Document Authentication | Streamlining Onboarding, Compliance & Fraud Prevention

Before the world experienced digitisation due to the advent of smartphones, fast-speed internet, the emergence of automated technologies, and the pandemic, many industries could only authenticate customers’ identities by physically matching the face of a client with that of provided in the ID document. Yet, it was hard and had multiple shortcomings. For instance, if customers provided a document without a facial image or if the verifying officer missed the essential fields or failed to determine forgery risks, the verification of a client remains doubtful.
However, enhancements in kyc verification methods and strategies and the emergence of facial biometric and online document verification backed by AI algorithms have redefined how businesses authenticate and onboard customers. With these tools, businesses can access a wide range of KYC and AML checks, helping them ensure compliance and avoid financial losses. According to the Goode Intelligence research, digital identity and document authentication services will be worth $15 billion by 2024.
What is Documentation Authentication?
ID document authentication defines a process in which businesses can validate the proof of identity (POI) provided by the customers. Depending on the nature and severity of the client identification programs, POI can include government-issued documents such as ID cards, drivers’ licence, and others.
Whilst the document verification process may seem excessive, the significance of it can not be neglected, especially when the criminals are getting sophisticated and cybercrime is becoming more complex. For instance, using artificial intelligence technology, criminals can create deep fakes using customers’ identifiable information. This is usually carried out by using identity documents.
One of the key benefits of document authentication is that it helps businesses limit such fraudulent attempts and promote a higher-quality and risk-free experience for every customer. Digital document verification is a top-tier and most advanced fraud prevention solution used across multiple industries, helping companies eliminate the risk of identity theft, accelerate compliance efforts, and ensure secure onboarding.

Manual Document Authentication Challenges Explained
Despite the fact companies are transforming their operations, and due to ineffective solutions, many businesses are still using manual document verification approaches. This type of identity authentication is a tedious, time-consuming, and labour-intensive process, with many errors and inaccuracies. It can become more hard and complex to ensure that the compliance officer verifying the customers’ identity documents has enough knowledge to detect or differentiate between legitimate and forged documents. To do this, companies need to arrange extensive training for employees as well as hire skilled employees, which unfortunately requires heavy investments.
On top of that, manual document verification comes with a greater risk of human errors, as even the most trained officers can miss minor details or make mistakes. However, this doesn’t stop here; it further leads to incorrect decisions, which can impact business adversely in the long run. Last but not least, being slow and tedious, manual verification can impact customer experience, leading to an increased drop-off rate and client frustration.
When is Document Authentication Required?
Document verification is an integral part of regulated industries worldwide, such as the financial sector, due to the rigid aml standards and kyc regulations.
Governments and regulatory watchdogs have designed a set of KYC and AML obligations for global businesses to safeguard the integrity of nations as well as counter emerging fraud risks. An array of acts, laws, and standards are mandated for every industry. One such is KYC, which can be fulfilled by integrating automated, robust, risk-free document authentication solutions. Following are the checks when document verification can fast-track onboarding procedures:
Customer Identification Program (CIP): This is a minimum requirement for the client onboarding and verification procedures, which helps companies determine customers’ true identities. Under Section 326 of the US Patriot Act, the program mandates businesses to verify customers’ details, which is carried out using document verification, recordkeeping, and sharing of verification results with the government and financial watchdogs.
Customer Due Diligence (CDD): All regulated industries need to gather the available details of their customers before getting them onboard and to ensure that the provided data is authentic, businesses need to incorporate document authentication solutions that can automatically match the provided information with the one placed in the ID documents. This ensures the authenticity of a customer.
Challenges of Document Authentication
Here are some of the major challenges businesses face using automated document verification solutions:
Multiple Documents Type
Approximately 6,000+ types of documents are used for verifying customers’ identities. A photo of the identity, personally identifiable information, and NFC chips placed in the documents are extracted, matched, and authenticated to ensure legitimate onboarding. However, using manual, ineffective document verification solutions, businesses can’t verify customers’ documents, or their tool does not support specific templates, resulting in an increased risk of fraud.
Difficulties in Ensuring Accuracy of Identity Verification
Maintaining the integrity of the business, safeguarding brand reputation, and accelerating trust among customers only depends on offering frictionless, reliable, and automated verification journeys. To do so, using fully automated identity verification with value-adding features like robust document checks, OCR reader, and NFC is a must. However, such protocols and solutions require heavy investments, making it challenging for businesses to achieve excellence.
Finding the Right Balance between User Experience & Compliance
As per the regulatory requirements, all regulated industries must comply with the KYC and AML standards. However, the requirements vary industry-wise. To meet compliance excellence, businesses must integrate robust digital document verification solutions that can fast-track and secure customer onboarding procedures.
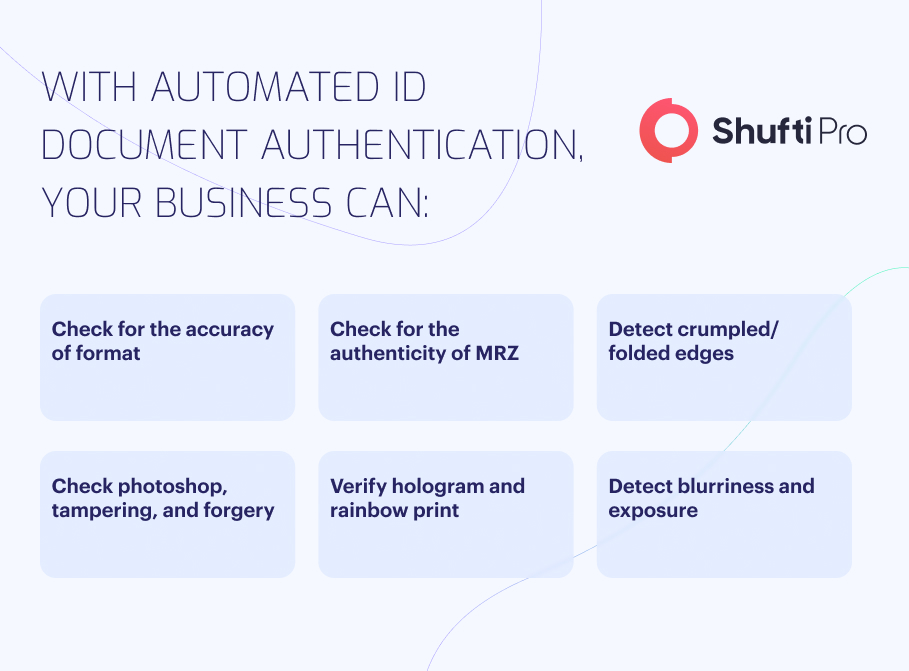
How to Choose the Right ID Document Authentication Software?
Selecting a trustworthy, state-of-the-art, and fool-proof document verification solution is a critical step to becoming credible in the market, ensuring compliance, and making the onboarding journey seamless while balancing security and customer experience. Here are some parameter your business need to have in mind before choosing an ID document authentication service:
Determine Your Company’s Goals: Shortlist your business needs based on your AML and KYC compliance program. Then, choose a document authentication service provider that can offer a customised IDV solution tailored to your business’s evolving needs.
Check for Multi-Modal Verification: In today’s digital age, where fraudsters, as well as regulatory obligations, are becoming sophisticated, having a multi-modal document authentication solution embedded with OCR, NFC, and facial bio is invaluable. These value-adding checks guarantee the highest level of assurance whilst eliminating the risk of identity theft or other document forgery attempts.
Prioritise Automation: Unlike manual document authentication procedures, effective and fully automated IDV solutions help businesses streamline verification and onboarding operations whilst establishing a seamless KYC journey. Such solutions ensure that legitimate customers are onboarded, and performance of both employees and operations is maximised.
Cross-Platform Integration Options: Check for a document verification solution that offers plug-and-play and low-code API integration across all platforms. Easy integration saves both cost and time whilst maximising customer experience.
Support & Updates: As business and regulatory requirements evolve with time, selecting a document authentication service provider that offers technical support as well as ongoing updates with respect to changing requirements is a must.
Document Authentication Solutions with Shufti
Determining the authenticity of customers’ identity documents in today’s digital-first world is not easy but undeniably crucial. With the increase in the crime rate, document forgery, and identity theft, the imperative need of integrating automated document authentication solutions is rising concurrently. Businesses can safeguard their reputation and expand operations globally by ensuring that provided documents are authentic and government-issued.
With Shufti’s full-scale, best-in-class, and fully automated document authentication solution, businesses can customise the verification as well as onboarding journey while ensuring a seamless customer experience. Our solution supports 10,000+ ID document types in 150+ languages, across 240+ countries and territories.
What Shufti Offer:
- Complete data extraction choice to align with industry-specific needs.
- Choose from a wide range of identity verification documents.
- Compliance-driven acceptance of specific countries and regions.
- Flexible nationality filters to meet verification requirements.
- AML checks for proactive risk mitigation and compliance with regulations.
Want to boost your customer conversion rates up to 80% with Shufti’s document verification service?

 Explore Now
Explore Now













