Phishing Attacks and the Role of Two-Factor Authentication

In today’s digital world, almost everything we do is on the internet, be it for official purposes or activities in our personal lives. Digitization definitely brought convenience to lives and it is easier to communicate now. Businesses have so many opportunities now thanks to technological advancements. Nonetheless, the emergence of technology is also benefitting criminals. The traditional methods of stealing and terrifying people are gone, and the virtual road is a better way for them. With the help of Artificial Intelligence and Machine Learning algorithms, cybercriminals can barge into anyone’s social media that does not have strict privacy measures. Businesses experience ransomware and data breach attacks now and then. The financial losses have significantly increased over time. Banks introduced digital methods of transactions but cybercriminals have figured out a way to fulfill their malicious intent here too.
Norton’s report on cybersecurity estimated that cybercriminals stole £130 billion in 2017 from the consumers along with £4.6 billion from British internet users. Identity theft, account takeover fraud, and catfishing are some of the common scams that are continuously increasing. Apart from these few scams, phishing attacks are also on the rise. It may come to you as a surprise, but phishing is the deadliest threat of all for any business and the most successful one too. Want to know more about phishing? Keep reading to find out.
What is a Phishing Attack?
Also called a social engineering attack, phishing is often used to steal data that may include login credentials to a social media account or bank account information. The cybercriminal appears as a credible source and sends emails that encourage the victim to click on the link or instant message.
This link is the main issue. Once clicked, victims are redirected to a different website that seems legitimate but it’s a trap. The new website will ask for sensitive information like your personal information, social media credentials, or bank account information. If any of your employees provide such information, your customers’ information can be accessed and used for illegal gains.
The link you clicked may include a virus that can install malware or ransomware software that can threaten your business later. A report from Keepnet Labs estimated that only 3 per cent of the employees report phishing attacks to the management. Have you ever wondered about the number of phishing emails your employees might have ignored?
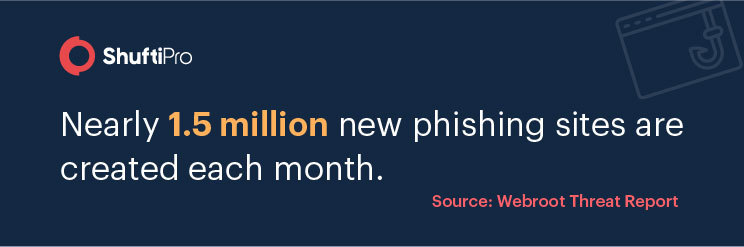
Types of Phishing Attacks
With time, cybercriminals have also developed different kinds of phishing attacks that fit their needs. Every type has its consequences for companies. Here are some of the common kinds of phishing attacks that you must know about.
Business Email Compromise (BEC)
Your middle-level management or first-line managers will receive information that says that you (or anyone from the higher management like CFO) is contacting due to some inconveniences. The email will show a high level of credibility with compelling statements. Some of the common reasons in such emails are:
- Issues related to tax
- Demotion or promotion matters
- Security issues in the company
Employees generally panic about issues like these and respond to emails. The message may ask for your company’s information and official bank account details. Your company’s information can be used for creating a fake bank account that can be used for money laundering or the information will be acquired for data breach later.

Whaling
The CEO, CFO, CTO, and other top-level managers are also unsafe nowadays. Whaling is another type of phishing attack that targets senior management. Since the targets are highly sophisticated, the emails are extremely sophisticated as well so that they can’t be traced. Maybe you receive an email from the central bank of the state saying that your firm was involved in money laundering and you have to pay a hefty fine to clear your name along with the company’s information.
Spear Attacks
These attacks are sometimes targeted to individuals – employees of the firm, and the majority of the time firms are the target. The sender uses personal information or appears as a legitimate company to get in touch. Winning your trust gets simpler this way and you can get a link that redirects you to a website for further information. On the other hand, you may be asked to reply to the email with sensitive information. In either case, you are being tricked into sharing confidential information.
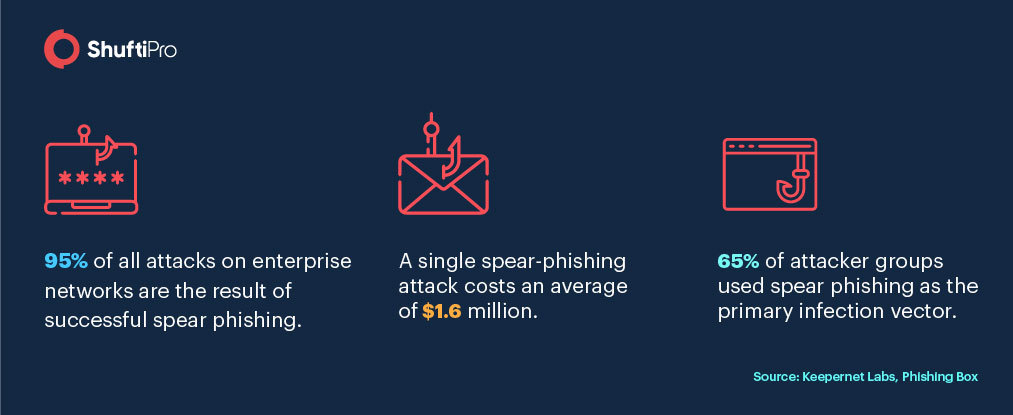
How to Spot a Phishing Attack?
Some tips and tricks can always save your business from any phishing attacks. There is a cyberattack every 39 seconds and half of them are attempted through emails. So, you cannot stop the attacks but you can spot them on time to stay safe. Here are some hacks for identifying a phishing attack.
Invalid Links
Always check for the validity of the link shared in the mail. No matter how hard a cybercriminal tries, it is impossible to get a legitimate domain and use it for illegal purposes. Search engines have restricted such actions. If you take a closer look at the links, the search engine will indicate a ‘not secure’ tab with such links. Moreover, the link shared in the email will never match with the one displayed in the search tab of the search engine.
Demand for Personal Information
Fraudsters often ask for personal information in the email so that they can use it for identity theft and synthetic identity fraud. Do not share any of the person or company’s information over the mail, especially if the source is unknown.
Learn more about identity theft: 5 types of identity theft fraud and How businesses can prevent it?
Technical Issues
Since you are receiving emails for compromising corporate information, you can check for technical mistakes. Spelling and grammar issues in statements along with the spelling of the names are not hard to identify. For instance, your CEO’s name on official documents is spelled as ‘Sarah’ but in the email, it is spelled ‘Sara.’ It may be a phishing attack and you can confirm the email before communicating further.
Tone of the Email
It is natural that your tone changes with the type of email and the motive of scam emails are to threaten victims for acquiring information. Always sense the tone of the email. Your employees will never order you or threaten you, so if the email from a ‘subordinate’ says that the ‘company’s domain has been suspended’, be sure to cross-verify the information before responding.
How Can Two-Factor Authentication Help?
Protecting your business is essential no matter what, and phishing attacks are the worst of all the cybercrimes. They can easily trick you or your employees into sharing confidential information. How to secure the firm is still an unanswered question. Nevertheless, you have two-factor authentication to make emails secure, be it your personal email or business email.
2FA is two-step verification in which one step is very common and everyone is obligated to do it. Setting a complex password is what we are talking about. Passwords are a combination of upper and lower case alphabets along with numbers and special characters. The second step is a verification code that is shared on your mobile number or recovery email registered.
The cybersecurity department of your company can enable two-factor authentication for all the emails of the business. If any of the credentials have been compromised, 2FA will not give access to the fraudster. How? A code is sent to the registered phone number (ideally, this must be your company’s number) and without verifying this code, no one can access the emails.
Read more: Why 2 Factor Authentication is vital for Online Identity Risk Management?
To Sum Up
Cybercriminals have become more sophisticated than ever and there is a dire need for enhanced security measures for companies. Confidential information through emails has often compromised that accounts for a significant part of data breach every year. Business Email Compromise (BEC), smishing, and whaling are some of the common types of phishing attacks that every company experiences. There are 2244 cyber attacks every day, which means your business is also attacked almost every day. You can protect your business accounts with two-factor authentication and ensure the security of all the employees.
Get more information about two-factor authentication from our experts.

 Explore Now
Explore Now













