What are the Key Differences Between CIP and KYC?

The terms Customer Identification Program (CIP) and Know Your Customer (KYC) refer to two distinct procedures in AML compliance. Since businesses often use CIP and KYC interchangeably, the distinction between CIP and KYC is usually confusing.
A KYC procedure comprises multiple components that work in tandem to verify a customer’s identity. CIP, on the other hand, is a term used by the US Federal Law that also refers to customer identification. However, despite their functional similarities and interchangeable use, it is important for businesses to understand the difference between CIP and KYC.
What is CIP?
A CIP is a set of procedures that certain businesses must follow to verify their customers’ identities. The CIP regulation outlines measures businesses must implement to establish a “reasonable belief” of each customer’s true identity upon onboarding.
Through this verification of customer identities, CIP essentially serves as the first line of defense. Introduced in 2003 under Section 326 of the USA PATRIOT Act, CIP mandates a framework that businesses must use to verify the identity of their customers and take measures to prevent financial crimes such as money laundering beforehand.
What are the six elements of the CIP Rule?
To establish the minimum standard for businesses to follow when identifying their customers, the CIP Rule was published to help businesses set a minimum standard of procedures that should be put in place. The six elements of the CIP rule are broad and general, so businesses may fulfill the minimum requirements of CIP in a manner most convenient to them. The six elements are:
- Establish CIP: create a document outlining your Customer Identification Program.
- Customer Identification – collect basic customer details such as name, date of birth, address, and identification number (SSN, TIN, etc.)
- Identity Verification – Verify customer identity using doc or non-doc methods within a reasonable time after the account is opened.
- Record-Keeping – Store and maintain records of the information and documents used to verify customer identity.
- Screening – Screen the customer against the Sanctions and Terrorist Organizations lists published by relevant US Federal institutions.
- Notice – Notify customers about collecting personal data for the purpose of verifying identity at the time of account opening.
Does the CIP Rule Apply to Every Financial Institution?
The CIP rule applies to every financial institution. The definition of a financial institution, and what entities can be considered one, is found in the Bank Secrecy Act (BSA).
While common examples include banks and lenders, the definition of financial institution under BSA also includes fintechs, the U.S. Postal Service, and telegraph companies.
What is KYC?
Know your customer (KYC) is an umbrella term that involves multiple regulations that businesses must follow. It is a long-term process that assesses customer risk on a regular basis to prevent financial crimes such as fraud, money laundering, and terrorist financing.
The purpose of any KYC measure is to assess the risk of money laundering associated with a customer. It is a continuous process to understand the customer’s financial behavior in order to detect any suspicious financial activity throughout the period of time the individual remains a customer of the business.
What is the Difference between KYC and CIP?
KYC is not a single set standard that businesses have to follow throughout. Different jurisdictions prescribe different KYC measures that businesses must undertake. For instance, the fifth Anti-Money Laundering Directive of the EU (5AMLD) directs member states to implement KYC measures that broadly include:
- Verification of customer identity.
- A risk-based approach towards KYC, with Enhanced Due Diligence (EDD) measures for high-risk individuals such as PEPs.
- Ongoing risk assessment of customers to detect any suspicious activity.
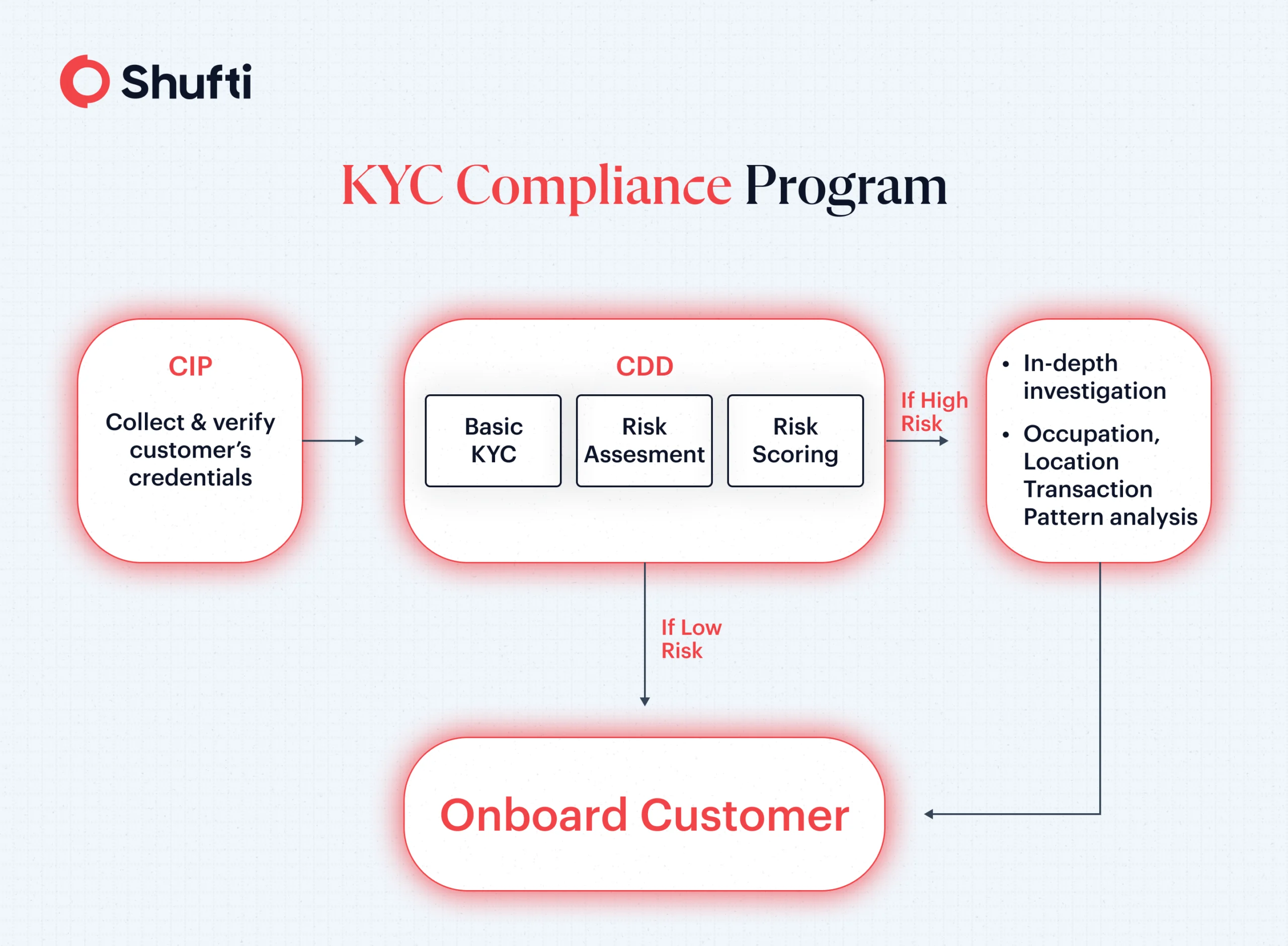
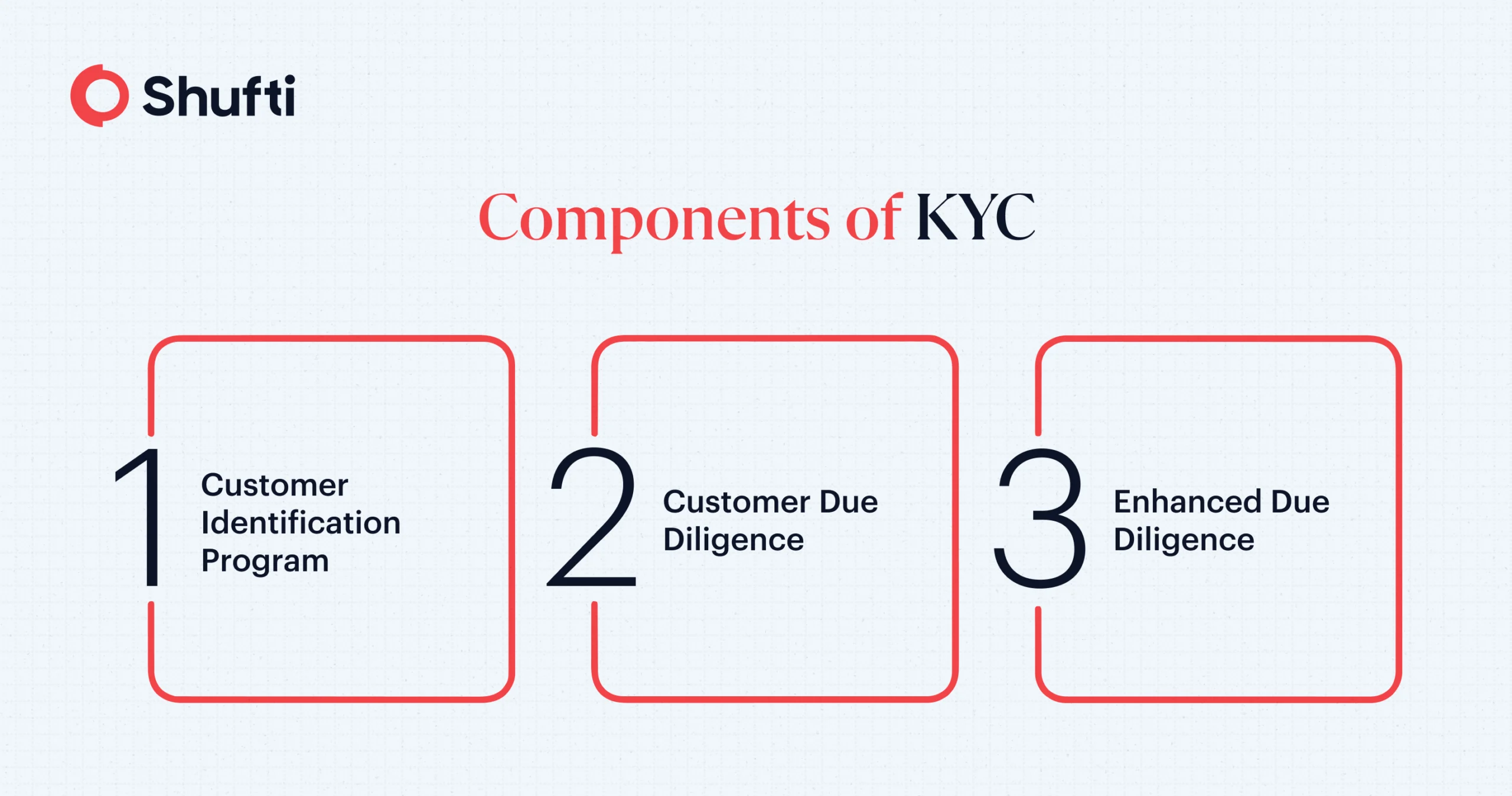
Similarly, according to U.S regulatory law (USA PATRIOT Act and Bank Secrecy Act), a KYC framework is made up of three main elements:
- Customer Identity Program (CIP) – FinCen’s six CIP Rule that verifies the identities of customers.
- Customer Due Diligence – for analyzing and processing data collected from CIP and third parties for assessing customer risk.
- Enhanced Due Diligence – Additional scrutiny for high-risk individuals, such as verifying sources of wealth and enhanced monitoring.
Simply put, the main difference between CIP and KYC is that CIP is part of a broader framework that is called KYC. While one part of this framework focuses on identity verification (CIP), other parts conduct customer risk assessments and ongoing monitoring (CDD/EDD). Thus, KYC, as per U.S regulators, includes CIP, CDD and EDD.
Choose the Right Partner for your CIP and KYC Compliance
The right partner for your KYC verification and Customer Identification Program is crucial for staying compliant with regulatory requirements. With Shufti’s, U.S businesses are equipped with the right tools to stay compliant with the six requirements of the FinCen CIP Rule:
- Verification engine for ID documents from over 230+ countries.
- Support for all document types (such as Passports, ID Cards, Driving Licenses, and more)
- Non-Doc ID Verification for quick and secure customer onboarding.
- Advanced biometric checks, including anti-spoof liveness detection, for reliable identity verification.
- Cost savings with customized ID verification tailored to your risk appetite.
Make CIP compliance hassle-free with Shufti. Get in touch – Talk to one of our specialists today!

 Explore Now
Explore Now













