Identity Fraud and Risk Assessment: An Ultimate Guide for 2023

- 01 Customer Risk Assessment - A Short Overview
- 02 Customer Risk Assessment - Why Do Businesses Need It?
- 03 Risk Score - Adding More Power in Risk Assessment
- 04 Customer Risk Levels
- 05 Risk Assessment - The Processes of Ensuring Secure Operations
- 06 Risk Assessment for Financial Institutions - 5 Essential Steps To Neutralise Crime Threats
- 07 How to Determine Vulnerabilities in Risk Assessment?
- 08 Money Laundering Red Flags Business Need To know
- 09 Fraud Control Plan - Why Do Businesses Need to Develop it?
- 10 Risk Assessment - Ensuring Legit Customer Onboarding
- 11 Minimise Fraud Risks with Shufti
Customer onboarding and business relationships always come with associated risks that must be handled in line with regulatory requirements. A customer risk assessment can help identify areas where businesses might be vulnerable to financial crimes. The primary benefit of carrying out a customer risk assessment is that companies can know their customers’ risk levels before getting them on board. Companies lacking such measures may face detrimental consequences, such as reputational damage, cases of money laundering, and global sanctions. However, due to the lack of this effective fraud preventive measure, the vast majority of fraud either goes undetected or remains largely unreported. Additionally, businesses do not want to report fraud to avoid negative PR.
However, there has to be a way for companies to conduct a customer risk assessment to secure their operations and services. Let’s shed some light on fraud assessment and how businesses can minimise risk with potential new customers.
Customer Risk Assessment – A Short Overview
Customer risk assessment is a step taken during client onboarding, referring to the process in which the potential risk a new customer poses is analysed thoroughly. Businesses can set up risk profiles according to the risk levels by assessing the customers’ information and taking necessary measures to safeguard operations. Customer risk levels help companies to determine the chance of committing financial crimes, particularly money laundering using financial firms. On the other hand, if the regulatory authorities expose potential suspicious activities of customers, that particular firm may be penalised by facing large fines and, consequently, incurring reputational damage.
Due to the high risk of money laundering and other financial crimes, businesses must take essential steps to avoid costly AML fines. Adopting KYC, CDD, and risk-based approaches are some measures a company can take to mitigate these risks.
AML Risk Assessment ensures businesses have a bigger picture of clients likely to attempt terrorist financing or money laundering. Once companies strengthen their AML Compliance programs, they will exponentially reduce the risks that come with inherent exposure to potential companies.
In short, it enables businesses to determine the likelihood of exposure to fraud and the associated financial or non-financial damages accompanying it.
For example, a client with multiple sources of undisclosed channels of income may pose a higher risk of fraud than others. However, generating a risk score based on a set criteria and assigned to such an end user gives a deeper insight into the presence of associated risks.
Customer Risk Assessment – Why Do Businesses Need It?
Today’s competitive landscape is filled with risks, from cybersecurity to bribery and corruption, ID theft is everywhere. Risk assessment is critical in evading money laundering and other forms of financial fraud.
US lawmakers are now applying pressure on enterprises to enforce risk assessment measures to understand their clients.
Risk Assessment also helps businesses to identify any loopholes in their current strategy, fix weaknesses, and improve processes.
Here is why the risk assessment process is essential for business:
- Reduce the risk of terrorist financing, money laundering, and subsequent fines/penalties as a result of non-compliance
- Detect, prevent, and mitigate fraudulent financial and non-financial activities
- Gain clarity on risks associated with customers that will impact the organisation
Risk Score – Adding More Power in Risk Assessment
A risk score is a range company set for the end user according to their risk levels. For example, a score between 0-30 is low risk. Something between 31 and 70 is medium risk, whereas anything above 70 is considered high risk.
Some businesses may consider a salaried customer to have the lowest risk and a self-employed person as medium risk, and vice versa. It all depends upon how a business views a self-employed vs employed.
Customer Risk Levels
Customer risk levels are divided into four brackets, as shown below:
- Low: Customers who successfully pass ID verification checks pose a low risk of illegal activity and money laundering.
- Medium: Customers with issues during ID verification checks and may be flagged for previous signs of fraud attempts.
- High: Customers have a track record of poor business practices, so enhanced due diligence needs to be conducted.
- Prohibited: For security measures, an organisation may not conduct any further business with a customer who has a proven track record of fraud and illegal activity.
Risk Assessment – The Processes of Ensuring Secure Operations
Businesses must now screen potential customers for safe measures and differentiate between high-risk and low-risk clients, facilitated by the implementation of a risk assessment system; companies can mitigate any fraudulent attempts that could lead to severe consequences, such as penalties and fines for non-compliance with AML and KYC.
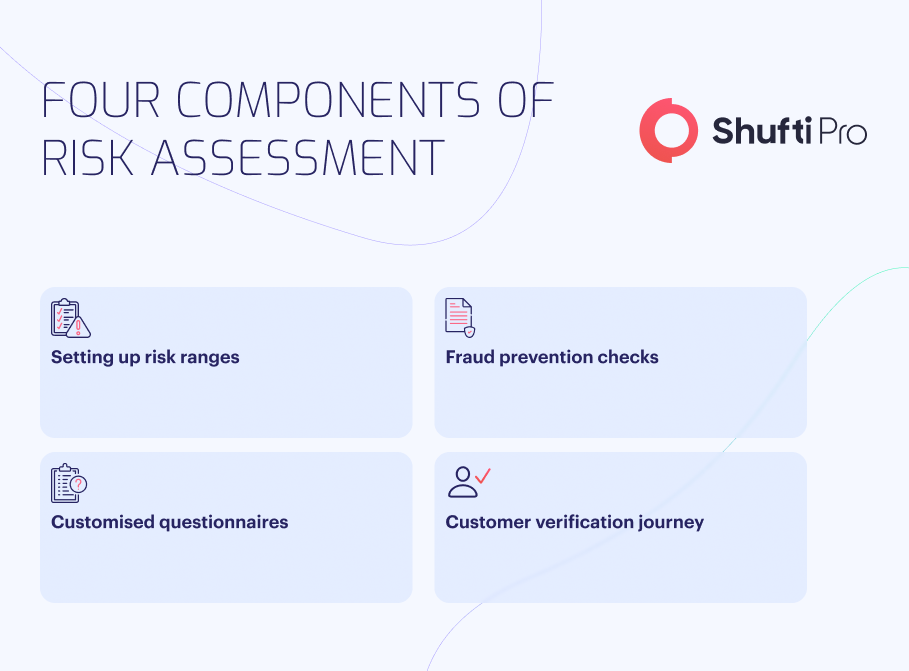
Here are the typical steps any company would follow for risk assessment:
- Set up the risk assessment title and risk range according to business requirements.
- Select the checks from the fraud prevention – data points section to avoid fraud by checking the customer’s PhoneNo, IP, Email, and behavioural risk.
- Create multiple customised risk questionnaires with several answer types by adding scores against each answer option.
- Configure KYC journeys for consumers with Low, Medium, High, and Prohibited risk levels based on the defined risk ranges and requirements.
For example, when applying for a credit card, it is common practise to provide bank statements spanning the prior 6 months to show proof of income.
But besides the internal processes, banks also have to follow the KYC and AML protocols to prevent ID theft and minimise the chances of money laundering.
When signing up for a credit card, the potential customer typically answers a questionnaire about their employment status and monthly income, among other things. The bank will then determine how likely it is for the end user to obtain a credit card without missing timely payments.
Banks aren’t just concerned about timely payments, they also want to ensure that their client does not commit fraud in the future.
Some banks prefer clients to have a fixed monthly income credited to their account at a given date, as opposed to self-employed or retired.
For financial institutions, someone with regular monthly earnings has a lower risk of default than one without a predictable income source.
With a risk score, banks can verify potential customers based on the personal information provided whilst signing up and filling out a questionnaire.
It enables businesses with numerous checks to prevent fraud, create customised risk questionnaires, and configure journeys for consumers with Low, Medium, High, and Prohibited risk levels.
Risk Assessment for Financial Institutions – 5 Essential Steps To Neutralise Crime Threats
Financial institutions deal with a significant risk of crimes on a near-daily basis. In previous years, several risks could only be estimated before they developed into more severe cases presenting a potential risk to a company. A financial analyst could only speculate on various business risks at any given time, whilst having traditional monitoring and risk control systems in place, but more efficient measures were required to determine potential threats in real-time.
A state-of-the-art financial risk assessment process includes a rigid set of policies or protocols to evaluate, assess and address risks a company can face in the near future. Here are five steps that must be included in your business financial risk assessment strategy.
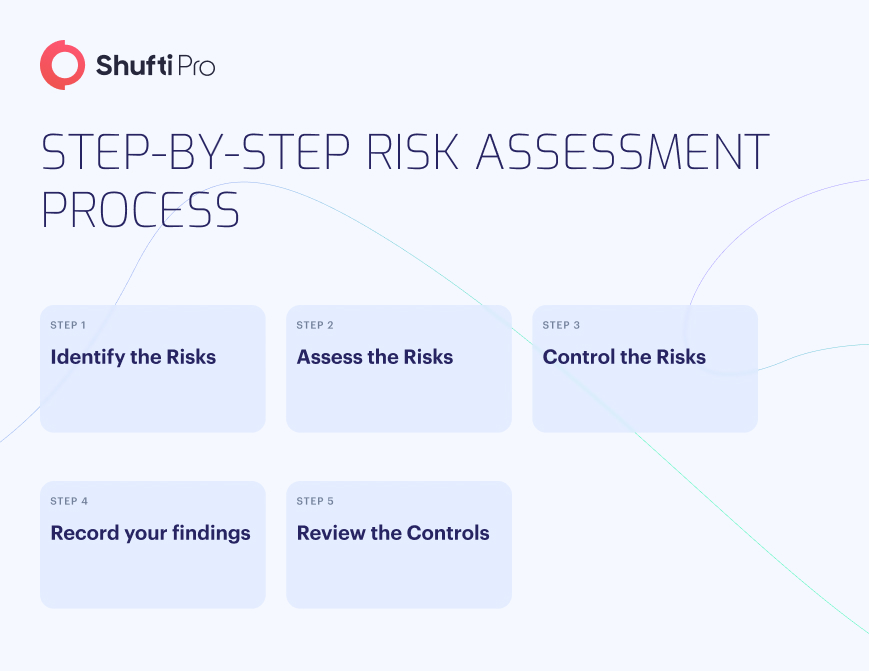
1. Identify the Risk
Every firm faces different types of risk depending on its cash flow, geographic location, industry, and reserve capital. The business financial or compliance department should have knowledge regarding the types of risk they are likely to face. However, in the event of an uncertain situation or potential risk is detected, the executive members need to initiate a risk assessment to evaluate the risk level.
2. Assess and Document the Risk
When assessing risk, a businesses’ primary goal should be determining the worst-case scenario, the likelihood of that scenario coming to pass, and the process required to recover from the potential financial loss.
3. Delegate Management Steps
When risk management steps are required, qualified staff members should be in place to handle the risk-handling procedure. Having a skillful and knowledgeable risk assessment manager will enhance accountability and create seamless interdepartmental coordination.
4. Take Action
If businesses have a rigid risk management system in place, taking action against a customer committing fraud will be fairly straightforward. If a risk is flagged for money laundering, transaction patterns and fund sources will be determined, and risk analysts will be able to detect such suspicious activities prior to the crime being committed.
5. Monitor Progress
As the risk management procedure is completed, assign a designated team to monitor the customers’ ongoing activities. However, if the risk is mitigated, periodic reviews will ensure that new variables are not increasing the level of risk resulting from the original situation.
How to Determine Vulnerabilities in Risk Assessment?
Risk assessments help businesses identify vulnerabilities whilst implementing AML risk assessment. Risk assessment varies based on the size of a business, its clients, and the type of services offered.
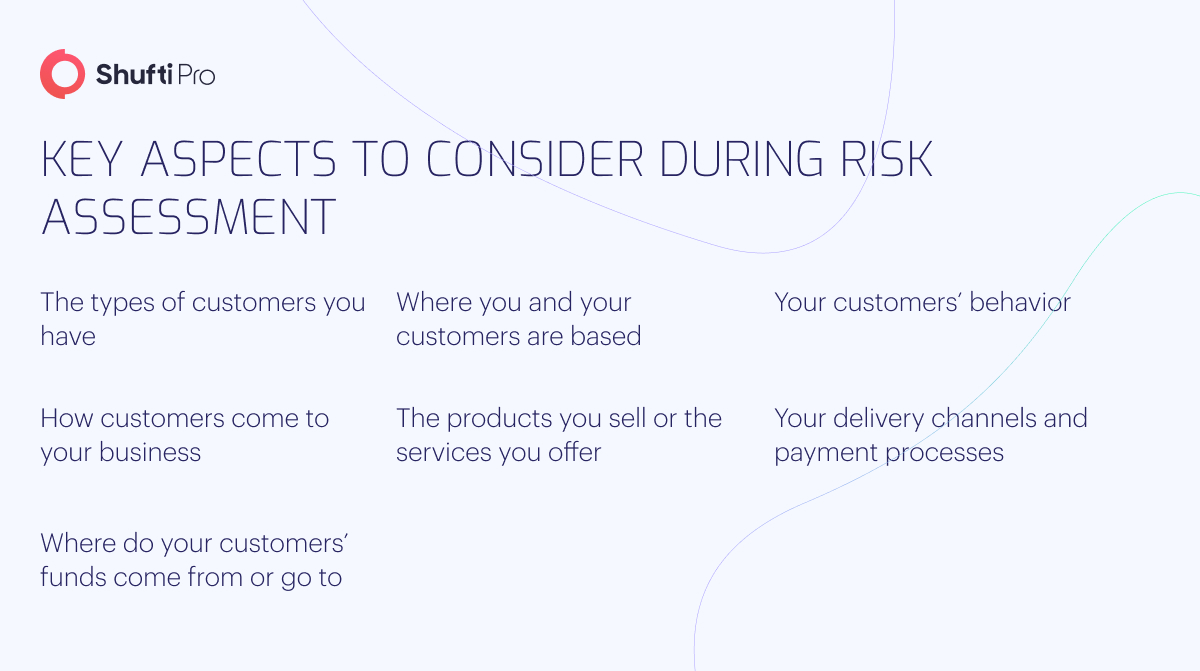
A few questions businesses can ask are:
- Who are the customers you serve?
- What is your customers’ main source of income?
- What are the geographical locations of your customers?
- What type of activities do your clients often perform?
- How do customers find your company?
- What financial risks do your company take?
- What are the origins of funds for your clients?
Getting answers to these questions is critical, as they will determine the past a company needs to take to tackle corruption, money laundering, bribery, and terrorist financing.
Money Laundering Red Flags Business Need To know
Businesses should have a robust security system in place, capable of detecting any suspicious activity.
Here are some common red flags that can put businesses’ reputations at stake if not dealt with appropriately.
#1 Electronic Payments
Accepting electronic payments increases fraud risks and substantially helps cybercriminals to launder money to different channels as legitimate.
#2 Cash Transactions
Be vigilant and exercise caution with cash transactions as it is next to impossible to trace; as electronic systems advance, cash is a safe haven for money launderers. E.g., casinos, restaurants, and even media houses, like news channels, could be lucrative sources of terrorist financing.
If clients are more engaged in cash transactions, this could be indicative of them hiding their illegally obtained money and only showing verifiable funds as a legitimate source of income.
#3 Politicians and Celebrities
Politicians and celebrities may launder money abroad via offshore accounts for purposes of tax evasion and cleaning cash. Since politicians have influential power, they can stop any investigation by bribing officials. This gives them a clean passage to transfer dirty money without getting compromised.
#4 Dealing with Offshore and Foreign Companies
Offshore companies have been historically formed and used for laundering funds without a trace; for example the British Virgin Islands, Panama, Grenada, and other island nations are home to some of the world’s most infamous offshore firms.
#5 Geographic Location
Without any prejudice or bias, unfortunately, some countries have become synonymous with money laundering due to their past track record. Basel AML Index lists countries with the highest rate of financial crimes, drug trafficking, and money laundering cases.
If clients are from countries on the Basel AML index with a high red score, this could prove challenging in continuing business relations with said client.
Fraud Control Plan – Why Do Businesses Need to Develop it?
A fraud control plan is a document that assesses your company’s exposure to fraud, alongside it’s strategies to combat it. Given the high global fraud rate, your business must build a control plan to detect fraud and minimise its impact.
Here are essential elements of a fraud control plan:
- Mission and/or vision statement on zero tolerance of fraud
- Key staff members and responsibilities for controlling fraud
- Key strategies summarising the importance of controlling fraud
- Outline of risk assessment and vulnerabilities
- Outline of known fraud types linked with your industry and their possible impacts on your company
- Outline of strategies for mitigating fraud
- A timeline on actions to implement strategies
- A detailed plan outlining steps to perform when fraud is detected
- SOPs on reporting frauds to law enforcement authorities
This is a generic framework and may vary based on the company requirements and regional regulatory laws in which the business is operational. It is vital for businesses to consult a local attorney and anti-money laundering experts or money laundering reporting officers to build a tailored strategy that fits company needs.
Risk Assessment – Ensuring Legit Customer Onboarding
Risk assessment is an essential component of the customer onboarding process, which is imperative for businesses to detect and mitigate any fraudulent activity. Without a thorough risk assessment process, there will always remain a high risk of working with corporations and individuals prone to fraudulent attempts down the road. Further screening of new customers against sanction lists is vital in minimising chances of financial crime in the future.
But risk assessment isn’t and shouldn’t be limited to the onboarding process. In fact, it should be a continuous process to monitor clients should they conduct activities that do not match their risk profiles.
For example, if a customer suddenly moves to transactions involving high amounts of cash, avoiding bank transfers for payments, and/or using offshore companies to transfer funds. This could be a potential red flag that should alert businesses for potential incoming fraud.
Minimise Fraud Risks with Shufti
Compliance with anti-money laundering laws is no easy feat. The industry dynamics are fast changing, and keeping up with them takes time, effort, and a step in the right direction.
But companies understand that keeping up with the pace of ever-evolving threats is challenging for businesses. That’s where Shufti’s risk assessment solution helps digital businesses keep in line with the industry’s standards and ensure every customer onboard goes through a thorough risk assessment procedure.
Our KYC & AML screening helps businesses to screen every client, whether individual or company, against 1,700+ watchlists to reduce chances of getting compromised. For companies, it isn’t just the finances but the business reputation that matters equally.
Finding it hard to fight fraud, secure operations, and meet compliance?

 Explore Now
Explore Now













