Future Prediction of Identity Verification for Businesses

Ensuring a user’s real identification has become crucial in the age of digitisation. Businesses are constantly sprouting on the broad internet, and international transactions can be completed with just one click. Identity verification, which used to be as simple as comparing a person’s face to a photograph on an ID card, has evolved into a complicated web of cybersecurity, information, and technology.
The virtual world is growing as the twenty-first century progresses, and with it, the problem of identifying digital identities is increasing and becoming more sophisticated. The necessity of ID verification is highlighted not only by the rising threats of identity theft and cybercrime but also by the legal requirements placed on companies to verify their customers’ legitimacy. Fraud used to be easy for businesses to spot, but nowadays, with highly developed technology like deepfakes, losses can reach $35 million in some instances.
The change in how individuals live and conduct business is reflected in how client ID verification has developed. The easy and convenient means of authentication are fading into obscurity and complexity as internet platforms replace physical stores and digital wallets take the place of paper money. The promise-filled future calls for better techniques and technology to verify that the individual on the other side of the monitor is, in fact, who they say they are. But moving forward, it’s critical to comprehend where IDV stands right now, the difficulties it confronts, and the innovations that lie ahead.
Why is the IDV Market Growing?
Since a large number of countries and states have established strong legislation and regulatory agencies to regulate numerous industries, including gaming platforms, digital currency exchange providers, and non-profit organisations, more industries are coming under the anti-money laundering (AML) standards. With the EU recently voting in favour of harsher laws for crypto transfers, these governmental measures are only anticipated to get more stringent over the coming years.
Fraudsters are not only becoming prevalent but are also using illegal, sophisticated means to hide hideous crimes. Even in less-regulated sectors like e-commerce, there is a growing need for IDV solutions as fraud grows more prevalent and complex. This is due to the fact that fraud is a major issue in many businesses and causes significant losses. Globally, the e-commerce sector lost $41 billion to online payment fraud in 2022 alone, and it is anticipated that this year’s loss will rise to $48 billion, and within 5 years, the loss will be $343 billion worldwide.
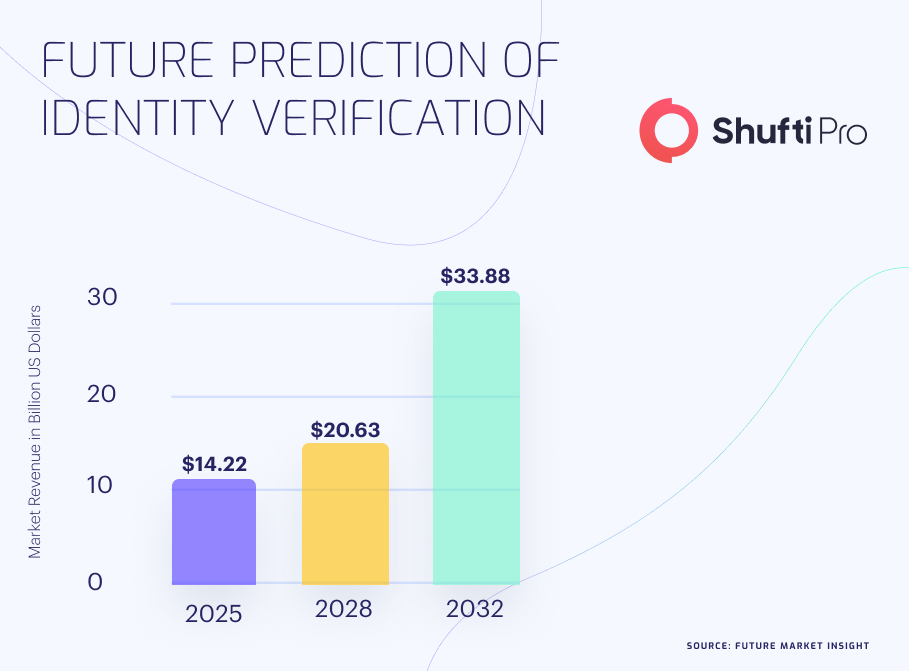
The Rise of No-Code Platforms
The introduction of platforms with no code signifies an efficient move in a time of tremendous technical advancement. Such platforms have decentralised the digital world, removing the conventional barriers of programming, and software development, allowing people and companies to explore and create.
No-code platforms, at their very core, enable users to create, build, and deploy programmes using visual user experiences without the need for conventional programming. Users can create useful goods by simply dragging and dropping various elements. No-code platforms have revolutionised the client ID verification market. Businesses don’t need to revamp their system to add new verification techniques completely, make process adjustments based on real-time input, or respond to regulatory changes.
Pioneering the Future with AI and ML
Artificial Intelligence (AI) and Machine Learning (ML) are not just trendy terms; they are changing the landscape of sectors, reframing possible outcomes, and unquestionably paving the way for the future. They have a profound and transformational impact on the field of client ID verification as well as they become woven into the framework of current technology.
Understanding AI and ML
AI is the general idea of machines acting in ways humans deem intelligent when accomplishing jobs.
ML allows computers to learn from information and change as a subset of AI, gradually increasing efficiency without explicit programming.
Enhanced Accuracy in ID Verification
Traditional identity verification is subject to mistakes. AI-driven solutions provide unmatched accuracy and lower false positives as well as negatives because of their capacity to analyse large datasets and spot trends.
AI is essential for improving biometric identification techniques like facial recognition or fingerprint authentication. AI systems can accurately identify people by examining thousands of facial traits or fingerprints and comparing them to previously recorded information.
Platforms may tailor user experiences using AI and ML. This could entail assisting users through activities based on their prior interactions or configuring security measures to suit unique risk profiles in the framework of ID verification.
Nonetheless, artificial intelligence and machine learning are shaping the future, not merely improving it. They have already had a significant influence on consumer identity verification, demonstrating their potential, and as they develop further, they hold up the possibility of greater security, effectiveness, innovation, and creativity in the future.
ID Verification using Blockchain
Blockchain, which is frequently hailed as the underlying technology of cryptocurrencies, has a huge impact that goes far beyond digital money. The field of ID verification is one of the most potential uses for this decentralised ledger technology. Blockchain has the capacity to fundamentally alter how businesses think about and maintain personal identities due to its built-in characteristics of transparency, confidentiality, reliability, and security.
The centralisation of user data in standard identity verification systems is susceptible to hacks. Blockchain provides a decentralised identity verification solution that gives individuals control over their data and only permits access when it is required.
Users are given control over their data using blockchain. They control who has access to their sensitive data, how long it is available for, and under what conditions. This presents a brand-new paradigm for sensitive information permission and data privacy.
Blockchain offers a ray of light as the globe struggles with the difficulties of digital identity verification. Nevertheless, cooperation between IT companies, government agencies, and businesses is necessary for its wide adoption. Together, they can design a secure, user-focused, and effective ID verification system for the future.
Overall, the combination of blockchain technology and ID verification heralds a time when identities are not only safe but also user-controlled, compatible, transparent, and accessible. The relationship between blockchain and identification will undoubtedly grow as technology advances, opening the door for radical shifts in how businesses view and handle identities.
Big Data Analytics Function
Data is frequently compared to crude oil in the digital era, a precious resource that fuels growth, innovation, and advances businesses. In this data revolution, big data analytics have taken the lead, providing information and trends that were previously hidden or disregarded.
Real-time decision-making is made possible for organisations with big data analytics. For example, analytics can promptly evaluate the risk associated with a financial transaction based on prior information or data and determine whether to accept or reject it.
Businesses can adapt their interactions and services to provide a personalised experience that increases customer satisfaction, retention, and loyalty by analysing user behaviour and preferences. Identification verification procedures can be improved with the help of big data and analytics. These techniques can identify abnormalities, eliminate false positives, and anticipate fraudulent efforts by analysing large databases.
The potential of big data and analytics will only increase as technology progresses. More advanced analytical tools, improved machine learning integration, and a growing focus on data-driven decision-making are all things that businesses can anticipate in 2024 and beyond.
Nevertheless, big data and analytics are more than simply trendy terms; they are transformational frameworks. Their influence highlights the significance of data-driven insights in influencing the future of organisations and the user experience as they traverse a variety of industries, from marketing to ID verification.
The Future of Identity Verification Services
Identity verification is a crucial component of confidence and safety in the modern digital world. It helps to stop fraud, ensures regulatory compliance, and protects people’s identities as well as sensitive private information. Digital identity verification systems use a variety of techniques, such as document verification or address verification and face verification or fingerprint-biometric authentication, to validate people’s identities. Continuous technology advancements and stakeholder cooperation are required due to the enduring challenges of protecting safety, maintaining secrecy, and eluding fraudsters. Identity verification will continue to be important in fostering trust and upholding secure online transactions and interactions as the importance of the digital landscape grows.
How can Shufti Help?
It’s clear that initiative, adaptability, and foresight serve as a compass as businesses explore the opportunities and complexity of the future environment. Reflecting on the latest article on, “Securing Identities in the Age of AI with Identity Verification,” it is very evident that technology and its problems are always engaged in a complex relationship. Restrictions will inevitably arise, but they are only factors for innovation, adaptation, and expansion. The cornerstones of long-term success and resilience as businesses face a rapidly changing future will be planning, educated decision-making, and utilising cutting-edge solutions.
Shufti can be helpful for the purpose of verifying identification. Using our cutting-edge, revolutionary technology, we offer sophisticated consumer identity verification through behaviour-based anti-spoofing detection. Our services are accessible in more than 240 countries and states, ensuring a global presence. We use a 2+2 verification method, offer multilingual OCR Data extraction in more than 150 languages, and have software that instantly recognises fraudulent IDs. Even in very complex regions, our identity verification system maintains regulatory compliance whilst acting as an impenetrable fortress of biometric authentication.
Looking forward to securing the business operation and identities in the age of growing dynamic and multi-complex jurisdiction?

 Explore Now
Explore Now













