How can AML play a role to impede the financing of terrorism?

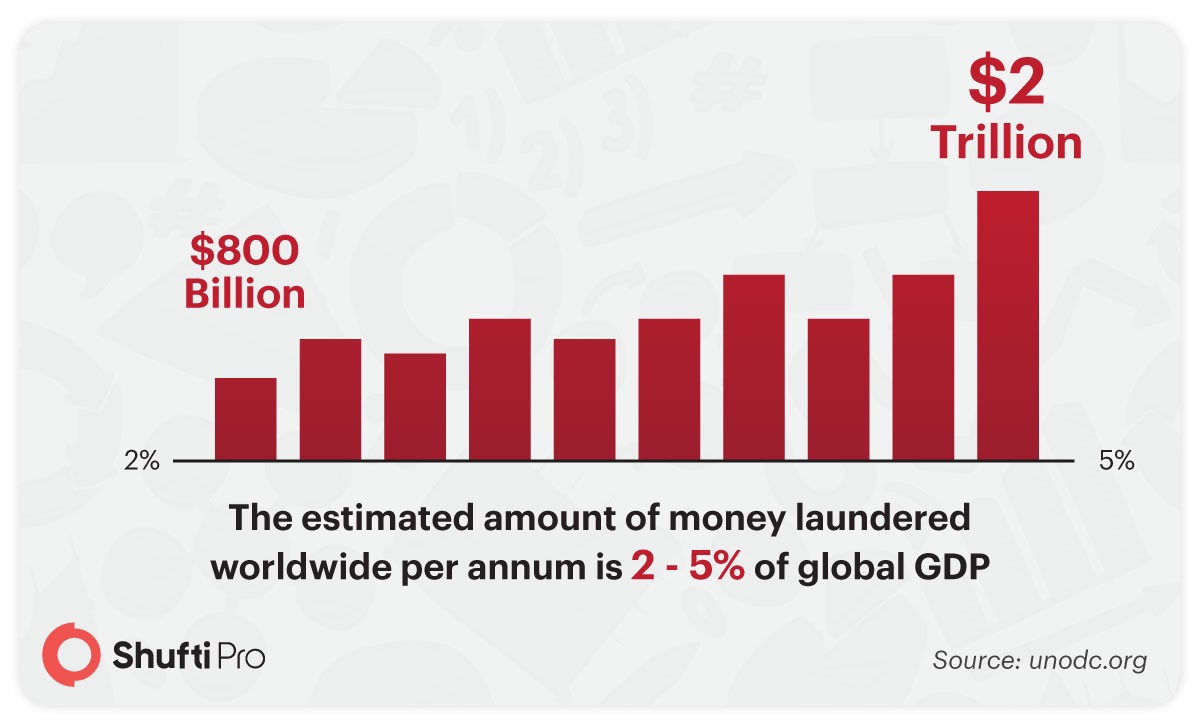
Money Laundering and Terrorism Financing are global issues and there is no dispute regarding it. Every year, billions of dollars are lost due to money laundering. According to a study by UN Office on Drugs and Crime, the estimated amount of money laundered worldwide per annum is 2 – 5% of global GDP, or $800 billion – $2 trillion in current US dollars. Money laundering and financing of terrorism have been going on for a very long time. Keeping in mind the immense loss that has to be encountered, global regulatory authorities set up compliances that were required to be followed by all financial institutions and banks. But before going into that detail, let’s get a glimpse of when were the AML and CFT regulations initially introduced?
What is AML/CFT?
AML/CFT means Anti-Money Laundering and Counter-Terrorist Financing. Both of these are a solution to fight illegal actvities of fraudsters. Money laundering and terrorist financing are two of the deadliest crimes that threaten the entire economy. AML/CFT are laws from the regulatory authorities to combat them.
Background of Money Laundering and the Financing of Terrorism
On 9/11, 2001, a tragic terrorist attack took place in which 19 militants related to the extremist group al Qaeda hijacked four airplanes and administered suicide attacks against targets within the United States. Two of the planes were flown into the dual towers of the World Trade Centre in New York City, a 3rd plane crashed into the Pentagon just outside Washington, D.C., and the fourth plane crashed in an open field in Shanksville, Pennsylvania.
Approximately 3,000 people lost their lives during the September terrorist attacks, which led to major U.S. initiatives to fight terrorism under the presidency of George W. Bush.
To carry out the attack, the 9/11 planners spent between $400,000 and $500,000, which was majorly provided by al Qaeda. Albeit the origin of the funding is undisclosed, detailed inquiry has unveiled about the financial transactions that supported the attack.
The hijackers and their financial facilitators used the anonymity provided by the international and domestic financial system to channel their funds via a number of hidden transactions.
Although the existing financial mechanisms of the country were strong enough to prevent the misuse of the system they were not designed to identify and obstruct transactions that financed state terrorism.
This ultimately led to the development of the KYC process and AML regulations as key components of the US Patriot Act, 2001. Later on, in 2005 the Reserve Bank of India made it mandatory for banks across the globe to adopt these guidelines to prevent the financing of illegal activities.
Read more: 24 scammers arrested on money laundering charges
Introduction of Financial Regulations
International authorities such as FATF and world bank are working with national authorities such as GDPR, FinCEN, FCA, FINMA, etc. and state banks to keep a close check on money laundering activities. Most of the countries are following the guidelines of the financial regulatory authorities such as FATF in impeding crimes such as money laundering.
The Financial Action Task Force or FATF is a global body that provides suggestions to countries with respect to their efforts to restrict terrorist financing and money laundering. The countries mostly follow the 40 recommendations of the FATF to prevent money laundering.
Governments and financial institutions have huge datasets of information regarding their citizens and these lists are regularly updated.
The lists are provided to law enforcement agencies in case any illegal activity is done by an individual, to bring them under the law.
Read more: Financial regulators assure further assistance to the industry during COVID-19
Techniques to Counter the Financing of Terrorism
Traditionally, financial Institutions would examine government-issued identification documents like a driver’s license and/or passport. These documents, generally, should essentially display an image as well as other identification data of the individual. Best practices, however, involve the displaying of multiple documents to diminish the risks presented by counterfeit and fraudulently obtained documents.
Read more: The Definitive Guide to Anti-Money Laundering & Countering of Terrorist Financing
In today’s online era, when consumers deeply value convenience and instantaneity, a visit to the bank to line up an account may be too inconvenient. So why create difficulties for customers, and asking them to physically present themselves, when there are easier and convenient ways to verify themselves online?
Identity verification service providers have built digital identity verification software that seamlessly authenticates the identity of individuals in a couple of seconds. These systems usually involve the use of cutting-edge AI technology that digitally verifies if the individual actually is who they claim to be or not. To make it certain, the software requires the user’s identification details which could be done through facial verification, document validation, address authentication, 2-factor authentication, and consent verification. These digital identity verification techniques conduct an in-depth analysis of the profile of the users to see if they are involved in any sort of money laundering or terrorism financing activities.
The software usually attains information from various data sets and sanction lists that are regularly updated by the international authorities. On-going AML checks can also be adopted to keep a close check on the Politically Exposed Persons or people with a history of suspicious activities.
Wrapping Up…
Money Laundering and the Financing of Terrorism are menaces in our society that need to be eradicated entirely. But this cannot be achieved immediately. It takes years of hard work, technology, policy formulation, compliances, and most importantly, the sheer will to fight these hazards. We should all stand united with our authorities and agencies to catch money launderers, terrorism financiers, and criminals. One of the most effective methods of doing this is by incorporating digital KYC verification into our systems and business processes.











