Know Your Donor (KYD) for NPOs – Red Flags that Charities Need to Consider

Like every other sector, non-profit organizations and charities are also vulnerable to financial criminals. Charity fraud is prevalent due to several unavoidable reasons like the large amounts of cash transfers making it difficult to monitor suspicious activity, as well as the trust of the employees involved.
However, there are also some avoidable reasons such as the complete lack of monitoring/auditing systems at certain organizations. Due to the Covid-19 pandemic, charities and non-profit organizations increasingly suffered from not only financial losses but a permanently stained reputation as well.
Types of Fraud in NPOs & Charities
Non-profit organizations are largely dependent on regular support from donors and public resources, which means reputational damages can cause them to shut down. The commonly reported frauds in charities in the past few years were unauthorized fundraising and credit card scams, which involve big donations along with terms and conditions from the donor’s side. Charity frauds are further sub-categorized as internal and external frauds. The most common internal frauds in charities are the misuse of charity funds and false expenses claims.
Unauthorized Fundraising
This kind of charity scam targets the sympathy and good faith of donors by persuading them to make a big donation for a given cause. In most situations, the fraudsters’ request is seemingly linked to an event like a flood or earthquake relief fundraiser. However, the money actually goes right into the criminals’ pockets.
There are several ways through which money is stolen by using unauthorized fundraising as a trap, including email requests to pay by card, or dropping the money in a collection box. Addressing the issue of unauthorized fundraising, the Charity Commission urges all trusts and charity organizations to incorporate necessary steps, including legal actions, to prevent donations from going into the wrong hands.
Credit Card Scams
Another type of charity scam was identified by the Charity Commission where credit cards were used by fraudsters to trick charities. Criminals supposedly try to donate a large sum of money to a particular charity but involve a condition that the charity should send half (or more) of the amount to their other desired charity.
The bank account details provided by the criminals are of their personal accounts. However, fake donations are made using stolen credit cards. In light of credit card scams, authorities have warned charities to be wary of uncommon large amounts of donations and unexpected terms and conditions from the donor’s side.
False Invoicing
In a type of external charity fraud, fraudsters try to rake in money from the charity itself. False invoicing involves fake bills with forged supplier identities and purchase orders, which are used to manipulate the company into paying for services and supplies that have not been delivered. This type of fraud targets and is prevalent in charities of all scales.
In most of the cases, the charities are tricked into paying the amount of the false invoices because the company staff thinks they would have already delivered the services or supplies. In order to prevent becoming victims of false invoicing, charities and fundraisers should make all invoices go through a verification system where they are cross-checked to see whether the listed supplies have been received. Also, the owner/supplier must also be contacted before the payment is made.
False invoicing can also be an internal charity scam where corrupt employees could set up and pay for fake invoices. The Charity Commission states that reports of this kind of scam have been steadily increasing.
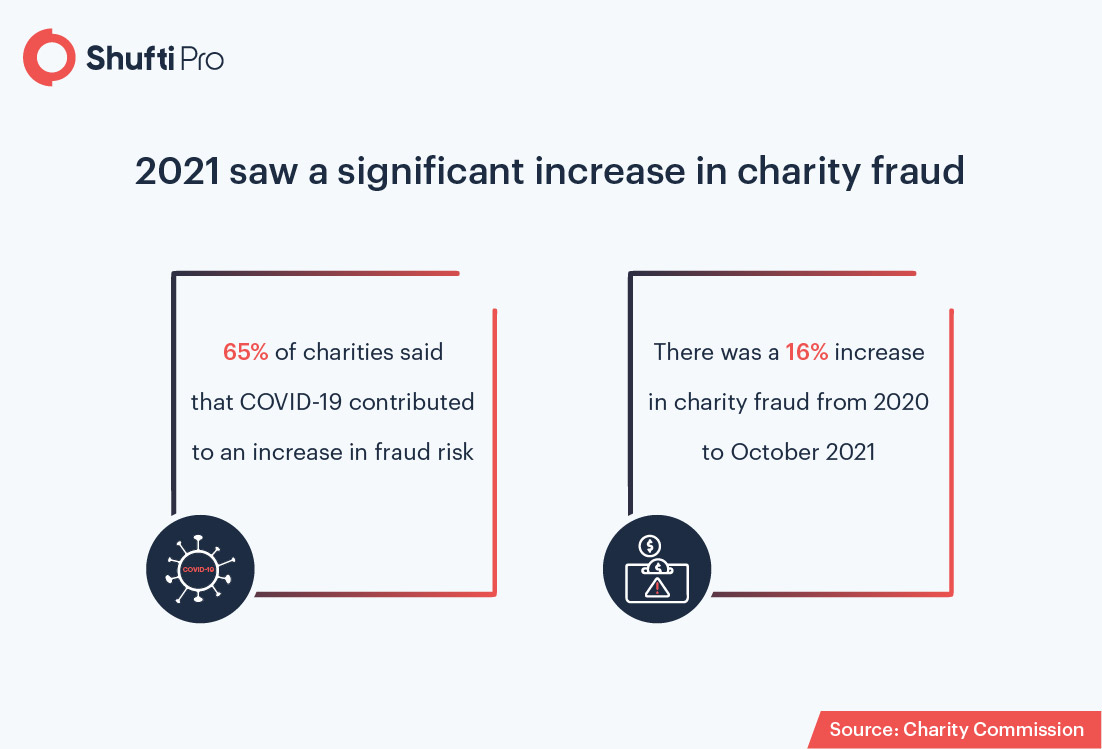
Fraud Losses in Charities By the Numbers
According to a report from the Association of Certified Fraud Examiners (ACFE), an organization loses more than $1.5 million on average to a single fraud case.
That’s not all, statistics from the Charity Commission show that around £8.6m of charity funds was lost due to fraud between 2020 and 2021. Another study by Action Fraud revealed a total of 1,059 fraud reports by charities during the same period.
However, the Charity Commission believes that the real number of such incidents was much bigger. Around 65% of charities have said that the Covid pandemic has led to a rise in fraud risks. Many of the charities have also shown concerns regarding the risks arising from remote work and virtual methods.
While non-profit organizations faced smaller overall losses than commercial enterprises, an average loss of $100,000 was recorded. This is a staggering 11 percent increase as compared to the previous numbers and a big loss for any given charitable organization. Apart from these immediate monetary losses, charities and non-profit organizations also face reputational damages.

Risk Assessment of NPOs by Financial Institutions
Financial institutions have the responsibility to analyze and reduce the risks in charities and non-profit organizations to eliminate financial crimes like money laundering and terrorist financing. To assist financial institutions in doing so, federal agencies recently issued the Joint Fact Sheet on Bank Secrecy Act Due Diligence Requirements for Charities and Non-Profit Organizations with guidelines to implement a risk-based approach in charities and non-profit organizations.
The paper was issued in November by the Board of Governors of
the Federal Reserve System, Federal Deposit Insurance Corporation (FDIC), Financial Crimes Enforcement Network (FinCEN), National Credit Union Administration (NCUA), and Office of the Comptroller of the Currency (OCC). The guidelines enlisted in the fact sheet are consistent with the customer due diligence requirements that are included in FinCEN’s 2016 CDD Final Rule.
Since non-governmental organizations (NGOs) can contribute to the funds for charities, the paper also mentions rules for inflow and outflow from and to NGOs. The complex process makes NGOs vulnerable to money launderers and terrorist financiers. Although all of the NPOs were not identified to have a high risk of money laundering and terrorist financing, regulators urge financial institutions to be prepared for uncertain situations in case of a possible influx in the number of NPOs.
What Shufti Offers
Considering the prevalent frauds in non-profit organizations, the need for verification and fraud preventions solutions is increasing. Implementing Know Your Customer (KYC) checks in non-profit organizations can help in reducing the losses due to fraudulent activities.
Shufti’s robust Know Your Donor solution is the ideal solution for non-profit organizations that find it hard to comply with regulatory obligations along with securing them from sanctions and financial losses. The AI-powered ID verification solution allows businesses to identify and verify the real identities of customers in less than a second with 98.67% accuracy.
Want to learn more about fraud prevention solutions for your charity organization?

 Explore Now
Explore Now













