How to Design an Effective Client Lifecycle Management (CLM) System with ID Verification

The customer journey with a business is very comprehensive. It does not end once the customer is onboarded. It begins with creating awareness about the brand and ends when the customer leaves the company. Creating a state of the art experience throughout the journey requires an effective customer lifecycle management (CLM) system. But how to do this? Designing a top-notch CLM system is no easy job. Nevertheless, you can read this blog and find the six easiest steps to structure the best CLM system that will not only ensure a great customer experience but also help the company in complying with the CDD regulations.
What is Customer Lifecycle Management (CLM) System?
Customer lifecycle management (CLM) is a system that gives businesses the authority to manage every client’s journey with them. From onboarding to offboarding, it is a comprehensive process that links customer relationship management at the front with identity verification checks at the backend.
6 Easy Steps to Design an Effective CLM System
Experts suggest five stages of every customer lifecycle management system; reach, acquire, conversion, retention, and loyalty. Business support executives of Shufti advocate that every stage must be equally effective and as per their recommendations, here’s how your company can create a CLM system that ensures efficacy at every stage.
Refine Your Goals
First things first, your goals must be refined. Vague or broad-spectrum goals have never helped companies in the past. Note that every goal should not revolve around the thought of acquiring more customers in any way possible. This is a broader target and for a good system, you need a goal that is narrowed down as much as possible. Providing a remarkable experience to customers, spreading positive word-of-mouth, retaining customers, etc. are some of the other targets, especially when it comes to designing an effective customer lifecycle management system.
Plan It Out
Now that you have a refined goal, planning phase steps in. Do you honestly believe that you can move forward with the CLM system design without a sound plan? Think again. Your goal is just the beginning. Now, you need to consider the available options, how you are going to choose the best alternative and above all, are these choices going to help you in compliance? It’s not just about onboarding and boosting sales anymore. You need extra security layers in the world where bad actors are crawling everywhere. Henceforth, never overlook this step.
Suggested: How Can You Make Your Onboarding Process Cost-Effective?
Choose Tools to Help You
Everything looks good on the document. It’s time to start implementing all the steps that you stated. Make a list of all the RegTech solutions available. Why RegTech? The regulations have become rigid for businesses and it’s not just about having the best system, companies need to protect customers’ data and get in touch with the legitimate ones only. Along with effective compliance, these solutions will help organisations in developing a lifecycle that can seamlessly onboard customers and assist them 24/7.
Ensure Process Convenience
Customer convenience comes above all other aspects and this is unachievable if the onboarding stage of the cycle (the first impression of your company) is tiring. To ensure convenience, you must incorporate a digital identity verification solution. The AI-based identity verification system will help the company in onboarding legitimate individuals only.
Map the Customer Journey
Never forget to map your customers’ journey. As cliche as it sounds, this is an integral part of the process and you may even call it the heart of the customer lifecycle management. Before onboarding, pre-purchase and post-purchase, every behaviour must be mapped out.
Remediate for More Effectiveness
The regulations for businesses are changing now and then. This impacts the CLM system and the best way to sustain the effectiveness of the system is remediation. Keep an eye on the regulations, latest technological changes and regularly update the system.
Recommended: The importance of KYC remediation
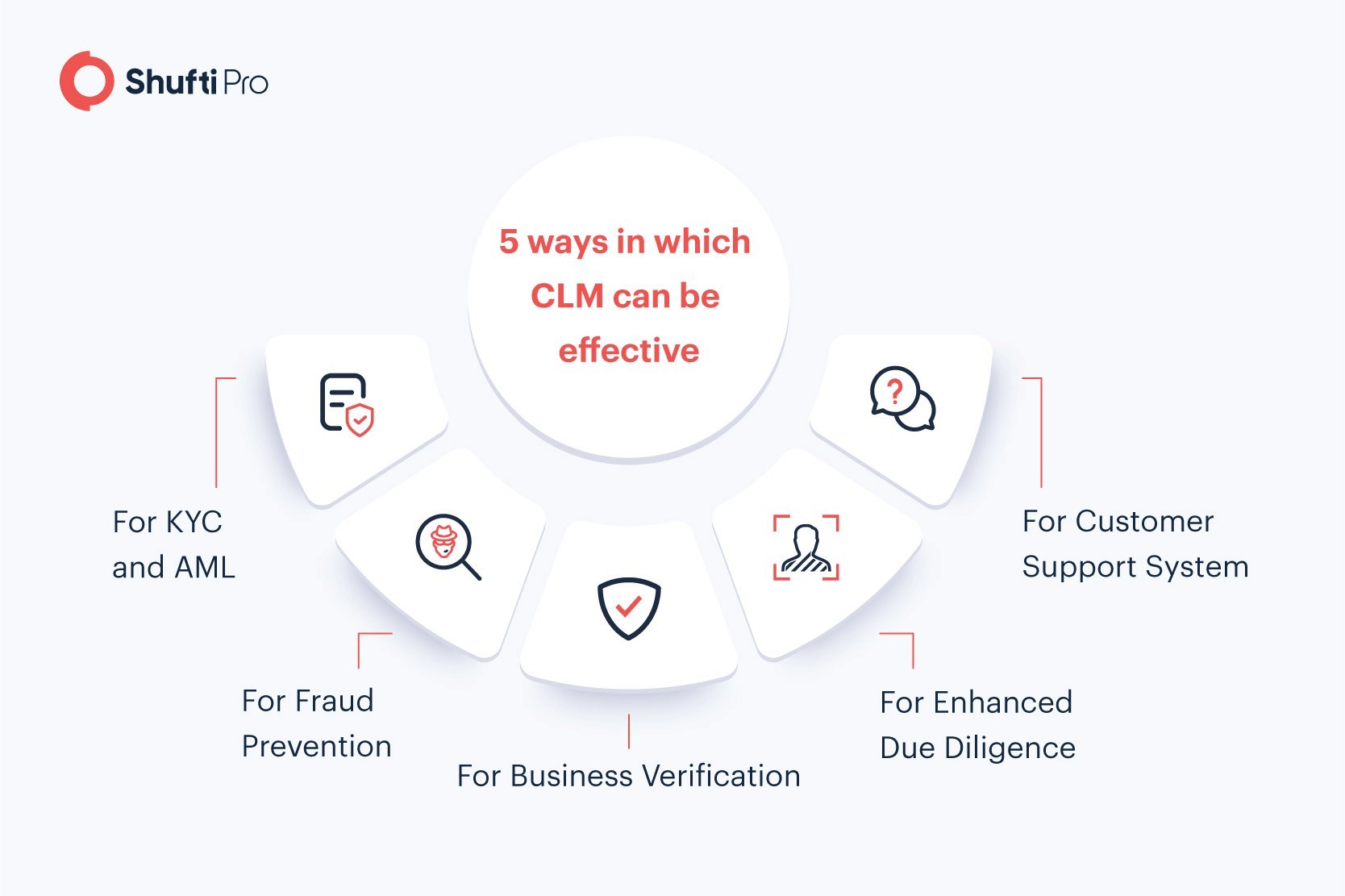
Downsides of a Poor CLM System
Since you now have an idea about designing the perfect CLM system, let’s take a look at what will happen if your system lacks at any point or stage.
Higher Costs and Lower Revenues
The cost of reaching out to potential customers and then acquiring them will only increase. Why? Because the decentralised system you depend upon will take a handsome chunk of investment and you may not be able to justify them at the end of the year. Moreover, the errors during customer onboarding, identity verification, ongoing KYC, and mapping the customer journey can contribute to more financial losses. On the brighter side, a fully automated CLM system that incorporates AI and ML models can streamline and decentralise the entire process. Ultimately, there is no room left for errors and high operational costs.
Decreased Customer Satisfaction
Why would any business want to spoil their customers’ experience? But do you know that a company might lose 74% of potential customers just at the onboarding stage because the process was inconvenient? Surprisingly, this is the second stage of the customer lifecycle and errors or prolong processes can end up in lower customer satisfaction. However, the system built on the aforementioned steps is meant to enhance the customer experience.
Ineffective Regulatory Compliance
Regulations are the biggest concern of all enterprises nowadays. Every stage of the CLM system must incorporate certain identity verification and customer due diligence checks for effective compliance with the laws. Unfortunately, conventional methods of ID verification and customer onboarding are no longer helpful. Despite the availability of digital identity verification systems, businesses still depend upon manual methods that lead to the inability to abide by the laws. On the contrary, AI-driven systems can cut loose ends and help the corporate sector in complying with the laws effectively.
To Sum Up…
Customer lifecycle management (CLM) is a never-ending process. From reaching out to saying goodbye, the procedure is comprehensive. A firm cannot give up on the system but it can adopt the six simple steps to make it as effective as possible. Refine goals, plan, search, digitise, verify, and remediate continuously to achieve the perfect CLM system. Otherwise, get ready to lose customers, experience declining sales and probes for law violation, and invest more in client acquisition and retention.
Want to know more about the role of identity verification in client lifecycle management? Feel free to reach out to us.











