KYC Compliance – Strengthening Fraud Prevention Across the Globe

Know Your Customer (KYC)
The widespread availability of the internet has made our world more connected than ever. This, however, has made our information more vulnerable to fraud. The ever-climbing fraud statistics continue to trouble consumers and businesses as well as regulators across the globe. Yet traditional practices for Know Your Customer seem no longer effective. With the increasing scrutiny of regulatory bodies and global financial regulators, businesses need to come up with an effective Know Your Customer Compliance process. The KYC process involves the verification of the identity of individual customers for preventing fraud and money laundering activities.
Traditionally, banks and other businesses performed KYC manually. However, manual customer compliance and KYC procedures take longer and tend to frustrate customers. For banks too, manually verifying and vetting each customer can be costly and arduous. Herein, comes the role of SaaS KYC service providers. Providers of identity verification as a service, nowadays are using machine learning, advanced biometrics, and a combination of Artificial and Human Intelligence capabilities to verify end users. It is an all in one solution that is equipped to fully automate KYC procedures and customer compliance programs in companies.
A comprehensive KYC and AML solution can effectively fulfill a business’s Know your customer compliance requirements. It not only makes the implementation of compliance obligations seamless but can also improve the onboarding process. Its KYC services include document, face, and address, consent verification along with global AML background checks, and video KYC solution.
Some of the major KYC and AML procedures that Shufti offers include;
- Document Verification
- Face Verification
- Address Verification
- AML Background Checks
- Consent verification
- Video KYC solution
Document Verification
A simple and efficient way for banks, financial institutions, e-commerce stores, crypto exchanges, ICOs, and a number of other businesses is to verify customers through document verification. It encourages customer compliance and allows businesses to verify users through multiple documents including ID cards, passports, driver’s licenses, credit/debit cards, utility bills, and other customized documents that a business may need verification, for its users.
The verification of the document(s) can be personalized for business, according to its need to verify its users. For example, an online retailer would want to verify the address of its customers to avoid shipping fraud and errors. Different features of a document that can be verified include Name, Date of Birth, Age, Date of Issue and Expiration, Document Number (MRZ code, passport number, etc.), Gender, Nationality, etc.
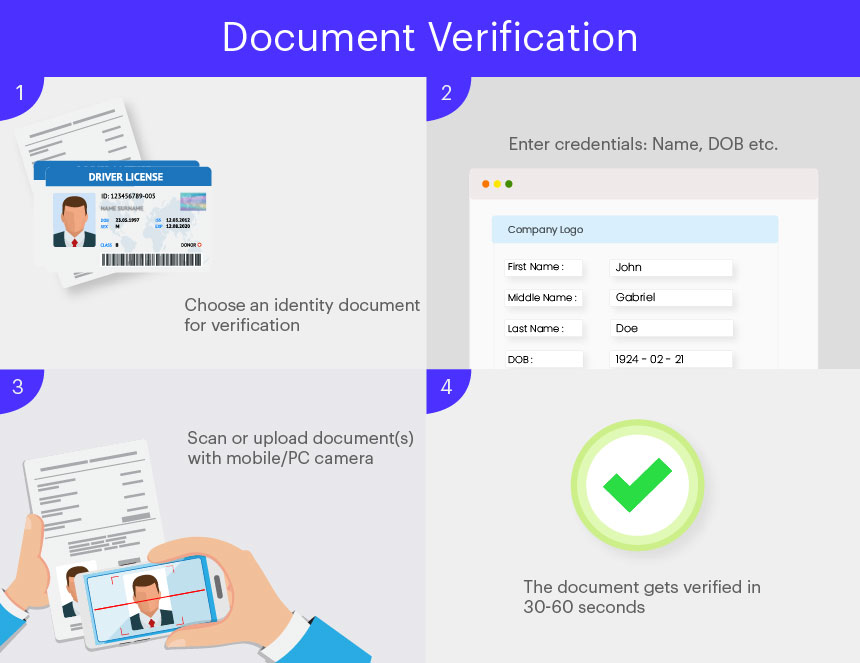
The process of document verification for a business is simple and easy. All they have to do is select the mode of verification (onsite or offsite) and document checks they want. The rest is taken care of by the verification software. The process of document verification involves;
- The end-user or customer comes in for verification and selects the type of document he/she wants to be verified by. It is up to the company to provide multiple options for its customers for verification including ID card, passport driver’s license, or any other ID document.
- The user then scans their document(s) or uploads a copy of it to verify their identity.
- The system verifies the user using hybrid AI and HI technology in 30-60 seconds.
Face Verification
Face verification nowadays is normally performed through a facial recognition software developed on AI-based protocols. Biometric facial authentication is usually performed by businesses that run a higher risk of attracting fraud and financial crimes like money laundering, bribery, and tax evasion. This may include but is not limited to, banks, insurance providers, investment firms, crypto exchanges, ICOs, and forex companies. All such businesses are highly regulated and require additional protection from fraudsters and criminals.
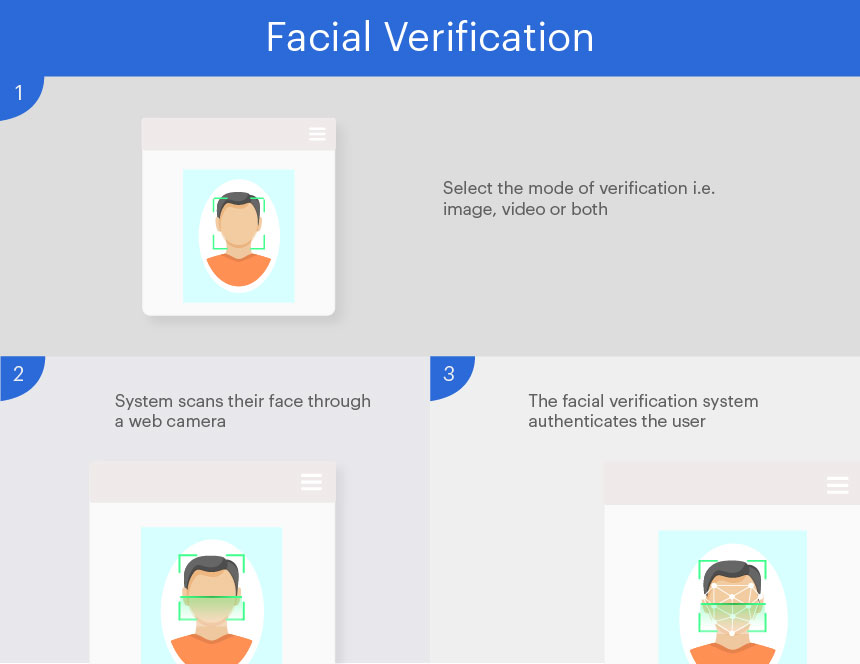
Performing facial verification is simpler than document verification and only requires the end user to show their face in front of the web camera. Alternatively, they can also upload a picture to authenticate their identity. The choice to verify the user through image or video or both lies with the company availing KYC services. An end-user is verified in the following way in the face verification feature;
- The end-user comes in for facial verification
- They show a fake or photoshopped image for verification
- The facial recognition system declines the verification since a fake image is being used for verification.
In another case,
- The end-user comes in for verification
- He/She will show their actual face or image for verification
- The verification is approved as the software detects the presence of a real person, or does not detect any photoshopped elements in the image used for verification.
Address Verification
E-commerce sites, online retail businesses, and banks often require address verification of customers in order to check if the person is using legitimate credentials to gain access to services. Address verification services allow for better and more convenient authentication of users around the globe. It is the fundamental solution for businesses to eliminate identity theft. Address verification further increases the accuracy in the shipping of orders allows companies to conveniently deliver merchandise to customers.
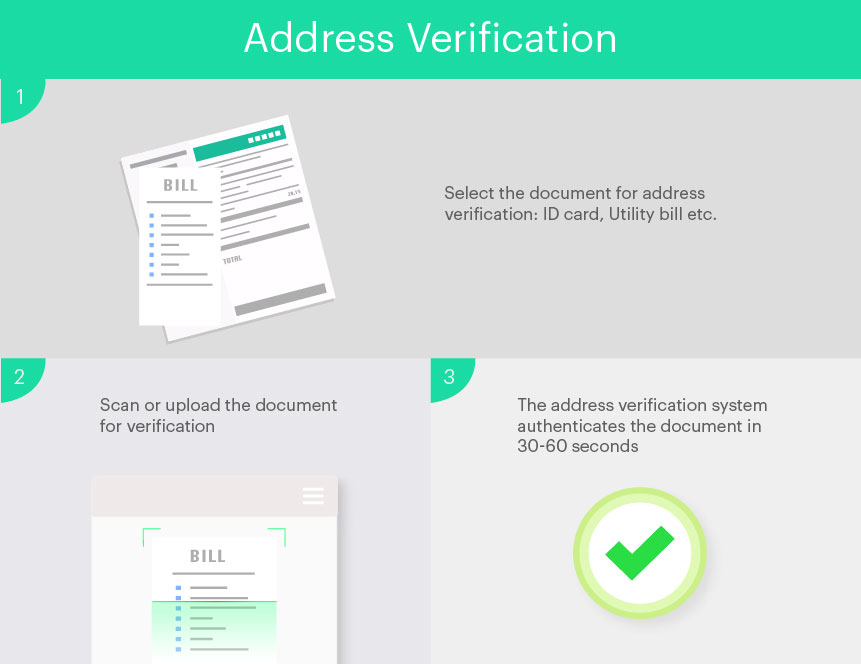
Address verification is performed using a number of different documents including utility bills, bank statements, tax bills, ID cards, passports, etc. The system is also able to corroborate addresses using different documents. Therefore, if either of the documents is forged or stolen, the system will stop the verification. The address verification process is performed in the following way;
- The user selects the document using which he/she wants to verify their address. It is up to the company if they want to provide their customers or users with various document options with which they want to verify their address.
- Scan or upload the document for address verification.
- The system will use data extraction protocols to verify the address of the user.
AML Screening
Banking and financial institutions are required to perform customer due diligence (CDD) for individual customers and clients. For higher-risk individuals, they are obligated to perform enhanced due diligence (EDD) to evaluate, assess, and eliminate the risk they pose to the institution. For more efficient risk assessment, the AML compliance program for screening each individual client is a must.
With an AML screening system, banks can now easily screen new and existing clients through a foolproof system. The screening process flags PEPs and high-risk individuals from a vast database. It contains data from over 1000 sanction lists and 3000+ databases. Some of the lists through which end users are scanned include OFAC, FATF, DFAT Australia, FinCEN, CIA, FINMA, and numerous others. The databank is updated every 14 minutes to account for any updates in the lists. Banks and other financial institutions can choose to implement batch screening or ongoing screening for their clients. Batch screening screens individuals in bulk in one request whose basic name and DOB are already known. In ongoing screening businesses operating in a high-risk environment can issue an “on-alert” status to clients with a greater risk profile.
AML compliance program is generally availed with KYC verifications and checks are run in the background.
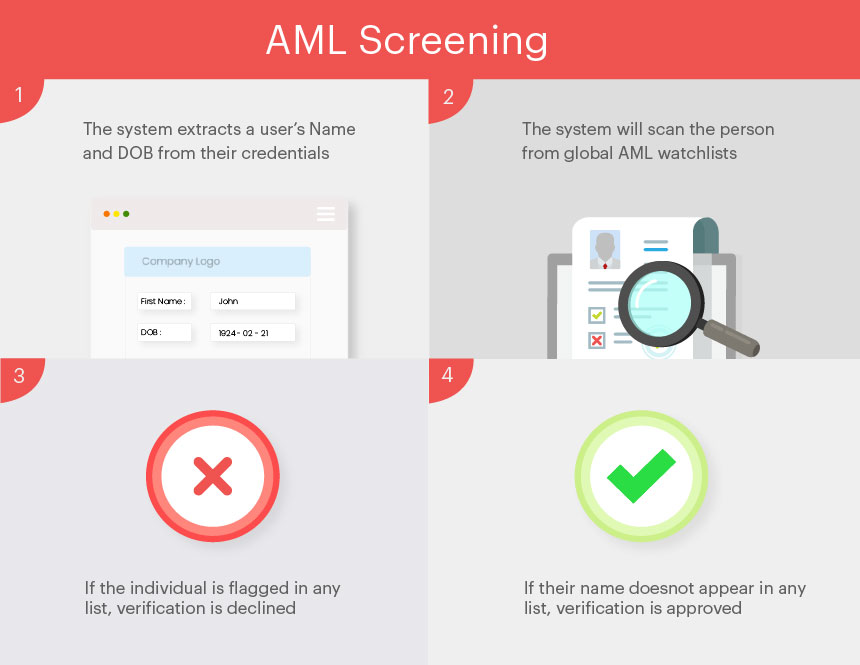
- The system extracts a user’s Name and DOB from their credentials as they perform their identity checks.
- The system will scan the person from global AML watchlists (FATF, OFAC, Terrorist Financing, FinCEN, DFAT, etc.)
- If the individual is flagged in any list their verification will be declined and the company will be notified of a specific individual’s flagged status.
- If they are cleared, their verification is approved.
Consent verification
It is one of the solutions unique to Shufti alone. Consent verification uses the technology of facial recognition along with liveness detection to verify the remote presence of customers in real-time. The process is quick and easy. The identity of the user is verified through a live selfie along with a unique or predefined printed or hand-written consent note which implies that the person in question gives his consent for the online transaction, for example. Shufti checks for the authenticity of the consent note or ID document. The rate of credit card chargebacks rises by 20% each year. Consent verification ensures ‘Know your customer’ compliance and helps with the quick onboarding of legitimate customers which as a result protects businesses from high-risk transactions, chargeback requests, and friendly frauds.
The end-user is verified in the following way in the consent verification feature;
- End-users provide their consent with a consent note along with their live selfie
- They are then asked to show their face to the camera holding client’s choice of the document (it can be an ID document or a handwritten consent note)
- The verification is approved or declined based on the live-ness, the validity of the consent note, or predefined document template
Video KYC Solution
There are a few processes businesses can use to verify their customers. One such process that Shufti pro offers is KYC through a video call. Video KYC is a process of remotely identifying the customers which overcome the hassle of verifying documents manually. Video KYC has been in the spotlight especially for the banking sector and related financial institutions. It offers a quick process of onboarding customers with minimum obstacles and low KYC costs. VideoID is considered one of the most significant developments in KYC since it uses an online video interview with a KYC expert for customer authentication. The KYC expert authenticates the documents while ensuring customer compliance and through AI-enabled facial recognition technology, does a liveness check in real-time to make certain that the person is who he says he is. Which, further, prevents businesses against spoof attacks, deep fakes, and synthetic identities.
The steps involved in the Video Customer Identification Process are as follows:
- Customers register themselves on the client’s platform
- The client schedules a live video call with one of their KYC experts
- Customers are asked to show the identity document live during the call
- Shufti pro analyses the information and the legitimizing of the individual using AI-techniques
- Verification results are delivered to the client
Requirements for Each KYC Procedure
The documents required from each end user for a KYC verification depends on the company availing the KYC services. Each company has its own requirements of customer compliance and verification of its users. However, certain standard documents are used by most businesses to verify their users. These documents include ID cards, passports, driver’s licences and credit/debit cards. The company can choose to provide different options for verification for its users or set a standard document through which the person can be verified.
Documents for address verification include, but are not limited to, utility bills, bank statements, tax bills, rent agreement, employer letter, insurance agreement and other standard ID documents. The AML checks require the full name and date of birth of an individual that can be extracted – or entered – during the KYC process. Whereas, video KYC requires the remote presence of an individual.
It must be noted that the requirement for each verification is set by the company availing the identity verification services. They may ask for only one or multiple documents for verification from each user according to the needs of their industry and the regulations they are obligated to adhere to.
Industries that Adhere to KYC Compliance
Know your customer compliance applies to a vast range of industries. Different businesses need to adhere to KYC requirements of their region as well as the region(s) they operate in. Some of the many industries and businesses that require KYC procedures include, but are not limited to;
- Banking, Financial Services and Insurance (BFSI) Industry
- E-commerce businesses
- Foreign Exchange Brokering Services
- Cryptocurrency Exchanges or Companies dealing with or operating on cryptocurrency (ICOs, Bitcoin wallets etc.)
- Freelancing platforms
- Telecommunication Services
- Travel and Hospitality Services
- Peer-to-Peer Marketing
- Online Gaming and Gambling
- Healthcare Industry
- Real Estate Sector
Standard KYC Compliance Procedures Around the Globe
Every jurisdiction around the globe has its own set of regulations and requirements for businesses to operate safely. Different countries and regulatory authorities set their own standards according to their legislative structure. However, standard KYC requirements are fixed for most regions across the world. Most know your customer Compliance Procedures are centred around:
- Digital Identity Verification.
- Electronic identity Verification or e-IDV, that verifies individuals through different government or independent databases.
- Address verification through different documents
Any specific distinction in the process of KYC exists based on;
- Use case – The use case for each business involves in what capacity a business might need KYC, how it would apply KYC procedures.
- Regulatory Requirements – regulatory requirements differ based on the type of industry, the level of risk an individual or business may pose and the region in which an enterprise operates in. For example, in a few countries including Germany, Spain, Switzerland and Austria the regulations require businesses to verify users through video conferencing
- Type of Business – the risk associated with a business also comes with the industry it operates in and its nature. For instance, financial service firms are bound by more legal obligations than perhaps an online retail store.
The identity solution from Shufti offers universal language support, along with the ability to verify over 3000 documents. This allows us to verify users from over 230 countries around the world. Our AML databank includes names of Politically Exposed Persons (PEPs) from over 1000 + sanction lists and 3000 + databases. It is currently catering to a diverse set of clientele ranging from financial services to online retail businesses to crypto companies. With the ability to verify users in under a minute, Shufti can fulfil a business’s KYC compliance requirements with increased efficiency.
Recommended for you: