Sim Swap Fraud: A new battle in the war of your Identity

In our connected world, we are using mobile devices for communication, work, banking, and entertainment. Phones help us manage the private files in our cloud storage accounts and organize our lives. By these devices, we manage our social media accounts. In short, our mobile devices hold every detail of our personal information. No matter the distance, the small chip in our devices known as SIM cards allow us to stay in touch with family and friends. But what if we lose our SIM cards? What if someone else hacked our SIMs? These are one of the many questions that are faced by SIM swap attack victims.

In this article, we’ll cover all the insights of a SIM swap fraud and we’ll discuss how to protect yourself from this type of scam.
What is SIM Swapping Scam?
SIM swapping or SIM jacking is a type of ATO (account takeover) fraud in which a malicious fraudster uses various techniques such as social engineering by which they transfer victim’s phone numbers to their own SIM card. The hackers can reset passwords or receive 2-Factor Authentication codes that can gain all the accounts which are linked to that SIM number. This type of attack can give fraudster access to everything your number is linked to which may include your social media accounts, email, and bank accounts.
How does it work?
A SIM swap scam occurs when scammers take advantage of a weakness in two-factor authentication and verification or exploit the system. So having control over your SIM would be valuable to fraudsters as he can have access to all of your personal data. Scammers start by gathering as personal information and engaging in a bit of social engineering to get hold of your number. The scammers call your mobile carrier, impersonating claiming that they have lost or damaged their (your) SIM card. They can then get a new SIM card activated in their possession with your number. So the fraudster is using a different SIM card with your number in his device. Fraudsters can then access your phone communications with banks and other organizations by using your data. They can change the passwords by receiving reset links and codes on their phone. And that’s it: They’re in. They can even create a new bank account with your name and carry their malicious activities like money laundering and terrorist financing under your name.
SIM Swap Hackers Targeting Crypto Investors- Some Examples:
On June 11, it came to light that California resident Richard Yuan Li had been charged to commit SIM swap attacks that targeted at least 20 individuals. With his elaborate money swindling scheme, he exhorted 100 Bitcoin (BTC) in exchange for keeping private and sensitive information of individuals from being released online.
There has been a dramatic spike in SIM swap attacks in the past few years. A crypto investor Michael Terpin fell victim to a $23.8 million SIM swap attack.
Similarly, investor Seth Shapiro filed a lawsuit against American telecom giant AT&T as one of their employees had masterminded a nefarious SIM swap scheme that resulted in him losing $1.8 million in various crypto assets.
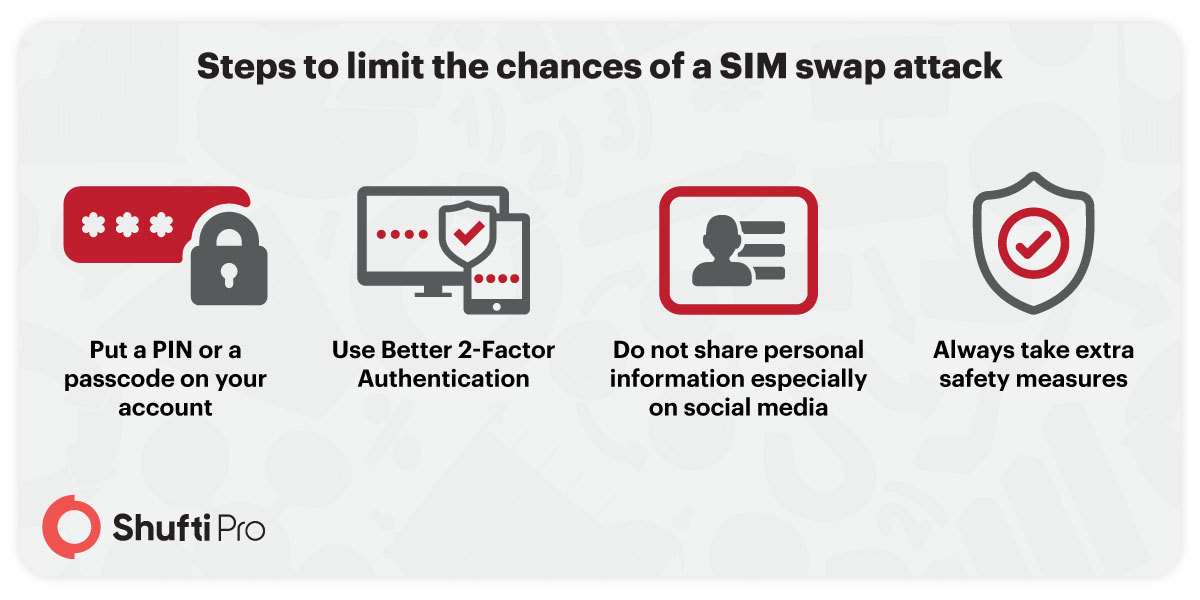
Sign to Know you are a victim of SIM swap fraud:
It can be a challenge to stay a step ahead of SIM swap scams. But there are always some warning signs so you can put a halt to fraudsters’ access as soon as you know those signs. Here are some of those signs:
- One warning sign, which is very common, is social media activity that isn’t yours. Any social status upload or tweet which you have not done alerts you to the breach.
- The other big sign is when your phone calls and texts aren’t going through. This may happen when the scammer deactivates your SIM and uses your phone number so you are unable to make calls or texts.
- If you get a notification that your SIM card has been activated on another device you’ll know you are a victim. So never ignore your notifications!
- If you lose access to your accounts and your login credentials no longer work, it’s most likely that they have been taken over through your number. In such a case, without losing a minute, contact your bank or other organization immediately.
SIM swapping due to poor ID verification process?
SIM swapping has become a significant threat for users as a large number of users are having their lifetime savings and invaluable data stolen from under their eyes. This is happening solely because mobile operators are seemingly failing to take reasonable steps to prevent these criminal hackers. They need to have proper identity verification checks so that they can restrain fraudsters from gaining access to anyone’s SIM.
SIM-swap-related incidents have increased sharply over the past few years because the telecommunication industry lacks identity verification checks and make customers vulnerable to a variety of different hack attempts.
Read Also: KYC for customer on-boarding in Telecommunications Industry

 Explore Now
Explore Now













