Identity Verification Services — Fueling the Demand for Safe Gaming Experience

Modern gaming is the most recent evolution of online games that has enchanted gamers across the globe. However, new products, payment options, and emerging technologies have made the business more vulnerable to criminal activities than ever before. Remote gaming’s recent rise, fueled by the COVID-19 epidemic over the last year, has increased financial crimes associated with the gaming business. thus, also gaining authorities’ attention regarding anti-financial crime regulations and social responsibility code.
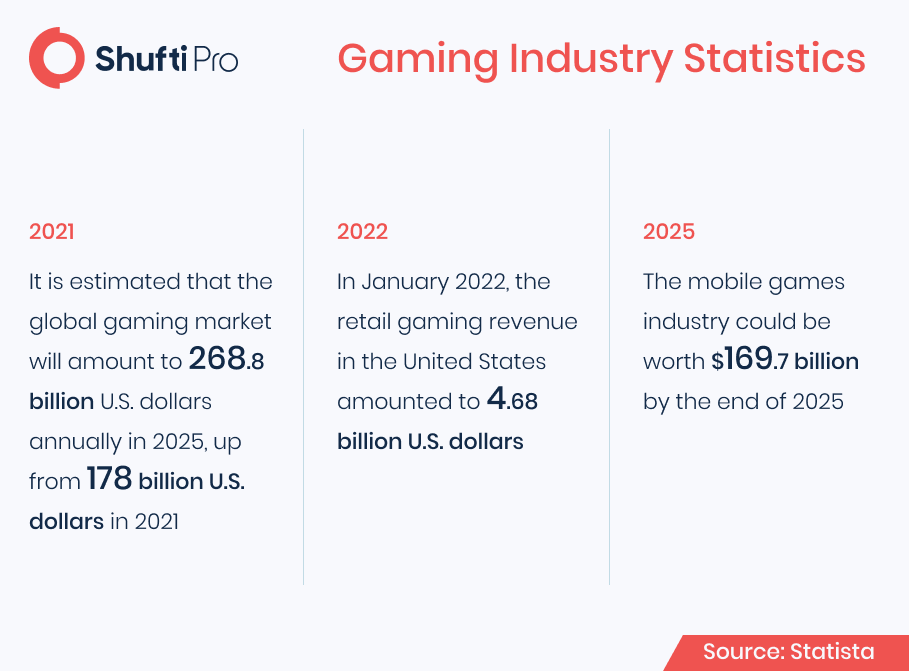
However, recent developments demonstrate how appealing the gaming community has become to crimes including money laundering. Thus, crimes carried out via video games are almost as old as the industry itself. While unlicensed copies and pirated versions of games were once the most common type of illicit gaming activity, recent advances and trends in online gaming platforms have opened up new opportunities for cybercriminals to defraud an industry worth almost $100 billion. What’s more concerning is that publishers aren’t the only ones who are being targeted; players are also becoming victims of this new type of criminality.
The State of Play – Financial Crimes and Digital Gaming Industry
Emerging innovations and the use of sophisticated technologies illustrate how the gaming industry has become a victim of cybercriminals, as well as how rich the game-hacking sector has become, emphasizing the need for game creators, gaming service providers, regulatory authorities, and players to take game security more seriously.
The key factor that makes money laundering and other complex crimes through online games possible like virtual onboarding, in-game items that sometimes have a real-life value outside the game. This includes artifacts that add additional powers to the player’s character (such as swords, armor, and magic potions) or ‘currency’ that can be used to purchase them.
In addition to this, some games allow players to buy and sell in-game products using government-issued fiat currency or with cryptocurrencies. This is known as microtransactions, and it is especially common in games that are free to play but have paid in-game products. For example, Second Life and Entropia Universe have official storefronts that allow in-game purchases. Furthermore, an increasing number of games use gambling-style microtransactions by selling ‘loot boxes,’ which are a collection of randomly-picked in-game artifacts whose contents are only revealed to the consumer after purchase.
There are no clear expectations of what game operators can or should do to uncover criminal behavior because online games are not heavily regulated in various jurisdictions. Some may be enticed to convert unlawful income into in-game products since they can be utilized to store value. Sixgill, a cyber security organization, published research on money laundering via V-bucks which is an in-game currency utilized in the online game “Fortnite”. According to Sixgill, money launderers were buying V-bucks from the official Fortnite store with stolen credit/debit card information and then selling them at a discount to other gamers on the dark web or on social media sites.
Similarly, another financial crimes report also stated that cyber-criminal groups had automated the use of stolen card details to create a large number of fake Apple IDs, in order to purchase in-game items in mobile games like Clash of Clans or Marvel Contest of Champions, and resold them for fiat currency on third-party websites.
In essence, purchasing in-game products with stolen card information is no different than purchasing any actual or intangible goods online with stolen card information. The payment processing company bears the major obligation for spotting this illicit behavior. However, the gaming firm may have important information about the criminal’s in-game behaviors, such as interactions with other players, which could lead to their exposure to criminal networks.
BSP Warns Play-to-Earn Gamers about Potential Illicit Activities
The Central Bank of the Philippines (BoP) has published a public warning regarding the increasing number of financial crimes involved in the gaming industry. particularly, play-to-earn digital games, even financial firms have flagged such kinds of online gaming businesses as a potential risk that is helping criminals to carry out money laundering and other crimes.
“The Bangko Sentral ng Pilipinas (BSP) advises those engaging in these games to be thoroughly aware of how these work, as the digital space provides a borderless and wider playing field for fraudsters or cybercriminals to carry out illicit financial activities,” the bank stated. In addition to this, the central bank has also highlighted that such platforms including Axie Infinity have gained popularity among the locals, although it has not yet complied with the regulatory obligation. “Digital gaming token transactions have a high degree of anonymity and are not subject to Know Your Customer policies,” it said.
Regulation
The online gaming industry is badly impacted due to the increasing number of financial crimes, including money laundering and terrorist financing. Due to this reason, this industry has become subject to regulatory obligation as a never-ending wave of standards and precautionary measures are lined up, aimed to secure the gaming industry.
In addition to this, The gaming company’s stance is comparable to that of a virtual currency exchange if a computer game allows players to send in-game items to each other and these in-game items can be swapped for fiat currency. Virtual currency exchanges, unlike gaming enterprises, should be subject to anti-money laundering/counter-terrorist financing (AML/CTF) legislation, according to the October 2018 modification of the Financial Action Task Force (FATF) Recommendations, the global AML/CTF standard-setter. Regulated enterprises must identify their customers, monitor their conduct, and report any suspicions of illegality to authorities under these guidelines.
Final Thoughts
Reducing the risk of financial crimes in the digital gaming industry is in the best interest of the players. Criminal activities not only impact businesses’ repute but also adversely affect the annual revenue. However, emerging technologies like Artificial Intelligence (AI) integrated into identity verification and AML screening systems promise to determine identity theft, money laundering, and other criminal activities. Online gaming platforms by incorporating AI-driven solutions can analyze the gamer’s usage pattern, flag cheaters, and prevent bad actors from creating fake accounts for their illicit plans. Thus, the only way of eliminating the risk of cheating is through Identity verification solutions.
Shufti’s state-of-the-art ID verification service can be an ideal solution to outlaw the cheating problems in online gaming. The system is powered by thousands of AI algorithms that can render 98.67% accurate and real-time verification results in less than a second, hence it is a perfect fit for the fast-moving e-gaming industry.
Want to know more about AML/KYC services for the gaming industry?

 Explore Now
Explore Now













