CFT & AML Compliance To Hold Back Financial Crimes

In this digital era, many factors are greasing the wheel of money laundering. Due to online transactions, it has become a piece of cake for fraudsters to carry out their financial frauds. But the AML Compliance Program for business is to govern the monitoring of accounts, detection, and reporting of financial crimes to relevant authorities. CFT and AML compliance promote stability in financial markets by mitigating the adverse effects of criminal economic activities and promote stability in financial markets.
In this digital era, many factors are greasing the wheel of money laundering. Due to online transactions, it has become a piece of cake for fraudsters to carry out their financial frauds. But the AML Compliance Program for business is to govern the monitoring of accounts, detection, and reporting of financial crimes to relevant authorities. CFT and AML compliance promote stability in financial markets by mitigating the adverse effects of criminal economic activities and promote stability in financial markets.
AML compliance trace and tackle the frauds like money laundering that any financial institute can face. Customer screening against certain PEP lists and sanction lists is done to complete due diligence and deter money laundering, terrorist funding, drug trafficking and other financial frauds. Anti money laundering checks provide a backbone for CFT (combating the financing of terrorism) and KYC regulations. AML regulations are key components of the US Patriot Act, 2001. In 2005 the Reserve Bank of India made it compulsory for banks across the globe to adhere to AML compliance to detect and prevent the financing of illegal activities.
Financial Regulations for Money Laundering- A Deep Dive:
The Financial Action Task Force, which is a group of 35 countries, work together to curb the risk of financing of terrorism by standardizing regulations to prevent such frauds. These authorities are working to keep a close check on money laundering activities. Many countries are following the guidelines of FATF to impede financial crimes and to restrict terrorist financing and money laundering. There are 40 recommendations of the FATF to put a halt on money laundering which countries follow. The FATF Recommendations are recognized by the global AML and CFT standards. The list of data sets of citizens that is being continuously updated is provided to law enforcement agencies in case any illegal activity is performed by any individual.
What is Combating the Financing of Terrorism?
CFT which is also called Counterfinancing of Terrorism is the process that involves investigation and analysis of sources that are used in the funding of various activities to gain political, religious, or ideological goals. By continuously monitoring transactions and by tracking down the source of the funds that support terrorist activities such activities can be prevented from occurring.
Key Features of CFT:
CFT is achieved by having a proper channel for AML checks. Following are some key features of how CFT works:
- CFT is basically restricting the movement of funding of terrorist organizations. By focusing on a variety of entities, including banks, charities, and businesses by regulation, supervision, and reporting.
- The efforts which are made to authenticate and put a halt on the movement of money and to monitor transactions to screen out those which are used to fund terrorist activities come under the umbrella of CFT.
- The CFT process plays a significant role in identifying money laundering activities from detection to prosecution. Money laundering appears to be legitimate but processes like CFT are used to identify such criminal activities and eradicate them.
- Financial Intelligence Units investigate suspicious transactions and information is provided to law enforcement for further investigation or prosecution.
How Combating the Financing of Terrorism Works?
CFT involves guiding and teaching financial investigative techniques and training financial institutes to identify suspicious activities. CFT efforts may examine entities including charities, registered money service businesses, underground banking entities with many others. Money launderers need to conceal the origin and how the money will be used in order to carry out their activities. Such frauds come from legal sources such as legitimate organizations as well as from illegal sources such as drug trafficking and government corruption. Terrorism financing and money laundering, both are interconnected. When an entity is able to detect money laundering activities, it is preventing terrorist funding simultaneously so combating money laundering is a key to CFT.
AML Compliance for Businesses
AML (Anti Money Laundering) practices are used to perform due diligence of customers. Businesses, especially financial institutes need to abide by AML checks to deny the loss of millions in penalties that will be imposed by regulatory authorities for not complying with the regulations. To analyze customer data and to detect suspicious activities financial institutes deploy stringent AML checks. Such checks filter out customer data and classify it accordingto the suspicion level so that high risk customers can be highlighted. Any sudden and abrupt increase in money transfer or large withdrawal should be considered suspicious and businesses should act accordingly. AML checks help financial institutes to impede financial frauds. AML screening detects not only money laundering but also other financial frauds like tax evasion, terrorist financing can also be traced and eradicated.
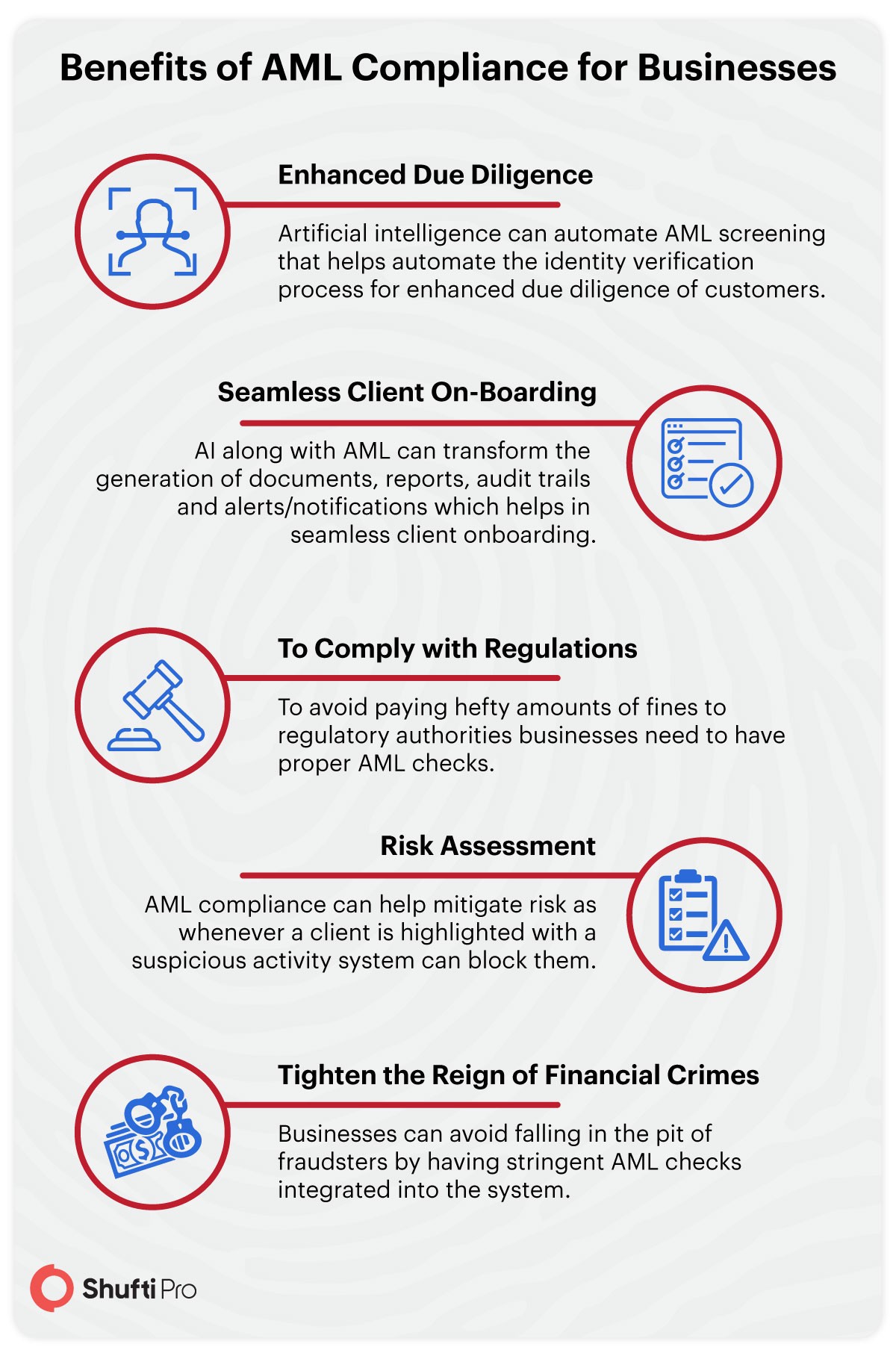
PEP List Screening- An Integral Part of AML & CFT:
A politically exposed person or PEP is the one who has a high profile role in society. Due to this prominent position that they hold in society they can commit money laundering and other offences. Many case studies and analysis reports have confirmed this fact already. There is a list available that holds all the names of PEPs known as the PEP list. Screening individuals against this list is an integral part of AML and CFT to identify the person. As these people are more likely to be involved in financial crimes so they come under the umbrella of high-risk for financial sectors. With PEP status additional risks which are involved can be highlighted. Businesses need to be more vigilant and must apply additional AML and CFT measures when dealing with such persons. In order to avoid reputational and regulatory damages, PEP list screening is an integral part of AML and CFT regulations.
Read More: Politically Exposed Person – An unsaid threat to Businesses
So in a nutshell, AML and CFT compliance are to eradicate financial crimes. Businesses need to abide by these regulations in order to be safe. If a business fails to comply with these regulations it will end up falling in the pit of money launderers and end up paying a hefty amount of fine which will be imposed by regulatory authorities. So in order to curb financial crimes and meet identity verification requirements businesses should have proper AML checks into their systems.
Find more relevant resources:


























![An Insight into AML Compliance in the Financial Sector [2022 Update] An Insight into AML Compliance in the Financial Sector [2022 Update]](https://shuftipro.com/wp-content/uploads/b-img-aml-comp.png)