Shell Companies and Money Laundering: How to Combat Them?

Shell companies are notorious for all the right reasons. These entities often called ghost companies are frequently used by fraudsters to launder black money. Shell companies are business entities without any actual premises, employees, or operational assets. They are created by registered agents to conceal ownership information from other businesses. This gives them the anonymity to hide ill-gained funds, avoid tax payments, and bypass AML regulations.
When it comes to developing B2B relationships, businesses should keep a vigilant eye on their partner entities. Verifying important details like corporate documents and addresses can save honest entities from associating unwanted ties with fraudulent companies. Business Verification, referred to as Know Your Business (KYB), and Anti Money Laundering practices help address this problem by taking down shell companies registered only on papers.
This blog describes how shell companies are used in money laundering, what role global authorities have played in preventing them, and how it can help enterprises in the long run.
How do Shell Companies Launder Money?
Shell companies usually claim cash transactions on behalf of their customers to launder money. Multiple transactions increase anonymity and reduce the chances of tracing the original recipient. Money launderers then deposit funds into the company that are transferred to the criminal’s account by creating false invoices.
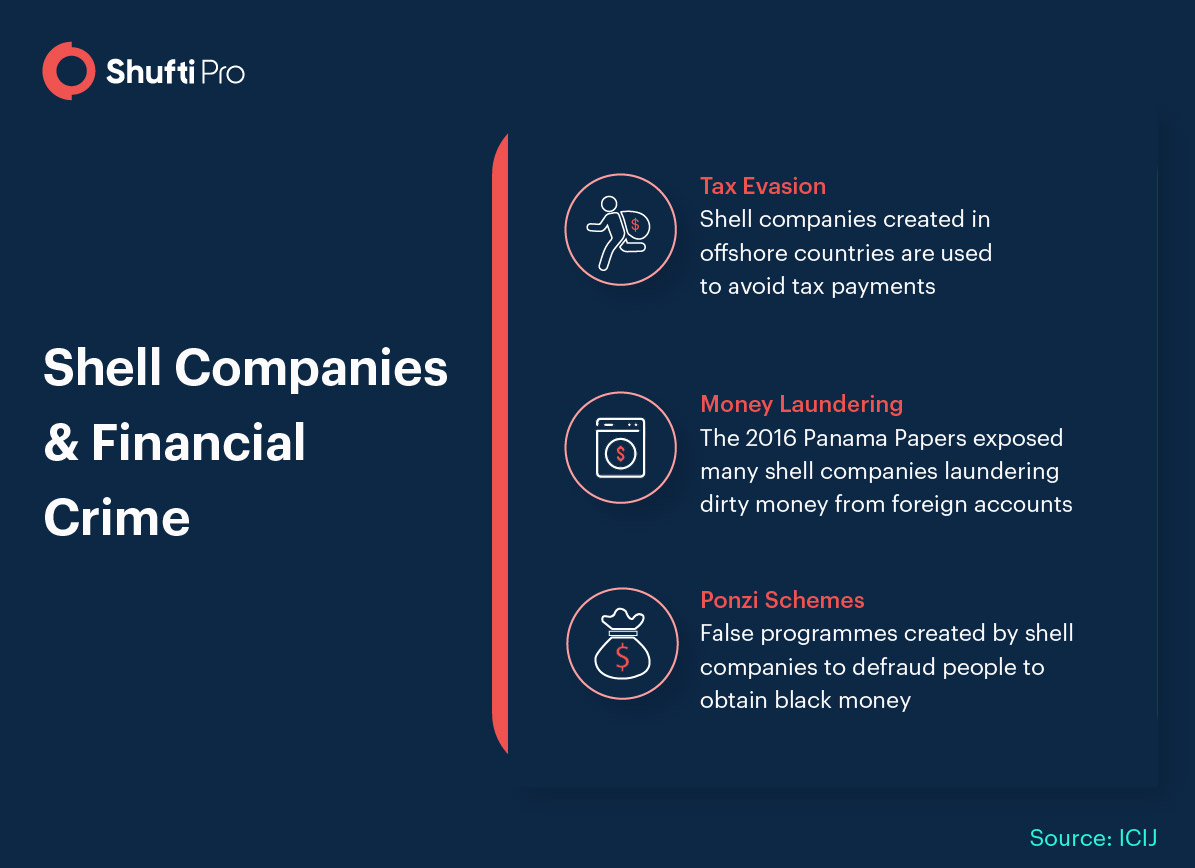
Global Efforts – Crackdown of Shell Companies
Global regulators and financial authorities have played an active role in the fight against fraudulent companies hiding their identity. In order to combat financial crime through shell companies, some efforts made by law enforcement departments are listed below:
Corporate Transparency Act (CTA) – USA
According to guidelines stated in the Corporate Transparency Act, businesses operating in the United States have to provide FinCEN – Financial Crimes Enforcement Network – with the information regarding the beneficial ownership of their company. This law was introduced in 2019 to prohibit all anonymous shell companies run by criminals for money laundering and illegal proceeds. The Transparency Act defines beneficial owners as someone:
- Having a 25% or more share in the company’s revenue
- Is responsible for controlling the business entity
- Who Receives benefits from the business’ assets
Person with Significant Control (PSC) – UK
Authorities under the UK government define beneficial owners as PSC – a Person with Significant Control. As per the laws, a person is not allowed to run a business if they fail to record details about a company’s PSC during incorporation. Below are identifiers that help identify PSCs, according to the UK:
- An individual with more than 25% of the company shares
- A significant authority (more than 25% voting rights) in the company
- An administrator having the right to appoint and remove executive officials
With the PSC reform in place, companies in the UK need to disclose “beneficial ownership” information which will help identify shell companies helping money mules launder dirty money. The PSC registry, having all the essential company information, stops fraudsters from obscuring their identity behind these illegitimate entities.
Combat Shell Companies with…
Business Verification
Business verification often termed as Know Your Business (KYB) is a corporate due diligence process which a business performs to verify other partner entities. It enables enterprises to devise policies and procedures to detect suspicious activities and prevent money laundering. With KYB checks, corporations can make sure they are conducting business with real and legitimate entities, and not another shell company.
KYB verification for corporate entities also helps them comply with the CTA, and Anti Money Laundering directives by the EU. By cross-checking against business filings, networks, and financial statements of a company, an automated business verification allows an enterprise to stay AML compliant.
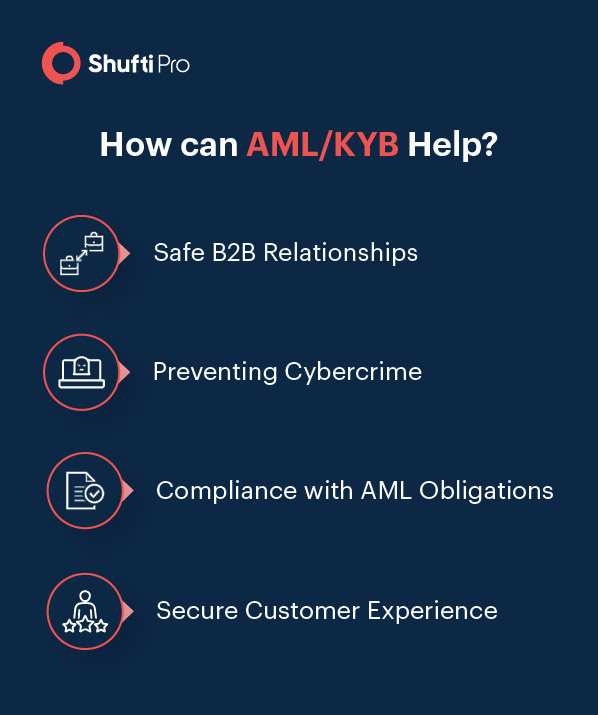
Risk-based AML Program
Business entities are required to comply with recommendations of the FATF and other global regulations to prevent money laundering. An AML compliance program based on proper risk assessment for customers and partner entities can address the regulatory requirements. These programs help identify the risk associated with shell companies that are frequently involved in financial crime.
What Should the Program Include?
When it comes to onboarding business associates, a company’s AML program should focus on Ultimate Beneficial Ownership (UBO), nature and amount of transactions and business activities. The compliance officer should connect data points to verify the stakeholders and transactional flow of the company.
Red Flags
Below are some red flags which a risk-based AML program should consider when verifying corporate entities:
- Is there any difficulty in obtaining ownership information about the company?
- Do the company’s transactions align with its business profile?
- Any payments listed without a proper purpose or date
- Transactions involving large sums of money with other shell companies
- The company performs frequent transfers to multiple beneficiaries
Watch list Screening
Beneficiaries of shell companies are often placed on adverse media lists due to the amount of risk they pose to a business. This can cause a customer’s risk profile to change allowing firms to conduct additional screening of these users. Politically Exposed Persons (PEPs) list includes individuals with a higher AML risk. Ongoing monitoring of PEP status can help enterprises to identify and take down potential financial crime.
Ongoing Transaction Monitoring
The red flags defined in the AML program can help corporations identify companies offering illicit services. Shell companies often involve unusual transaction patterns which could be detected through a transaction monitoring solution. Ongoing AML monitoring of corporate entities also helps identify high-risk companies which could possibly be involved in money laundering and other cybercrime.
Address Verification
Verifying a corporation’s address can help businesses find out if it’s a shell company or not. Since these entities only exist on paper and do not have any physical premises or personnel, they are easy to spot. An address verification solution powered by artificial intelligence can quickly check for possible hidden information including addresses and corporation dates to identify ghost entities operating for illicit purposes.
To Sum It Up …
Although shell companies are not always created with an ill intention, their ability to hide ownership identity makes them suspicious. Fraudsters exploit this aspect to their benefit for cleaning money acquired from illegitimate gains. While regulators across the globe continue to implement Anti Money Laundering laws, corporate entities are faced with compliance obligations. A robust mechanism for AML compliance to verify and monitor business associates can help enterprises achieve the all-important trust in a B2B relationship.

 Explore Now
Explore Now













