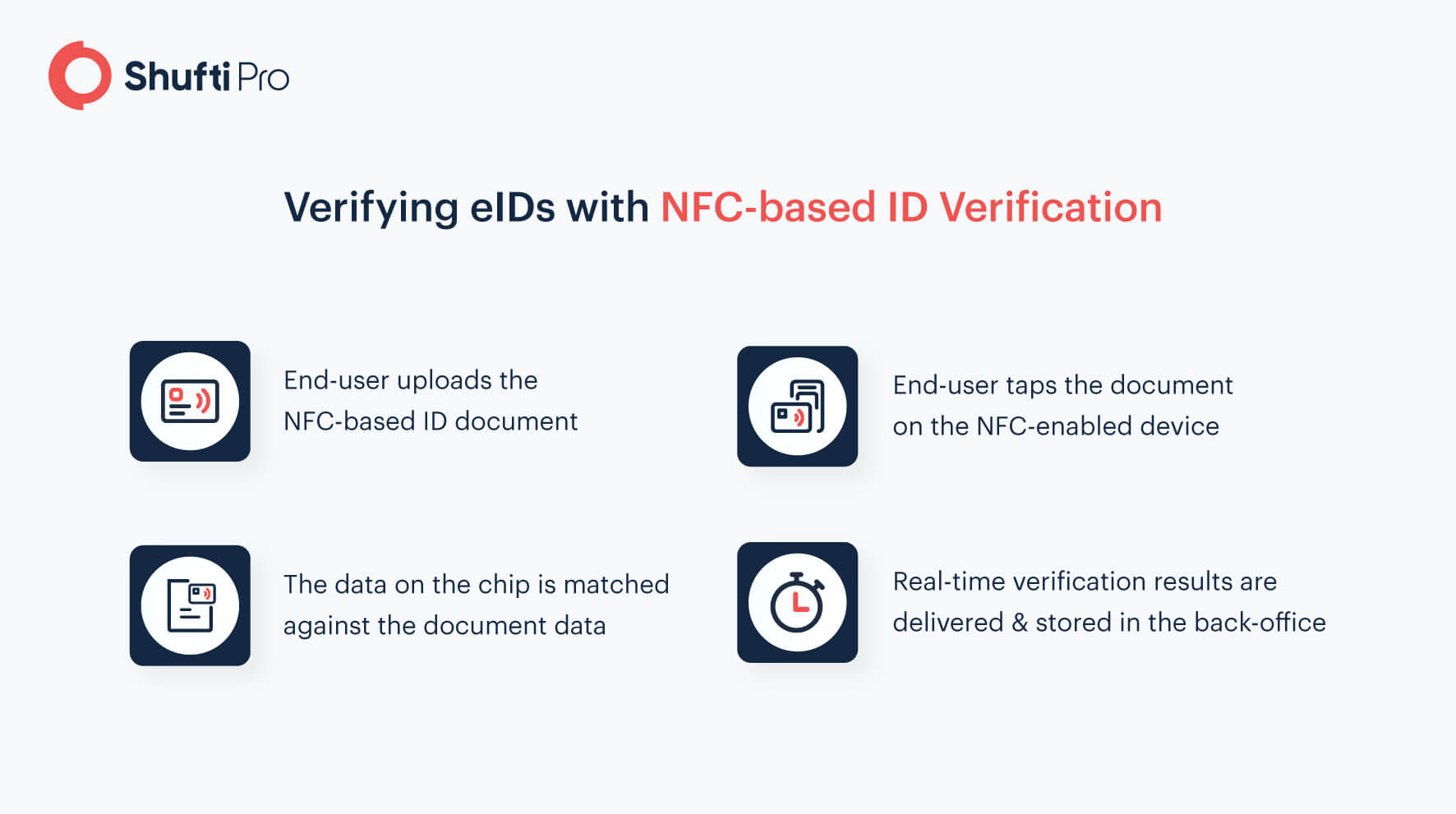
1. NFC-based ID Verification
The chip in eIDs allows businesses to verify the identities of end-users in the blink of an eye. NFC-based identity verification validates identities through a tap on an NFC-enabled device.
Here’s how the process goes:
2. Video Interview KYC
Video KYC is another remote identity verification solution that we offer. During the video KYC process, the end-user gets in touch with the KYC expert on a live video call for authentication. The process has seven simple steps:
- End-user registers on the company’s platform for KYC
- KYC expert and the end-user get in touch on a live video call
- The expert interviews customers for liveness detection
- End-user shows the government-issued ID documents during the call
- The document is verified for forgery and tampering
- The face of the end-user is matched against the image on the ID document
- Verification results are delivered and stored in the back-office
Note that the process is lengthy but takes only a minute or two to complete.
In a Nutshell…
Electronic or biometric identities are now a more convenient option for identification. The eIDAS issued guidelines on remote identity verification and seamless cross-border transactions in the European Union. The interoperability of eIDs across member states is still under consideration. However, eIDAS is working on an IT infrastructure to remove hurdles for cross-border use of eIDs. The laws also state multiple methods for remote identity verification and fortunately, all of Shufti’s identity verification solutions validate IDs remotely. The two most appropriate services for the EU member state and the UK are Video Interview KYC and NFC Verification.
For more information, get in touch with our experts.

 Explore Now
Explore Now













