Securing Transactions and Operations with Biometric Consent Verification in Digital Banking

- 01 What is Biometric Consent Verification?
- 02 How is Biometric Consent Verification Used in Digital Banking?
- 03 How Biometric Consent Verification Works?
- 04 Comparison of Biometric Consent Verification and Traditional Payment Methods
- 05 Use Case for Biometric Consent
- 06 Biometrics + I Agree = Consent Verification with Shufti
In the modern digital world, secure business operations are crucial. The focus on maintaining security has become more prevalent, given the sharp rise in digital transaction volume. Although they offer safeguard operations, traditional authentication techniques like passwords and PINs are susceptible to phishing and hacker attacks.
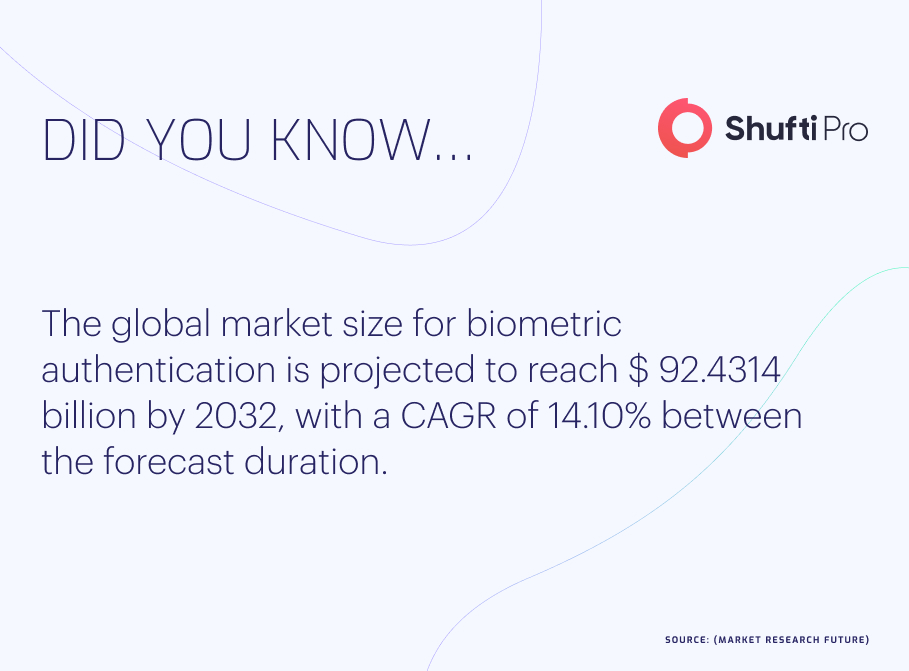
Conversely, biometrics offer a more dependable and secure means of authentication. The process of authenticating a person’s identity through distinctive features, including voice, face, and fingerprint recognition, is known as biometric authentication. With biometric authentication, the user’s identity is instantly validated, negating the need to remember a password or PIN. Biometric technology was valued at $28 billion in 2022 and will exceed $70 billion by 2027.
A recent strategy to combat the growing number of identity theft attempts that aim to fool standard identity verification techniques is biometric consent authentication. Due to the more thorough process and numerous additional verification techniques included, it is harder for online identity fraudsters to circumvent. The biometric consent verification service addresses every problem of a standard verification system.
What is Biometric Consent Verification?
The phrase combines two distinct verification services provided by KYC. One type of biometric verification is available only for onsite verification and is primarily provided as facial verification. It is also occasionally provided as an iris or fingerprint scan. Consent verification is essentially a written agreement given by a user to a business so that their credentials can be checked.
Thus, a biometric consent verification will encompass multiple facets of an individual’s identity. It will verify the user’s physical presence at the moment of verification, and they will have to present a personalised document or a handwritten note. Therefore, a mix of document and facial verification will be used.
How is Biometric Consent Verification Used in Digital Banking?
A few important applications of biometrics in banking are as follows:
Customer Onboarding
Verifying a new remote customer’s identification is the first and most important step. By ensuring that they are interacting with a real person right away, banks can support compliance efforts by early detection of potential false identities, bots, and bad actors. Banks are able to verify the identification of every new customer without ever having to see them in person by first scanning a trusted identity document, such as a driver’s licence, and then having them complete a quick biometric facial scan.
Due to the fact that businesses are unaware of the user’s danger until after they are enrolled, onboarding represents the point of greatest risk. To protect from threats like synthetic identity fraud, it’s crucial to start with the highest level of identity assurance possible. The onboarding process builds trust that lasts the duration of the client lifecycle.
Client Verification
A valid onboarding process may give way to fraudulent conduct such as phishing, identity theft, account takeover fraud, or other fraudulent activities. By using biometric consent authentication, businesses may be sure that the person attempting to access an account is the same person who created the account.
Returning authentication can be accomplished by a less complicated liveness check if the individual’s identification has been confirmed with the highest level of assurance; otherwise, a more rigorous procedure is needed unless newly discovered information increases the danger. A few examples of this are when a customer requests a password reset, adds a new authorised user to their account, sets up a new device, or rebinds an already-existing device. In certain situations, a bank can choose to strengthen authentication and demand a second biometric scan to be sure that this is the customer making the request for the adjustments. This makes it possible for banks to provide their clients with the necessary flexibility and convenience.
How Biometric Consent Verification Works?
Step 1: The end-user shows their face to the camera, holding a consent note of the client’s choice. There are two choices: a customised note or a predefined template. A unique consent message defined by the client (handwritten or printed note as per the client’s choice) is considered a customised note. However, any specific document selected by the client (company documents, employee card, etc.) is considered a pre-defined template
Step 2: the biometric consent checks for remote user presence and verifies the unique consent note, whether it is original or fake. During the process, it could be a pre-recorded video or any other spoofing that can be used to deceive the vendor. Once the consent note is raised, it is further checked for liveness detection, leaving no loopholes for threats and fraud.
Step 3: Definitive verification results are delivered, and the identity is confirmed for digital banking. The decision is made whether to verify and onboard or reject. If a user is rejected during the process, further precautionary measures are taken. Nonetheless, in either case, the proof is stored in the back office.
Comparison of Biometric Consent Verification and Traditional Payment Methods
Traditional techniques for securing payments include PINs, passwords, and signature verifications. These techniques are vulnerable to fraud, theft, and hacking, too. However, biometric identification makes it more difficult for fraudsters to access personal data by using distinctive bodily traits like voice, facial, and fingerprint recognition.
Biometric consent verification is not only more convenient but also more secure. Users of traditional payment methods might have to keep track of passwords or carry cards, which can be annoying and challenging to use. In contrast, biometric consent authentication only needs the user’s physical presence and a consent note.
Use Case for Biometric Consent
Biometric consent verification can help almost all organisations and industries that require a KYC verification solution. A mix of liveness detection, pattern recognition, artificial intelligence, and machine learning algorithms confirming facial verification, document verification, and customised text presented on a handwritten note can accomplish comprehensive identity verification in real-time.
In addition to being ideal for the one-time verification process during client registration, it is a reliable source for frequent access to a resource that would otherwise be limited. It can be used by banks to determine the type of transactions that clients are ordering them to do after a particular point. Retail customers may be requested by e-commerce websites to reveal their identity, along with a handwritten order confirmation with the order number and date. Goods delivery firms can also use biometric consent verification to verify addresses. By requiring claimants to display their personalised insurance files in front of their webcams along with their national identity cards, insurance claims can be processed quickly.
Biometrics + I Agree = Consent Verification with Shufti
Customers can be verified with a live selfie and a personalised handwritten or printed message. Simplified “I agree” checkboxes are insufficient to obtain users’ agreement in light of the rise in payment fraud and fraudulent chargebacks. They don’t offer enough proof to show who checked that box.
Integrate Shufti’s cutting-edge consent verification service to obtain your clients’ digital consent before moving forward. Shufti instantly validates and authenticates the user’s biometric identity and permission note using cutting-edge AI technology and anti-spoofing methods. Shufti expedites the verification process by screening consent notes in 15–60 seconds.
With Shufti, there is no minimum verification requirement. Every Shufti verification service, including the biometric consent verification service, is supported in more than 150 official languages and is accessible in over 230 countries. Not only are real-time verification results shown to end users, but they are also posted to the Shufti back office, where Shufti customers may check proof of verification and track how many verifications their clients have completed.
Need to secure transactions with biometric consent verification in digital banking.

 Explore Now
Explore Now













