Prevailing Identity Fraud in Telecom Sector – How Shufti Can Reduce the Risks

The telecommunication industry holds significance for the information sector as it is primary infrastructure for communication through phones, cables, and the internet. Emerging technologies and increased digitization have skyrocketed the risks of cyberattacks on telecom industry, eventually leading to identity theft and other financial crimes. Fraudsters use a myriad of ways to exploit the system, including spoofing, phishing, robocalling, and account takeover.
Users have to input their details before using any telecom services, resulting in a large number of data shared on the internet. Identity theft has become the most common scam in the telecom sector, increasing other crimes, particularly money laundering, account takeovers, and account opening fraud. Fraud in telecommunication industry is rising at an annual rate of 20% to 30%, highlighting the need for robust identity verification measures.
Telecommunication Industry – A Highly Vulnerable Sector
Unlike many other sectors like banks, insurance companies, and real estate, telecommunication industry has not implemented stringent measures to curb fraud, resulting in multiple scams. Criminals steal the identities of users through several means and further use sensitive data to carry out various crimes. Identity fraud has adopted the form of a huge threat to overall digital system and is termed a global security concern by Financial Action Task Force (FATF).
The number of mobile phone users is around 7 billion in 2022, making telecom sector highly vulnerable to identity fraud and other monetary crimes. All the global financial watchdogs and major jurisdictions are working tirelessly to implement a strict system of identity verification in telecom sector to eliminate bad actors. Telecommunication Service Providers (TSPs) should regularize the industry by incorporating Know Your Customer (KYC) measures, including biometric verification, facial recognition, and document authentication.
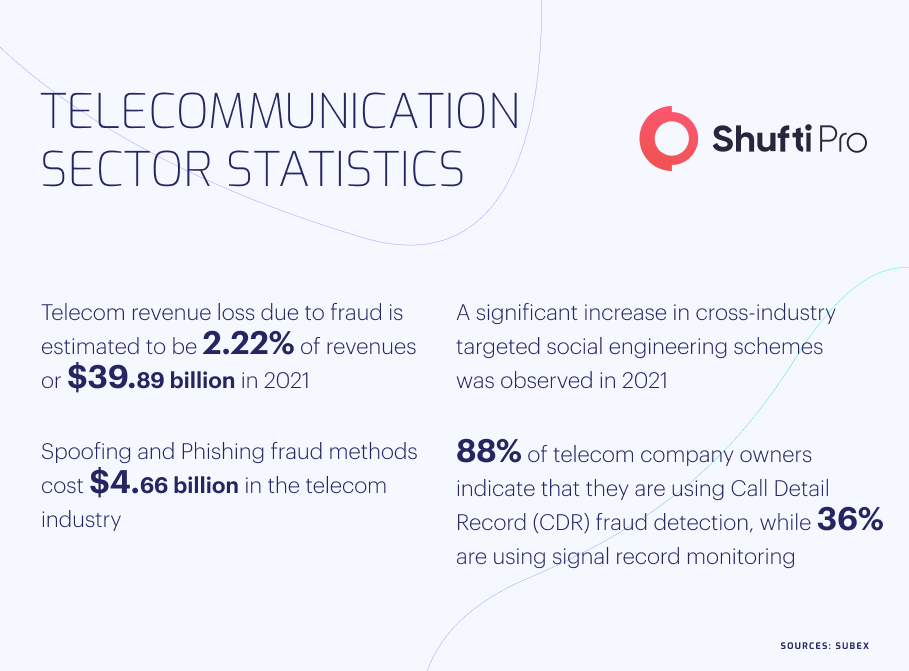
High Profile Cases in Telecom Sector
Sim swapping, subscription fraud, CLI manipulation, and robocalling are some of the major scams encountered by telecommunication service users. Due to legislation by several countries against telecom fraud, many cases have surfaced in the recent past and criminals have been penalized. Identity theft, money laundering, and other financial scams are a huge threat to overall digital system, which should be monitored through effective KYC solutions.
Telecom Firm in UK Hit by Identity Theft
The UK-based telecom company has been targeted by scammers resulting in identity loss of a large number of users. The owner has complained that scammers are blackmailing company and providing fake one-star reviews on their services.
The CEO of company has further stated that a complaint has been registered against scammers to Google, but no strict action has been taken yet. It has been termed by Google that investigations are going on and criminals will be penalized as per the regulations.
Aussie Telco KYC Failures Prompt Large Fine
Australian Communication and Media Authority (ACMA) has penalized a telco company that was providing phone lines to the users without verifying their true identities. ACMA has further termed that company remained unable to comply with the KYC regulations and provided services without following identity verification standards. The company has also admitted to not fulfilling the security checks recommended by regulatory authorities.
ACMA has imposed a fine of AUD199,800 and also asked the company owners to compensate all the users who suffered due to fraudulent activities by unidentified users. ACMA emphasized the importance of protecting customers from all such scams and instructed all telecom companies to ensure KYC compliance.
Global Regulatory Authorities Monitoring Telecommunication Industry
In the wake of prevailing identity fraud and financial scams, global authorities have taken a strict stance against prevalent crimes in telecommunication sector. FATF, Interpol, and many countries have legislated stringent laws to incorporate identity verification measures in telecom companies.
Canada
Canada’s Anti-Spam Legislation (CASL) is the primary body responsible for monitoring scams in telecommunication sector. It has committed to reduce the harmful effects of spam and related threat. CASL is working along with Canada’s Competition Bureau and the Office of Privacy Commissioner, to eradicate chances of fraudulent activities in telecom sector.
It has taken a strict stance against the violators and set administrative monetary penalties for criminals. In multiple cases, several fraudsters have been penalized with imprisonment and fines for violating rules of state.
Sweden
Electronic Communications Act (ECA) is monitoring the whole telecommunication industry in Sweden by implementing identity verification measures for companies. ECA has termed the telco sector as highly vulnerable to identity theft, phishing, and other financial scams. Authorities have issued a road map to penalize all the bad actors exploiting the telecom industry.
Singapore
The Infocommunications and Media Regulator (IMDA) is primary regulatory body overlooking the telecommunication industry in Singapore. Due to increasing crimes, IMDA revised existing laws in May 2022 and implemented more strict measures to curb financial crimes. IMDA has issued detailed guidelines for telecom companies to enforce identity verification measures before onboarding new users. It further proposes penalties to culprits in case of violations in the form of imprisonment and fines.
The Need of Identity Verification Measures for the Telecom Sector
Compared to 2019, fraud losses increased by 28% or $11.6 billion in 2021, highlighting the need for robust identity verification measures. Several sectors, particularly banks and insurance companies, have controlled the crime ratio by implementing several KYC measures, including facial recognition, and document verification. The Telecom industry is inevitable for digital operations, and it is need of the hour to regulate it by incorporating strict verification checks.
Not only identity theft but criminals are also carrying out money laundering using telco companies, raising the need for AML measures. Although it will be a gruesome task for Telecom Service Providers (TSPs) to regulate the whole sector, there is no feasible option than incorporating KYC and AML checks. The governments of several countries are already working to eradicate financial scams from mobile operator companies which must be accompanied by TSPs.
How Shufti Can Help?
Shufti’s state-of-the-art identity verification services are a feasible option for telecommunication companies. IDV services include; facial recognition, document verification, and biometric authentication, which are essential for an ideal KYC. Shufti’s KYC solutions are powered by thousands of AI algorithms verifying true identities of users before getting them on board.
Anti-Money Laundering (AML) screening solution by Shufti has access to 1700+ global sanctions lists and screens users’ data against them to keep bad actors away from the system. It provides output in less than a second with an accuracy of 98.67%.
Want to know more about identity verification and anti-money laundering solution for the telecommunication sector?

 Explore Now
Explore Now













