How Identity Verification Eliminates Social Media Scams to Enhance User Experience

Social media has experienced exceptional growth in the past decade as a result of advancements in internet accessibility and speeds. In their infancy, social media platforms were hardly a big part of the internet. As time passed, the monumental growth of social media platforms like Facebook, Instagram, and Twitter has taken their usage to new extremes, even playing a critical role in altering election outcomes. However, all this growth and evolution does come with some serious implications for users as well as the platforms.
The insufficiency of identity verification measures on social media platforms can lead to fraudulent activities where people can create fictitious accounts and hide behind pseudonymous identities. As a result, social media platforms have become an ideal breeding ground for online fraud and identity theft, which is becoming a deliberate concern for businesses incorporating social media channels in their marketing campaigns. Other online crimes include social media-induced violence, cyberbullying, and money laundering, all of which can be notably reduced by utilising thorough identity verification solutions.
Social Media – A Perfect Getaway for Criminals
As social media has become a central part of our online lives, criminal activities have found a new favourite home. Social media has given ground for criminal ventures to prosper in a quasi-stealth mode online. Such platforms have also given favourable chances for regulatory authorities to identify in-process crimes and raise the bar for performing future criminal activities. Thus, like many other alterations in communication technology, social media has both benefits of ease of use and costs when it comes to its connection with criminal equity and regulations.
Social media fraud continues to create trouble for both users and businesses, although institutions have managed to figure out the significance of social channels as an unmatched sales tool. Over the years, an increase in social media crimes has been observed, with victims losing more than just money.
Moreover, with digitisation, online frauds are becoming more standardised and involve organised crime groups. In 2022, tricksters are attaining new heights in fraud attack automation. Now, scams are less concentrated on average everyday users and are more so focused on exploiting particular groups to expand conversion rates. This increases the concerns for regulating social media platforms by multiple authorities using identity verification solutions to prohibit crimes.
Practices to Combat Frauds on Social Media Sites
Social media identity theft is becoming more frequent as social networks further coalesce with everyday life. Petty mistakes can endanger your private information, allowing fraudsters to steal your personal information and use your Social Security number or other private data, potentially harming your credit. Several fundamental practices can alleviate this risk and shield your profile, such as personalising your privacy settings, hiding your locality, and utilising a password manager with auto-generated difficult passwords. Protecting your identity on social media is a simple but crucial process to make sure your financial health and personal security are adequately protected.
Identity Verification
The lack of identity verification measures is one of the prime reasons social media platforms expose users and businesses to fraud with an army of fake accounts and profiles. Identity verification can prevent such scams in social media, averting monetary losses and reputational damages. Developments in technology have introduced innovative ways for digital companies to utilise a handful of AI programs to address emergent social media threats.
NFC Verification
The severity and frequency of identity thefts have shown that a considerable number of people are not conscious of the significance of protecting their personal information on social media. Questions around data privacy and having to take extra time are two of the main reason why people run away from IDV solutions. NFC (Near Field Communication) takes less than a second to determine whether a user on a social media platform is authentic or not. All they have to do is to upload an image of their NFC-enabled file and tap the chip on the device to get authenticated.
Secure Connections
Since the main purpose of identity theft is financial exploitation, it is essential to secure payment methods and bank account information. Businesses can minimise data loss on social media sites by securing their connections. This particularly involves restricting entry points and access to specific business areas and creating data backups.
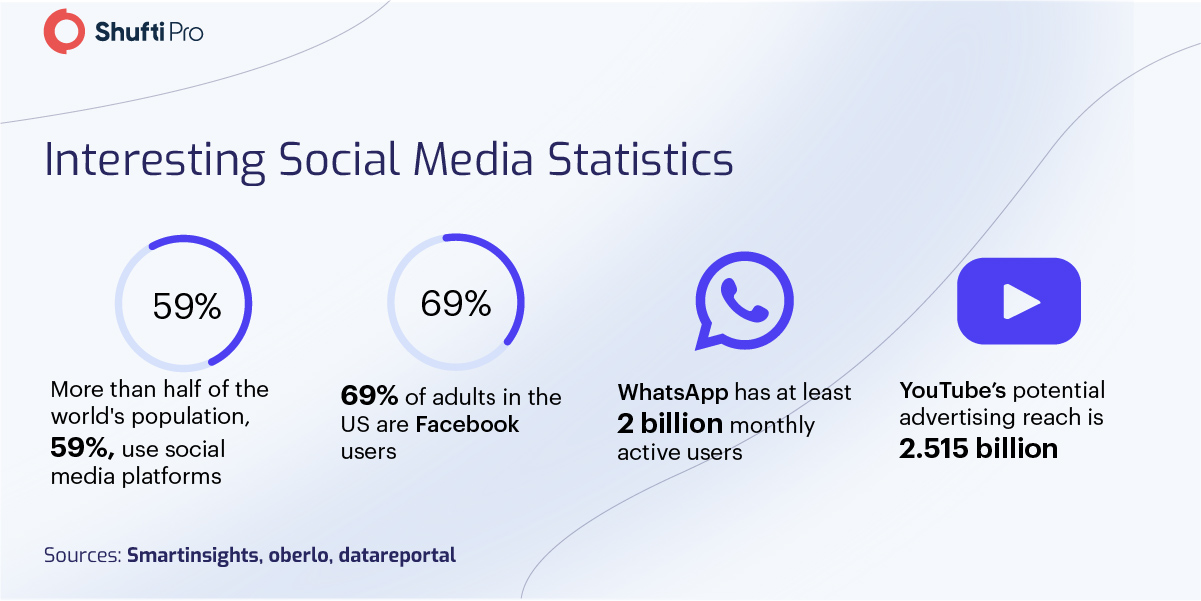
Global Regulations to Protect Social Media Platforms
Businesses, government institutions, and politicians operating through social media platforms face serious consequences from soaring fictitious accounts. Governments across the globe are taking steps to introduce laws for the implementation of identity verification measures on social platforms.
European Union
The EU instigated General Data Protection Regulation (GDPR) to organise a set of rules on how companies, businesses, and other users operating through social media platforms can secure their data. Social media sites face hefty fines if they do not remove extremist content within 24 hours. The European Union has also taken strict actions on copyright protection. Social media platforms are held responsible for not hosting copyright-violating content on their sites.
Russia
Russian regulatory authorities are increasing pressure on companies and businesses operating on social media platforms to inspect online content considered illegal by the government. Those who failed to comply with Russia’s internet legislation have faced penalties and potential blocking.
China
Chinese regulatory authorities have also greatly limited ingress to virtual private networks that some users’ have employed to gain access to the blocked sites. The Cyberspace Administration of China also claimed to have cleared up to 9,328 illegal gambling mobile apps. Furthermore, China has hundreds of cyber police members, who strictly monitor politically sensitive activities on social media platforms.
Significance of Identity Verification for Social Media Safety
Identity verification of users and immediate deletion of illicit content are just some of the regulatory obligations directed at social sites in the UK and within the EU. The suggested law has received heavy criticism for lacking a balance between exempting authentic online scams and defending free speech. Simultaneously, Twitter’s new owner intends to simplify its users’ freedom to convey their thoughts by introducing user authentication.
Most digital organisations and service providers must know who they are doing business with. Those following AML regulations (Anti-Money Laundering) are required to meet KYC (Know Your Customer) requirements to make sure that users’ are trusted individuals—i.e., not bad actors or those under sanctions.
These legislations and regulations have been administered to avert money laundering and other financial crimes. AML-regulated companies that fail to manage KYC obligations may face sanctions, such as heavy fines and face reputational damaging consequences in the market and industry. The laws and regulations are intended to place high command on companies. Still, they are obligatory to keep the company protected, its customers, and thus in a sense society as a whole. These legitimate concerns constantly evolve and vary depending on the authority, industry, and country.
Key Takeaways
Developing a business through social media platforms necessitates steadiness and lawful traffic, which cannot be accomplished unless the platforms are protected. When fraudulent operations step in and try to take control of confidential information to create fake accounts, both the business and its customers lose hard-earned capital profits.
Shufti is a UK-headquartered IDV service provider on a mission to create solutions that eliminate online fraud and identity theft. Presenting ultra-modern Know Your Customer services to enterprises and SMEs, Shufti takes several facets of social media cybercrime trends into account. Shufti’s Identity Verification solution assists businesses to regulate their social media operations smoothly while ensuring customer satisfaction. The risks of online scams can be remarkably reduced by verifying users’ true identities once they register on social media sites.
To get answers to your questions regarding KYC and AML screening, contact us today.











