The Most Frequently Asked Questions About Perpetual KYC

Maintaining the accuracy of customer data presents a considerable challenge. Automating it has traditionally been expensive and difficult, leaving room for human errors. In the past, customer data updates were carried out periodically, typically every one, three, or five years. However, most resources were allocated to high-risk activities, neglecting routine maintenance and regular updates for a significant portion of the customer base.
The consequence of this approach is accumulating outdated information within businesses, including obsolete addresses, expired driver’s licences, and outdated contact details. This accumulation leads to both latent and immediate risks, such as the potential for hefty fines. Furthermore, obsolete KYC data fails to accurately reflect an individual’s current risk level or suitability for financial products. This is where the concept of Perpetual KYC (PKYC) emerges.
Let’s dive deep into the blog to learn more about PKYC.
FAQ 1: What is Perpetual KYC?
Perpetual KYC is a continuous Know Your Customer (KYC) procedure to verify and track customers’ identities and behaviours. KYC is a regulatory obligation imposed on organisations to combat illicit activities like money laundering, terrorist financing, and fraud. It is important to note that the specific implementation and requirements of perpetual KYC can vary based on the jurisdiction, industry, and regulatory frameworks governing the organisation.
FAQ 2: What is the Difference Between Traditional and Perpetual KYC?
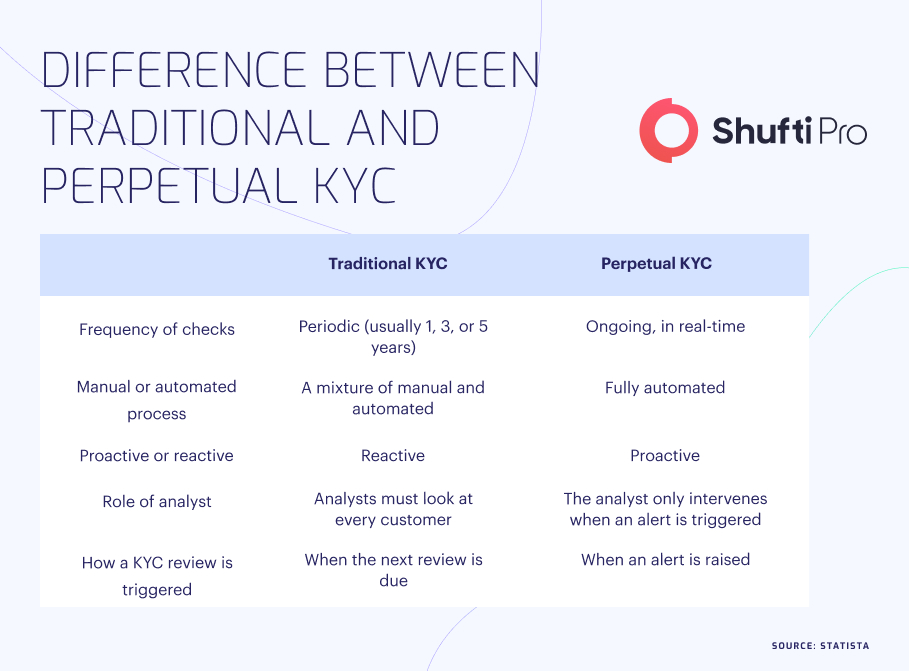
The key difference between traditional and perpetual KYC is their frequency and data update approach. Traditional KYC typically follows fixed cycles, such as one, three, or five years, for refreshing customer data. It often involves manual processes and periodic reviews of customer information. On the other hand, perpetual KYC adopts a continuous and automated approach, utilising real-time monitoring and automated systems to verify and update customer records constantly. Unlike traditional KYC, which can result in the accumulation of outdated data, perpetual KYC ensures that customer information remains accurate and up to date throughout the entire relationship with the business. PKYC is a proactive approach that minimises risks, enhances compliance, and enables businesses to make more informed decisions based on current customer data.
FAQ 3: What are the Challenges of PKYC?
PKYC also comes with its own set of challenges. Some of the key challenges associated with PKYC include:
- Data Privacy and Security: With continuous monitoring and updating of customer data, there is a need for robust data privacy and security measures. Approximately 15 million customer data records were exposed worldwide during Q3 of 2022. Safeguarding customer information from unauthorised access, data breaches, and cyber threats becomes crucial in PKYC implementation.
- Regulatory Compliance: Adhering to constantly changing regulatory requirements can be challenging. Businesses must stay updated with the evolving compliance landscape and ensure their PKYC processes align with relevant regulations and guidelines.
- Data Quality and Accuracy: Maintaining accurate and high-quality customer data is essential for effective PKYC. Data inconsistencies, errors, and gaps can impact the reliability and usefulness of PKYC processes. Businesses must establish data governance practices and invest in data validation techniques to mitigate these challenges.
- Integration and System Compatibility: Implementing PKYC requires integrating existing systems and databases. Ensuring compatibility and seamless data flow between different platforms and databases can be complex, requiring technical expertise and resources.
- Customer Experience and Consent Management: Balancing PKYC requirements with a seamless customer experience is crucial. Maintaining customer consent for ongoing data monitoring and updates can be challenging, requiring clear communication and transparency to build trust.
- Scalability and Resource Allocation: PKYC involves continuous monitoring and updating of customer records, which can be resource-intensive. Businesses must allocate sufficient resources and invest in scalable infrastructure to handle the increasing volume of data and processing requirements.
- System Reliability and Downtime: PKYC relies on automated systems and real-time data processing. Ensuring system reliability, minimising downtime, and having backup plans in place are important to maintain uninterrupted PKYC operations.
Whilst PKYC offers significant benefits, addressing these challenges requires careful planning, robust infrastructure, adherence to privacy regulations, and ongoing monitoring and improvement of processes.
FAQ 4: Is Perpetual KYC the Future of Compliance?
The future of compliance will likely embrace perpetual KYC as a valuable approach. Here’s why:
- Evolving Regulatory Landscape: As regulations evolve and become more stringent, businesses must adopt proactive measures to ensure compliance. Perpetual KYC provides a continuous monitoring and updating mechanism, allowing businesses to stay ahead of regulatory changes and maintain real-time compliance.
- Enhanced Risk Management: Perpetual KYC offers a proactive approach to risk management. Businesses can promptly identify and address potential risks by continuously verifying and updating customer data. This helps prevent fraudulent activities, money laundering, and other financial crimes, strengthening the overall security posture of the business.
- Customer-Centric Approach: The future of compliance is customer-centric, focusing on providing personalised experiences. Perpetual KYC enables businesses to have up-to-date customer information, facilitating tailored services, targeted marketing, and improved customer satisfaction.
- Technological Advancements: With advancements in automation, artificial intelligence, and data analytics, perpetual KYC becomes more feasible and efficient. Automated systems can handle the continuous verification and updating of customer records, reducing manual effort and improving operational efficiency.
- Cost Savings and Efficiency: Implementing perpetual KYC can save costs by eliminating the need for periodic large-scale data refreshes. With continuous updates, businesses can allocate resources more effectively, reduce manual errors, and streamline operational processes.
Whilst the adoption of perpetual KYC may vary across industries and jurisdictions, its benefits align with the future direction of compliance. Embracing this approach can help businesses navigate complex regulatory environments, manage risks effectively, and offer great customer experiences in the digital age.
How Can Shufti Help?
Shufti offers a real-time identity verification solution to help businesses achieve PKYC. Our AI-powered IDV solution assists firms in implementing perpetual KYC by ensuring accurate customer verification within seconds, continuous monitoring of risk profiles, and compliance with evolving regulatory requirements.
Still confused about how PKYC helps your businesses in managing risk effectively?

 Explore Now
Explore Now













