Building an Effective Customer Due Diligence (CDD) System with Shufti
There are various factors that businesses have to consider while implementing measures to gather clients’ information before onboarding them. The customer due diligence (CDD) process is viable for companies in order to ensure that only legitimate entities are onboarded and business operations are streamlined with regulatory obligations to curb financial crimes.
CDD in financial corporations is a crucial aspect of KYC/AML compliance. There are numerous global regulators that have legislated strict standards and guidelines developed over the years to reduce the threat of money laundering and other financial crimes. Among various global financial watchdogs, FATF and FFIEC are putting efforts and are developing strict laws to curb money laundering, financing terrorist and other financial crimes. Yet, cybercriminals are also getting more sophisticated and are using enhanced technologies to manipulate security systems. Therefore, customer due diligence procedure is becoming important for businesses.
€500K Fine Imposed on Rabobank for KYC Failure
The Central Bank of Dutch (DNB) issued a draft for Rabobank on 12 October 2021, that highlights the shortcomings in their AML/CFT framework. DNB ordered the bank to enhance the customer due diligence, transaction monitor, and suspicious activity reporting mechanism. However, due to KYC failure, the Dutch anti-money laundering department has imposed a fine of EUR 500k to Rabobank.
The draft came after the last order received in September 2018 that ordered the bank to “improve its Know Your Customer (KYC) compliance activities.” However, on 1st April 2020, “DNB carried out an investigation and concluded that Rabobank did not meet the injunction requirements, despite all efforts.”
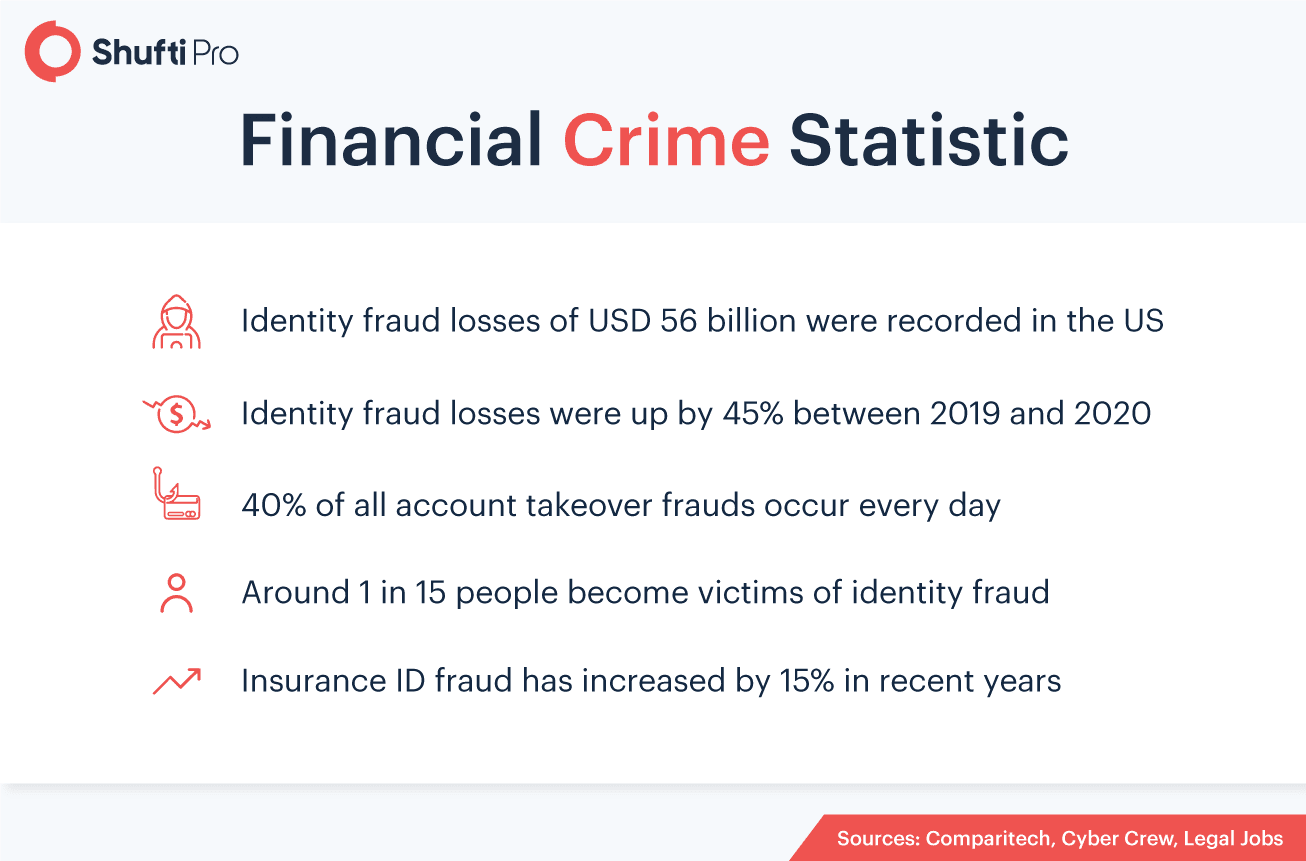
Key Factors for Financial Firms to Build CDD System
Customer Identification
Before onboarding customers, companies are required to identify their real identities in order to ensure that their clientele comprises legitimate individuals and the potential risks that can disrupt business operations are minimized. To do so, companies require personally identifiable information (PII) such as an address, phone number, ID number, name, and more from the customer.
In addition to this, businesses also acquire government-issued documents and other relevant documents from authentic sources having clients’ photos. To verify the address, companies can utilize secondary documents like insurance documents, bank account statements, and utility bills.
Business Verification
Companies and other corporate entities also need to incorporate authentication measures to determine the legitimacy of the businesses before establishing any kind of B2B relationship. This approach helps out companies in multiple ways – it assists them to comply with KYB regulations and also safeguards business interests. To verify a business, information like registered name, trademark, location is gathered and verified.
Apart from this, the Ultimate Beneficial Owners (UBOs) of the businesses are also required to be verified as they can pour adverse impacts onto the partnering businesses. This whole process can only be completed by undertaking customer due diligence measures. This is the way businesses can ensure that criminal attempts are identified and deterred at an early stage.
EDD – Going an Extra Mile for Risk Assessment
Through their risk assessment processes, businesses determine whether there is a need for simplified due diligence or Enhanced Due Diligence (EDD). In any case, it’s crucial for businesses to carry out CDD procedures in a well-mannered way to ascertain whether EDD is necessary or not. This is a continuous process, as clients can transition into high-risk categories as time passes, so performing due diligence periodically could be fruitful.
For instance, most jurisdictions require politically exposed persons (PEPs) to undergo the enhanced due diligence procedure as they are considered high-risk entities. Other factors that drive EDD are accounts with unusual transactional activities, a large volume of money transferring to international accounts, and adverse media mentions. To practice EDD, the potential customers’ location, occupation, transaction types, and names are determined.
In the case of businesses, UBOs, as well as connected entities, are identified. Strict anti-money laundering procedures and KYC checks are imposed on them to authenticate their identities. In addition to this, companies can overcome the risk of regulatory sanctions and hefty fines.
Gathering Third-party Information
To successfully run their operations, businesses have to rely on third parties including banks, audit companies, and lawyers. In order to perform effective due diligence, companies need to strengthen their processes and choose these third parties wisely. In cases of unfortunate events, the responsibility for CDD measures always falls upon the company, not the third party. Sometimes, getting the information required for CDD is only possible through a trusted third party, where sufficient optimization of business processes and standards is very important. In the end, the company itself is responsible for paying the non-compliance fines.
Ongoing Monitoring and AML Screening
The story doesn’t end when businesses have onboarded customers or developed B2B relationships. Companies are required to continuously keep an eye on clients’ activities for risk assessment. However, new technological innovations have provided businesses with effective and innovative suspicious activity reporting (SAR) and transaction monitoring systems that can generate accurate results. With such systems, individuals can be categorized according to risk levels and due to the predicating algorithms, customers’ transaction history can forecast future outcomes and update the clients’ profile accordingly.
With ongoing transaction monitoring and AML screening systems, customers’ background is checked against financial crime databases and global watchlists for better risk analysis. This also allows businesses to notify regulatory bodies regarding suspicious activities in due time. These steps support banks and other businesses to identify shady transactional patterns and monitor customers’ activities.
Key Challenges for Financial Institutions to Ensure CDD
Data quality
Financial and non-financial institutions find it hard to manage and aggregate customers’ information. As regulations continue to evolve, it is driving businesses to gather comprehensive data to improve risk assessment systems and control structures. However, the unavailability of rich data leads to suspicious decision-making as data integrity has a significant impact when carrying out due diligence procedures.
Cultural Issues to Gather CDD Information
This problem usually occurs in underdeveloped or developing countries where culture is valued a lot. Therefore, businesses operating in such nations find it quite challenging to perform CDD. customers are hesitant to provide personal as well as business-related information. This makes it difficult for companies to identify clients before getting them on board.
Identification of Ultimate Beneficial Owners (UBOs)
Identifying UBOs is also challenging for most businesses. However, many jurisdictions are making a strict regulatory framework for UBOs verification. As a result, for businesses, there are heaps of policies and requirements that are setting various thresholds for the identification of UBOs. companies that work globally, find it hard to determine beneficial owners located in other countries. There are several examples where the guidance for verification is not elaborated properly, which creates ambiguity.
What Shufti Offers
Shufti’s robust identity verification solution helps businesses to carry out customer due diligence procedures in a streamlined way and assists to comply with the regulatory obligations. The AI-powered solution can identify customers by verifying true identities. In addition to this, ID documents are also authenticated through various document checks in real-time. Furthermore, businesses can screen individuals against 1700+ global watchlists including PEPs through rigid AML background screening services that provide companies to build transparent B2B relations.
Want to know more about Shufti’s identity verification and background screening solution?











