Understanding eKYC | The Benefits, Processes & 2024 Forecast

Governments worldwide require firms, such as financial institutions, to know who their customers are and who they’re associated with. The identification procedures, often known as Know Your Customer (KYC) or customer due diligence (CDD), are intended to detect and prevent money laundering as well as other financial crimes.
The term eKYC electronic Know Your Customer originated from the shift of certain important procedures in sectors that require more severe controls than typical to authenticate the identity of their consumers and end-users. Although eKYC has only become popular in recent years, the term widely recognised as Know Your Customer KYC process that professionals in the relevant fields have used for much longer.
Learn more about eKYC, its importance, and the benefits it brings to businesses as well as individuals. Understand the eKYC signal process and countries implementing it, as well as differentiate manual KYC from eKYC, along with the top prediction for 2024 and businesses’ way to go for digital KYC.
What is eKYC?
Electronic KYC verification is an automated means of validating identity and other KYC requirements. The method will differ depending on the industry, corporate requirements, and client preferences. However, it mainly refers to the use of e-forms, electronic records, and various levels of automation. eKYC, like traditional KYC process, is often performed during the start of the account creation process and is then maintained regularly.
eKYC vs KYC
Traditionally, KYC had to take place at a physical location. This meant that to open an account; businesses would generally demand a consumer to present paperwork and documents for verification. eKYC is basically a digitised version of KYC in which consumers fill out forms and provide documents as well as other information digitally via apps or web portals.
The collection and verification of customer or client information is where KYC and electronic KYC differ. Whilst KYC may require offline procedures such as obtaining and verifying physical documents, eKYC accomplishes the same goals through digital technology. Compliance risk assessment can be done via eKYC without either meeting in person or exchanging physical documents. It is the next evolutionary stage in a crucial process that safeguards businesses as well as society from fraud, scams, terrorism, and other criminal conduct.
Why is eKYC Important?
Because of the increased demand for digitised products and services, businesses are focusing on expanding into markets beyond their geographical borders. Scalability is one of the primary medium-term goals of organisations, allowing them to leverage their value offer and the capabilities of digital technologies to function easily anywhere worldwide.
In this view, eKYC, which responds to criteria adopted in the majority of states, can allow enterprises to include users and consumers in any state with full legal safeguards if appropriately done and tailored to each market.
Productivity and efficiency, however, are critical for any organisation. The eKYC increases ratios to previously impossible levels by utilising error-free systems that allow staff to focus on more vital duties whilst ignoring bureaucracy.
Which Countries have Implemented eKYC?
Many nations throughout the world have given banking institutions the authority to undertake KYC procedures electronically. Nonetheless, Estonia and India are frequently regarded as at the forefront of the eKYC transformation.
Since 2001, Estonia’s national ID card has featured electronic features, making the country an example for many other countries seeking to adopt e-IDs. Citizens utilise these e-IDs to access hundreds of government facilities as well as for commercial interests.
In contrast, India’s Aadhaar system combines a 12-digit number (akin to an SSN) with unique signals such as a person’s photograph, fingerprint, and iris scan. This information is kept in a centralised database and is accessible when a person’s identity has to be verified for government-related purposes. Other than Estonia and India, many other countries are adopting and implementing eKYC, including, but not limited to:

The Benefits of eKYC
eKYC has various benefits, mainly because it may leverage automation more than traditional identity verification methods.
The Benefits of eKYC for Customers
Convenience
Individuals and businesses can fill out forms and apps without scanning real papers, printing paperwork, visiting physical branches, and standing in line waiting for their turn.
Rapid Approval Process
Customers benefit from speedier account opening approvals because of the automated electronic data review.
Enhanced Privacy
Using eKYC often results in fewer human beings examining sensitive data since the system processes it automatically. Customers will benefit from increased privacy overall.
The Benefits of eKYC for Businesses
Enhanced Processing Speed
Identity verification can be accomplished in seconds after submitting customer information, which is substantially faster than a traditional review. This speeds up the process, lowering drop-offs and increasing conversion rates.
Reduced Workload
With low reliance on traditional inspection, financial organisations require less staff committed to KYC, allowing resources to be reallocated to other areas.
Scalability
eKYC systems enhance corporate growth and flexibility by reducing the requirement for hiring and educating manual reviewers. Additionally, the accessibility of electronic KYC services 24 hours a day, seven days a week, ensures that business operations continue beyond typical working hours.
Reduced Human Errors
Reducing human involvement reduces the likelihood of inaccuracies, resulting in better operations.
The Stages of eKYC
Biometric identification is the most reliable and fastest technique of verifying identity in any industry or sector, and it works in the following manner:
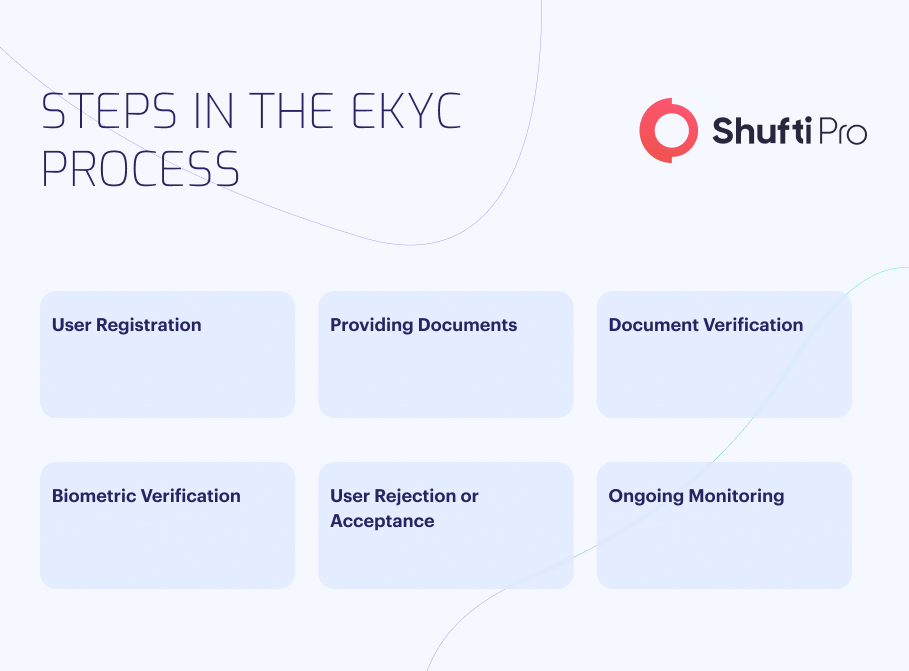
- The user enters information into the platform.
- Scan the ID card, and AI extracts data from documents, verifying its reliability and accuracy.
- As proof, the user is required to present their face and execute the commanded action for live detection.
- To identify the consumer, the automated system pulls identifiable patterns from them, creates a user in the system, and compares the data to that included in the identity documents provided.
- The system creates credentials that grant the user access to the system as well as the goods and services that are contracted afterward using facial biometric identification.
- When the procedure is finished, and the user is onboarded, the data is saved and continually monitored in the future.
Examining the user experience and interface in which these steps in the eKYC process will take place is critical. Only the most refined eKYC online identity verification systems can avoid mid-process dropout and ensure excellent outcomes.
Different Signals to Use When Performing eKYC
eKYC can help businesses gain a better understanding of their consumers’ identities. This is because eKYC can use a greater variety of information and indicators than standard KYC procedures. Traditional KYC is based on proactive signals like Personally Identifiable Information (PII) the user provides and data from third parties like sanctions or watchlists. eKYC, on the other hand, combines these with passive signs and cognitive signals that are difficult to detect manually by evaluating human forms and papers.
Active Signals
Active signals include data provided explicitly by the individual, such as:
- Name
- Residence
- Birthdate
- Social Security number (SSN or any other identification number)
Furthermore, active signals include documents and images uploaded, such as government-issued identification cards, financial records, photos, etc. Along with the shift to eKYC governments such as India, Pakistan, and Estonia have implemented electronic identification forms that serve the same objective as traditional IDs. Although the notion of eID has yet to receive general adoption at the national level in the US and the UK.
Third-Party Data
Third-party information refers to signals that are collected from sources other than the people, such as government agencies, business entities, data libraries, and authorised databases. These datasets come in different forms, including:
- Federal government watchlists
- Phone risk reports
- Lists of sanctions
- Adverse media reports
- Politically Exposed Persons (PEP) lists
- Email risk reports
Third-party data is often acquired in the background throughout the process of opening an account, allowing businesses to improve their understanding of clients without adding further barriers to the KYC process. Additionally, many businesses cross-reference client profiles with these data sources regularly to verify that the person’s position remains constant.
Passive Signals
Passive signals, also known as device signals, are generated by the device people use to complete the KYC procedure. Typically, these indicators are acquired in the shadows without anyone’s knowledge. They include a variety of data points, such as:
- IP address or location information
- Software fingerprint
- Browser identifier
- Metadata
- VPN information
Passive signals are important in eKYC because they allow digital verification and contrasting details provided voluntarily by an individual with information silently transmitted through the device. For example, if someone claims to be in Berkeley, but their IP address shows they are now in Miami, additional inquiry may be required to determine their legitimacy.
Behavioural Signals
When interacting with web-based interfaces or programmes, individuals’ activities generate behavioural indications. Individuals are generally ignorant that their behavioural indicators may be monitored, examined, and analysed. Among the behavioural indicators are:
- Recognising hesitations
- Identification of disengagement
- Cursor clicks and keypad strokes
- Application of developer tools
- Copy-cut-and-paste operations
- Using autofill functionality
Behavioural signals can be used for a variety of purposes, such as identifying between legitimate individuals and artificially intelligent bots when filling out a form. Additionally, it can aid in detecting probable identity theft situations, such as if an application is filled out mysteriously or by a real person. As a result, behavioural signals, like passive indications, are essential in the realm of eKYC.
Top 5 Predictions for eKYC for 2024
Automation Take Over to Manual KYC Processes
Advanced technology like artificial intelligence and machine learning remain poised to gain progress in replacing manual, difficult, and repetitive KYC processes that would otherwise cost a significant amount of energy and time. Fintechs, financial institutions, cryptocurrency exchanges, and IT safety service providers are all starting to use AI-based Customer Due Diligence (CDD) solutions. Nonetheless, the main concern remains how AI or any other technology determines the legitimacy of a document; it checks the following information in a streamlined manner:
- The size of the font
- The distance between phrases and words
- Recognising altered pictures
- Examining the document’s expiration date
- Identifying photoshopped papers
- Detecting forged unique identification numbers
- Deepfake detection
Advanced technology and machine learning will continue to assist businesses in detecting and combating fraudulent activities. The automation and related technologies market is developing at a 20% annual pace and is expected to reach $5 billion USD by 2024.
Ongoing eKYC to Become a Part of AML Compliance
Some people and businesses will always be more vulnerable than others. In this instance, a one-time KYC for onboarding high-risk businesses may not be sufficient, so continuing KYC will become an essential component of risk mitigation. High-risk customers, such as PEPs (Politically Exposed Persons), must be examined annually instead of three or five years for low-risk customers. As opposed to relying on continuous traditional KYC, the automated technique shows potential red flags connected with questionable activity, such as:
- The unusually high volume of transactions
- Change in ownership of a firm
- Dealing with high-risk countries and corporations
Suspicious behaviours will assist corporations in determining the continuous risks connected with interacting with high-risk enterprises and entities.
Real-time risk profiling using AI and IoT
The Internet of Things, or IoT, is a network of interlinked physical devices equipped with software and sensor technology that allow data to be shared with other devices. Whilst it is still in its early stages, it will eventually form the cornerstone for all we do digitally.
The IoT market is only getting started, with a CAGR of 25%. When advanced technology like machine learning or artificial intelligence is used, eKYC will be taken to an entirely different level. IoT will be used by financial institutions, fintechs, and other businesses to save time, effort, and money in establishing digital client identities and tracking money-related activities in real-time. It will also aid companies in risk assessment and profiling to reduce fraudulent activity.
Additional UBO Information Requirement
The Corporate Transparency Act of 2021 with Final Updates makes one thing clear: American corporations must identify their beneficial owners as soon as possible. As a result of recent regulatory developments, ID verification and data about ownership will now be necessary.
Unidentified ultimate business owners (UBOs), on the other hand, continue to be a significant component of the KYC problem. Frequently, insufficient information on firm ownership creates a barrier to efficient KYC operations.
Some countries, such as Luxembourg or Panama, are notorious tax havens and might require longer to adapt to new regulations. Nonetheless, regulator bodies and governments will exchange owner-beneficiary data soon to reinforce and comply with KYC requirements.
More Data Sharing
Lastly, sharing information with legislative and judicial organisations will only increase soon. Many nations worldwide have made it necessary for enterprises to provide information about the organisations and individuals with whom they do business. All of this takes place in an attempt to reduce fraud and prevent heavy penalties for money laundering and terrorist financing. As AI improves the efficiency of eKYC verification, it will speed up the onboarding and data exchange procedures.
How Can Companies Implement eKYC?
One of the first considerations for companies intending to transition from traditional KYC to eKYC is the technology or mixture of technologies to employ. It is critical to balance company demands with eKYC compliance standards, information security, onboarding simplicity, and, of course, budget.
- When searching for the best eKYC solution, seek one that can Integrate with current systems
- Reduce friction in customer interactions and unnecessary delays
- Meet and far exceed any applicable regulatory standards
- Provide real-time filtering against reputable information sources
- Evolve and adapt to a shifting fraud-detecting landscape via advanced technology like AI and ML
- Demonstrate its worth by obtaining certification from organisations such as the International Organisation for Standardisation (ISO) 27001
Having discussed the many advantages that a third-party eKYC solution provider can bring. When businesses begin their search, many providers state that their system is built on powerful AI and machine learning algorithms. That is all well and good, but some go beyond AI and incorporate human touch. All data their AI verifies gets revalidated by live people, adding an additional layer of verification and reducing the possibility of inaccuracy.
Why Verify Digitally with Shufti?
Every day, authorities and governments face increased pressure to strengthen money laundering regulations to eliminate financial crimes. Shufti assists businesses in onboarding new clients by understanding consumer behaviour, developing risk profiles, and monitoring ongoing eKYC. Shufti provides electronic KYC solutions in 240+ nations and regions whilst supporting 150+ languages. Shufti is assisting businesses in avoiding scams and complying with stringent regulations.
Here’s what sets apart Shufti’s eKYC solution:
- API and SDK that can easily integrate into the client’s existing system
- No document uploading
- 99.77% accuracy rate and verifies clients in seconds
- Comply with stringent AML and KYC regulations
- Fast customer onboarding reduces friction and unnecessary delays
- Real-time authentication from government databases
- Risk profiling using advanced technology and AI
Tired of manual KYC processes and looking to onboard clients whilst maintaining compliance?











