Shufti’s Bug Bounty Programme: Strengthening Security Via Ethical Hacking

With the avalanche of security vulnerabilities in the verification industry, Shufti is launching its Bug Bounty programme in partnership with Bugcrowd. The company is inviting cybersecurity researchers and ethical hackers to track down any loopholes in its identity verification services and claim a bounty. Shufti is all set to start this programme as part of its promise to enhance security protocols and uncover the sophisticated tactics hackers use to bypass IDV systems.
Understanding Bug Bounty in Depth
A bug bounty is a monetary reward or compensation that is awarded for detecting any bugs, vulnerabilities, or weaknesses in the company’s security services. Bugs are usually in the form of security exploits and vulnerabilities; whilst they may also take the form of process issues or hardware flaws. In a Bug Bounty programme, all ethical hackers, bug bounty hunters, and cybersecurity researchers are invited not only to detect any vulnerability in security systems but also to report it to the concerned enterprise.
The ‘What’ and ‘Why’ of Shufti’s Partnership with Bugcrowd
Many organisations lack diversified skills and resources to detect any hidden vulnerability before hackers or cybercriminals do. Using reactive tools is not sufficient due to their low-impact results that overlook the emerging risks. Even those companies that use sophisticated technology can misjudge the patience, skills, and creativity of today’s attackers. This is where the Bug Bounty programme comes to the rescue.
-
What is Bugcrowd?
Organisations look for a proactive approach when it comes to cybersecurity and Bugcrowd is the most comprehensive and up-to-date security solution that orchestrates technology, data, and human intelligence to blind spots. Bugcrowd connects businesses and their applications to a crowd of security researchers to expose critical software vulnerabilities. The Bugcrowd Security Knowledge Platform lets businesses do everything possible to secure their organisation, customers, and reputation with products like Bug Bounty, Pentesting, and more.
-
Why is Shufti Partnering with Bugcrowd?
Shufti’s partnership with Bugcrowd aims to simulate a cyberattack on the company’s platform and deliver results so that it can offer fast, secure, and reliable IDV solutions. The company devised the Bug Bounty programme to show its commitment towards uplifting security standards whilst comprehending the sophisticated tactics cybercriminals use to defraud the IDV systems.
Through its Bug Bounty programme, Shufti is calling on all ethical hackers and cybersecurity researchers to expose hidden vulnerabilities in exchange for a monetary reward.
Thinking of how you can enter the field of Ethical Hacking?
Contact us at: [email protected]
Why is there a Need to Launch a Bug Bounty Programme?
The Bug Bounty programme helps companies enhance their security systems and builds and elevates trust in the digital age. Here’s how:
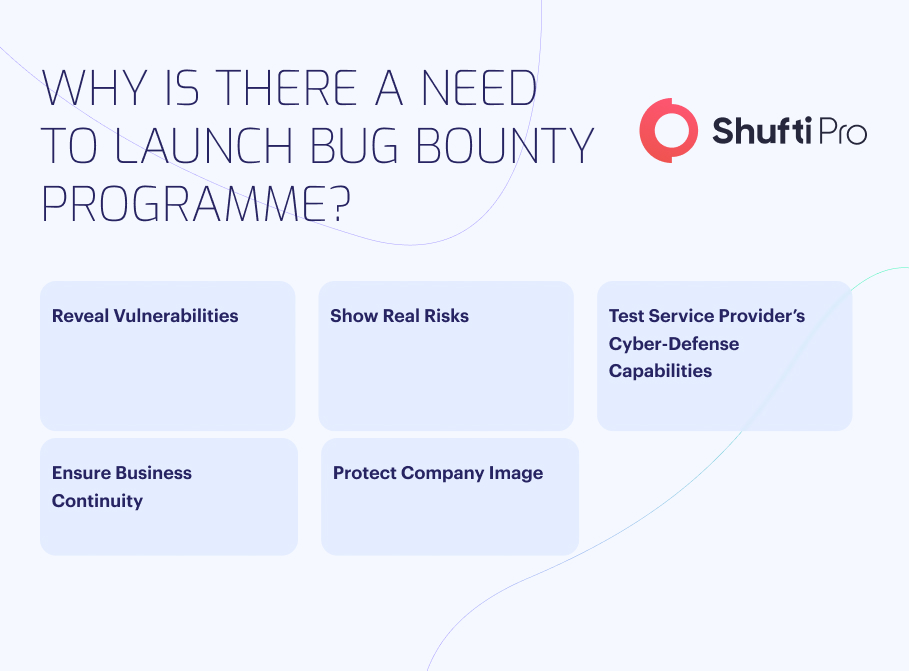
1. Reveal Vulnerabilities
The Bug Bounty programme and pentesting help security providers expose any existing weaknesses in their system and network infrastructure. It also helps to uncover the habits and actions of the workforce that can lead to cyberattacks and data breaches. At the end of the Bounty programme, a report is generated shedding light on the loopholes in the company’s security service or software to help it improve its system and enhance trust in the digital era.
2. Show Real Risks
With the Bug Bounty programme, businesses can pre-detect any real risk that a company may face in the event of a cyberattack. It shows how the hacker can access a company’s confidential information and perform commands of the operating system. The Bug Bounty programme lets firms know how vulnerable they are to any possible security exploitations.
3. Test Company’s Cyber-Defense Capabilities
Bug Bounty programme is a ray of hope for security solution providers as it helps them to detect an attack in time and respond to it promptly. Once the company is reported with any red flag, it starts investigations, discovers intruders, and mitigates the risk of a cyberattack on time. Not only this, but the programme also helps the experts test the efficacy of their protection strategy and what steps they need to take to boost their security strategy.
4. Ensure Business Continuity
A firm needs network availability, 24/7 communications, and access to resources to offer its customers a better service. Disruption in the company’s system puts a dent in the business’s reputation. With the help of the Bug Bounty programme, it can detect potential threats and ensure that the business does not encounter any downtime.
5. Protect Company Reputation
Protecting customer data is the top priority of any business as compromised client data can wreak havoc on a firm’s name and image. Through a Bug Bounty programme, firms can detect loopholes in their security solutions, thus preventing themselves from any potential cyberattacks and data breaches that can put their reputation at stake.
Are You Ready for the Chance to Win a Financial Reward?
The meaning of Bug Bounty is incomplete without knowing what this programme is all about. It is a lucrative win-win situation, both for the company that is launching it and the hacker who is attacking it. It provides businesses with the opportunity to mitigate cyberattacks and also provides them access to tens of thousands of skilled ethical hackers. Contrary to this, it’s alluring for cybercriminals as well. Besides offering financial rewards, the Bug Bounty programme helps attackers build their recognition.
Are you ready to enter Shufti’s Bug Bounty programme?