Online Payment Fraud and the Role of AML Transaction Monitoring

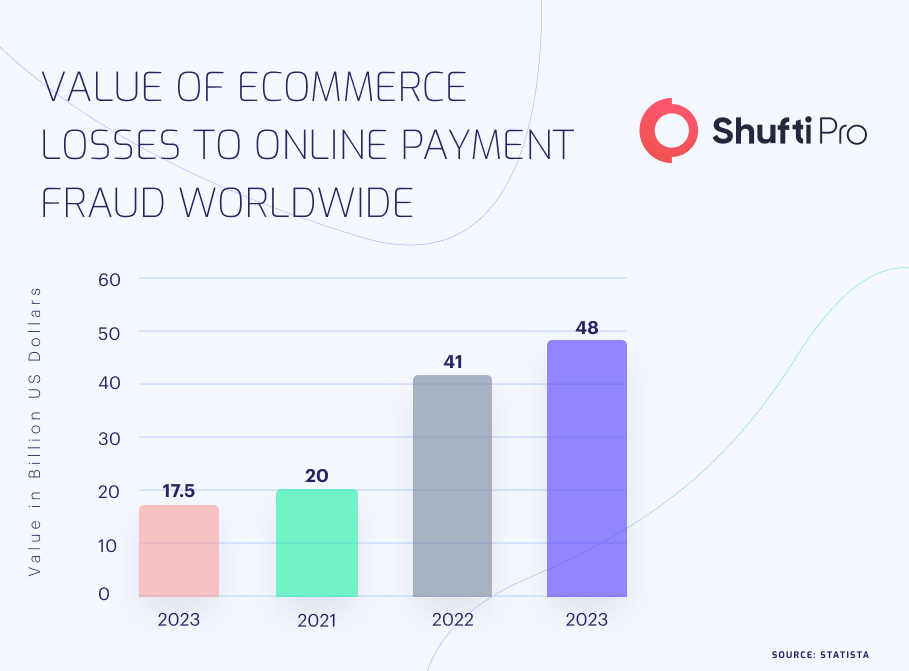
Imposing travel restrictions worldwide after the COVID-19 pandemic led to an unprecedented surge in eCommerce activity. This paved the way for increased online scams, and these effects were felt globally. Scams have affected each region differently, with Latin America reporting the highest loss (4.6%) and North America reporting the lowest loss of revenue (2.4%) in the same year. eCommerce lost $41 billion to digital payment fraud globally in 2022, highlighting how important it is to deploy robust Anti-Money Laundering (AML) transaction solutions.
Online Payment Fraud to Watch out for
1. Stolen Cards
Stealing an individual’s ID card, credit or debit card is considered identity theft. Identity theft is stealing someone’s sensitive data, including their name, credit card number, social security number, etc., to buy products or services.
Scammers obtain anyone’s personal details through various methods, such as:
- Phishing: Scammers use texts or emails to trick individuals into providing confidential details by clicking on a link that instals malware on their devices.
- Hacking: Sometimes scammers hack the business’s computer systems to get all the personal data.
- Social Engineering: Criminals win someone’s trust and trick them into providing personal details in person or over the phone.
- Card Skimming: Imposters put small devices on card readers that steal an individual’s data when the card is swiped.
- Searching through Trash: Scammers even search a target’s recycling bins to obtain personal data illegally to fulfil their illicit intentions.
Such scams are not only wreaking havoc on customers but on merchants too. Firstly, they have to pay a refund and chargeback costs. In addition to this, they may also face severe fines in case their chargeback ratio exceeds the card scheme threshold for consecutive months. Not only this, but merchants also suffer reputational damage in case the customers hold them for not safeguarding their confidential data. Such scams could lead to fines and lawsuits for not complying with Know Your Customer (KYC) and AML regulations.
2. Chargeback Fraud
A chargeback scam or ‘friendly fraud’ is when a customer asks for the credit card charge, necessitating the reversal of the charge and refunding the client. As chargebacks are usually initiated by customers making legitimate claims, they are challenging to identify and prevent, and it is hard to prove the illicit intentions of criminals.
To be successful in this scam, customers falsely claim that:
- They have yet to authorise a transaction to get a refund and avoid paying for the services, goods, or services they received.
- They have yet to receive the services or goods that they ordered, although they did.
- The services or goods they received differed from those mentioned or had defects.
Chargebacks cost merchants much, as they may result in chargeback fees, lost revenue, and higher processing costs.
3. Card Testing
Card testing is a kind of credit card scam where criminals use automated software to check the validity of their stolen card numbers. They do this by conducting a significant number of transactions, every for a small amount, to test card numbers that are valid and which are not. With every successful transaction, the scammer becomes aware of how legitimate the credit card details they possess. This enables them to make more purchases using credit cards or even sell the obtained information on unauthorised online platforms.
Such small transactions are not flagged as fraudulent, making card testing scams remain unnoticed for long. This wreaks havoc on merchants if they do not have robust procedures to mitigate the fraud risk that could cost them chargebacks and fines.
4. Marketplace Fraud
Marketplace scams include wide-ranging frauds on an online marketplace, like eBay, Amazon, or Facebook. Different types of marketplace fraud are:
- Listing counterfeit or fake versions of some popular products, like electronic devices or designer dresses, usually made using low-quality materials and have a small shelf life.
- Sellers list items not in stock and disappear once they receive the payment.
- Scammers create fake seller accounts and use them to list overpriced or fake items.
Marketplace fraud causes big problems for eCommerce platforms if a client complains and the seller has disappeared, the funds can not be recovered. The particular marketplace is held accountable for refunding customers the requested amount.
5. Refunds to an Alternative Payment Method
In alternative refunds, a scammer deliberately pays more than asked for an item or service. They then request a partial refund via an alternative method like a wire transfer, gift card, or check, claiming to the seller that they accidentally entered the wrong amount. Scammers use different tactics to convince the seller to send the refund in their preferred form. For instance, they sometimes claim that the payment method is invalid or that they can not receive a refund in the same account or card. Once the scammers get the refund, they disappear and leave the seller to bear the loss of the disputed amount and the one sent through the alternative method.
AML Transaction Monitoring to the Rescue
eCommerce is becoming a hotspot for fraudulent activities lately. Scammers are trying to steal customers’ personal data for their illicit purposes. This is where the AML transaction monitoring solution comes in, mitigating the risk of different types of fraud in the online marketplace and enhancing security. Not only does it help keep criminals away, but it also helps online platforms abide by regulations and avoid hefty fines. Thus, investing in a robust transaction screening solution is the best decision, especially in this fraud-hit era.
How Can Shufti Help?
Shufti offers an AML transaction monitoring solution, protecting online marketplaces from different types of payment fraud by verifying identities within seconds. We are a globally trusted IDV solution provider, preventing chargebacks and recovering lost revenue. With a perfect balance of security and speed, you can automate customer onboarding processes and save time and energy. We screen customers against 1700+ watchlists, ensuring compliance with regulations and protecting firms from heavy financial penalties.
Still confused about how AML transaction solutions prevent payment fraud in this age of digitisation?











